Protect against tomorrow’s attacks,
today Now!,
Cloud Security that secures “Build to Runtime”. Compliant with SOC2, STIG, PCI, HIPAA, CIS, MITRE, NIST, and more. One Platform that can do Agentless ASPM and CSPM, CWPP, KSPM, and KIEM. AI-LLM powered durable, reliable, and scalable CNAPP solution.
GET STARTED
Deploy Comprehensive CNAPP in Minutes
- CNAPP
- CWPP
- CSPM
- KSPM
- IoT/Edge
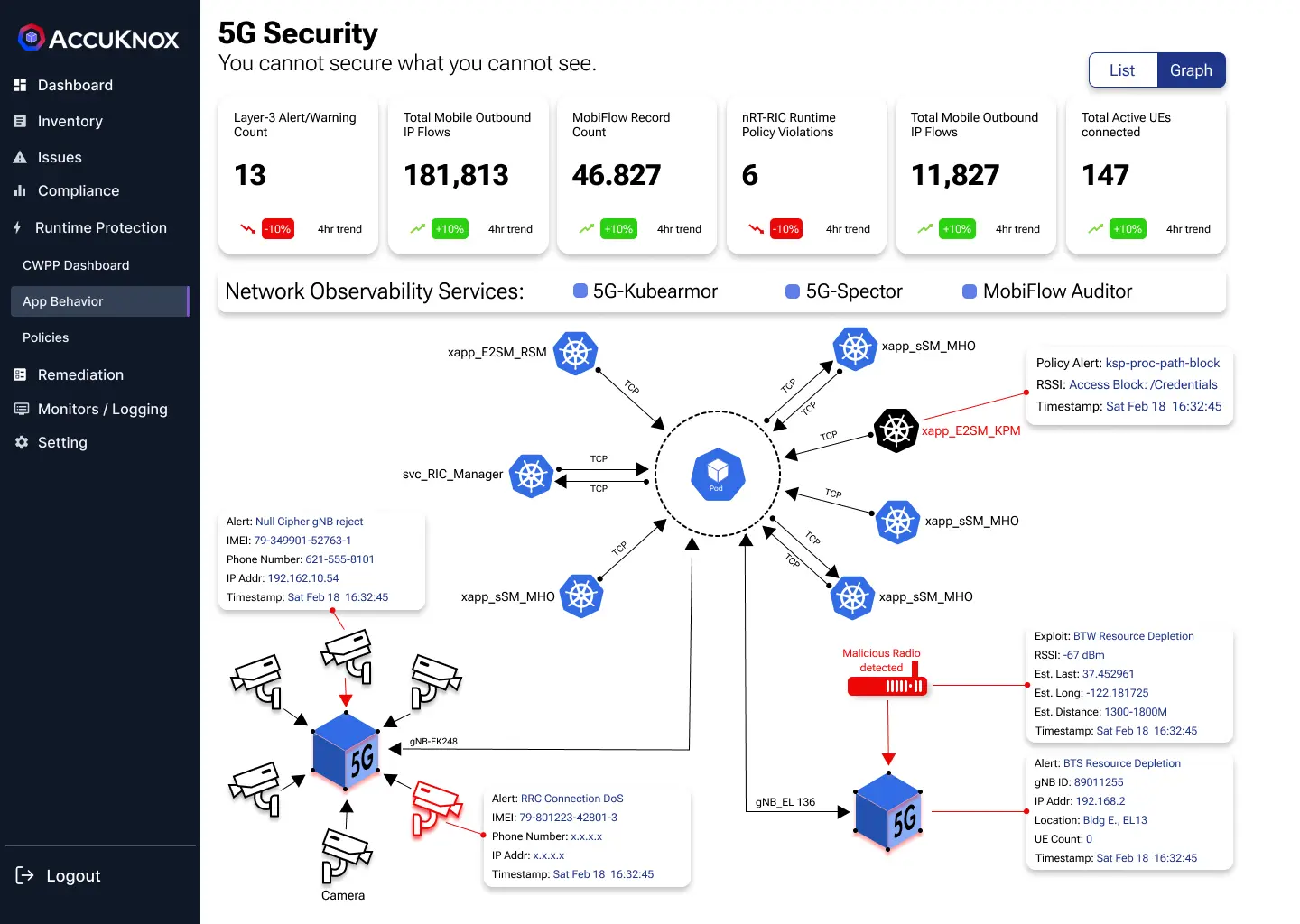
- 5G Security
- Comprehensive Multi-Cloud, Hybrid (Public, Private) Cloud Security
- DevSecOps model for CI/CD security, SaaS Model & On-Premises Model
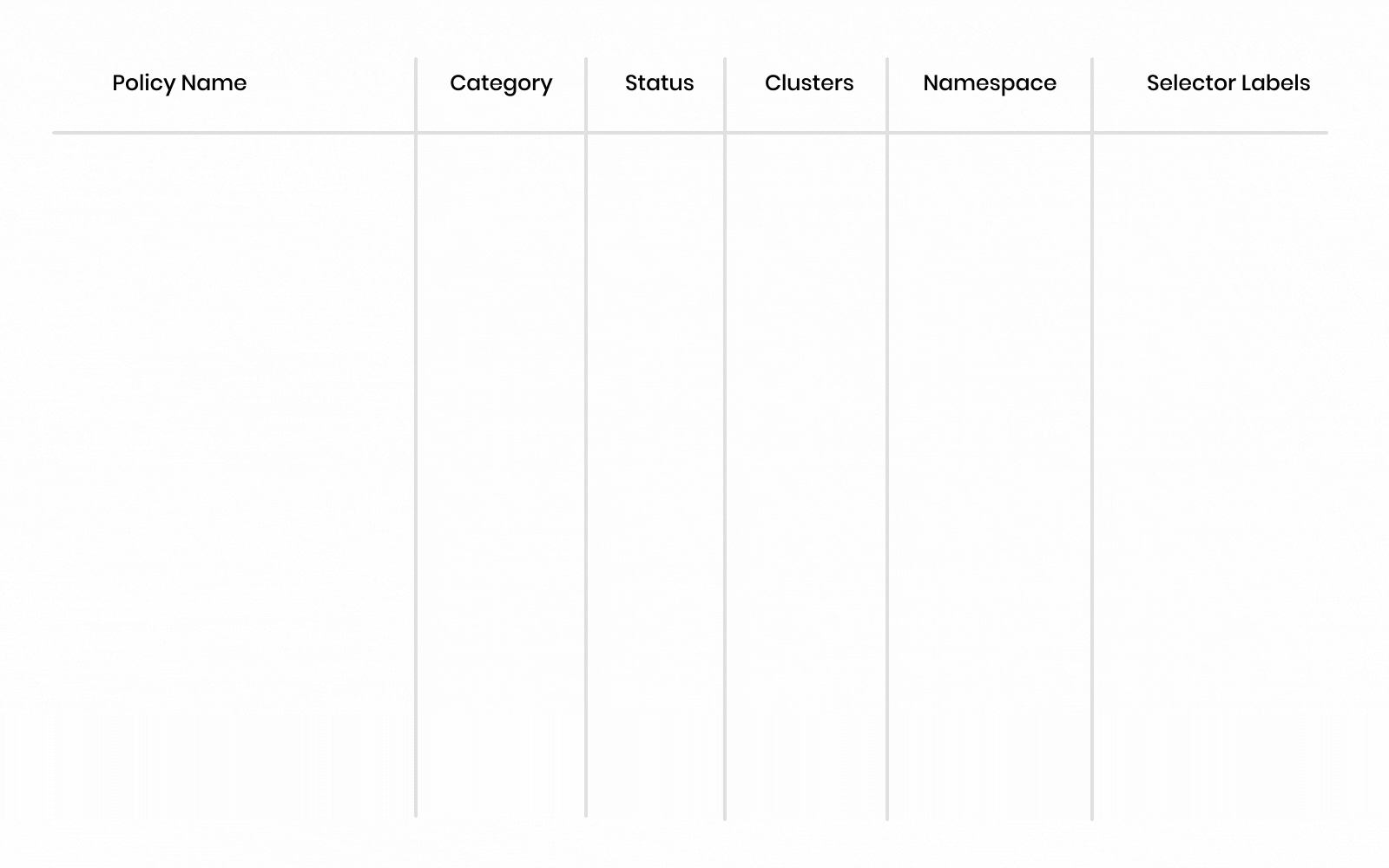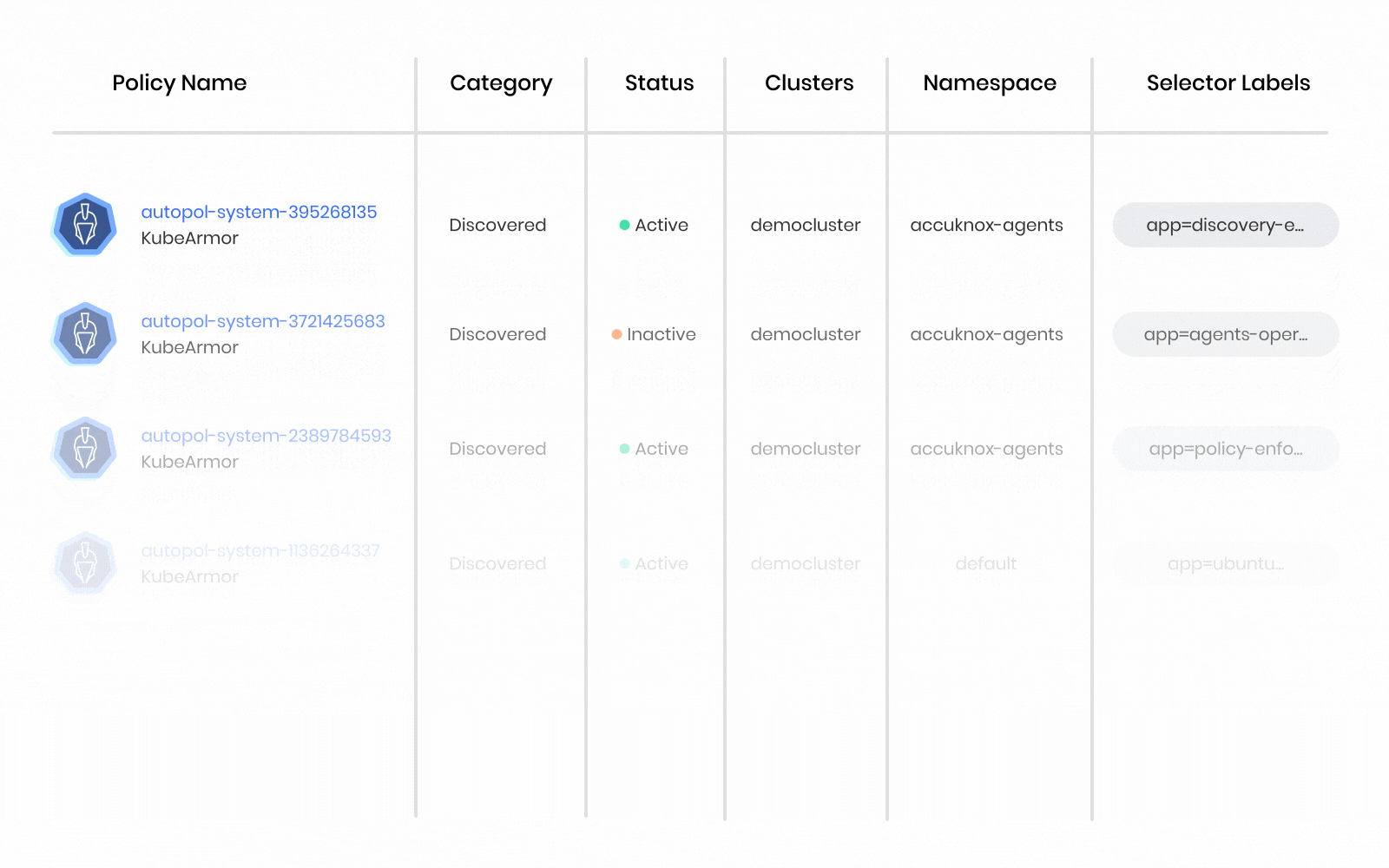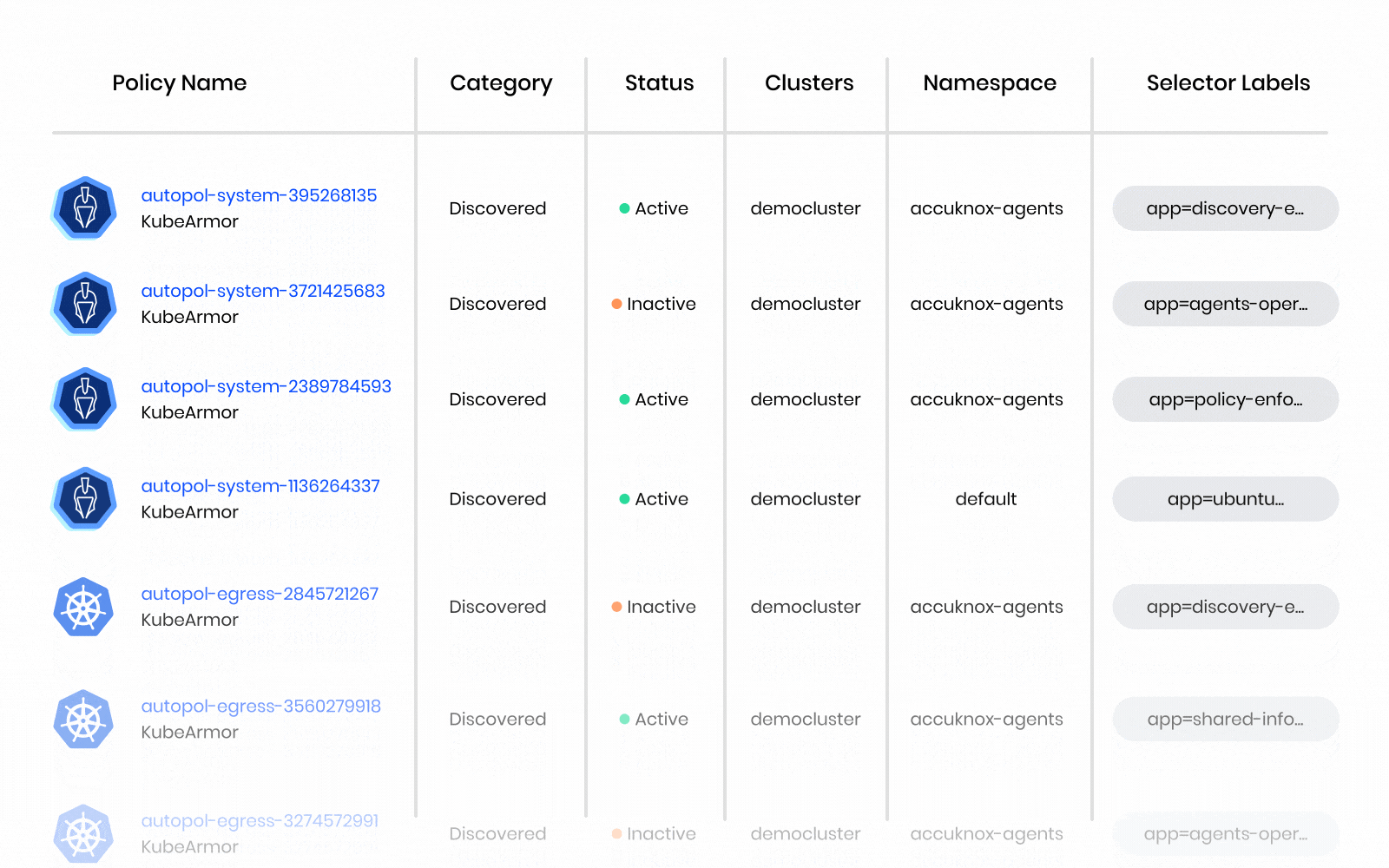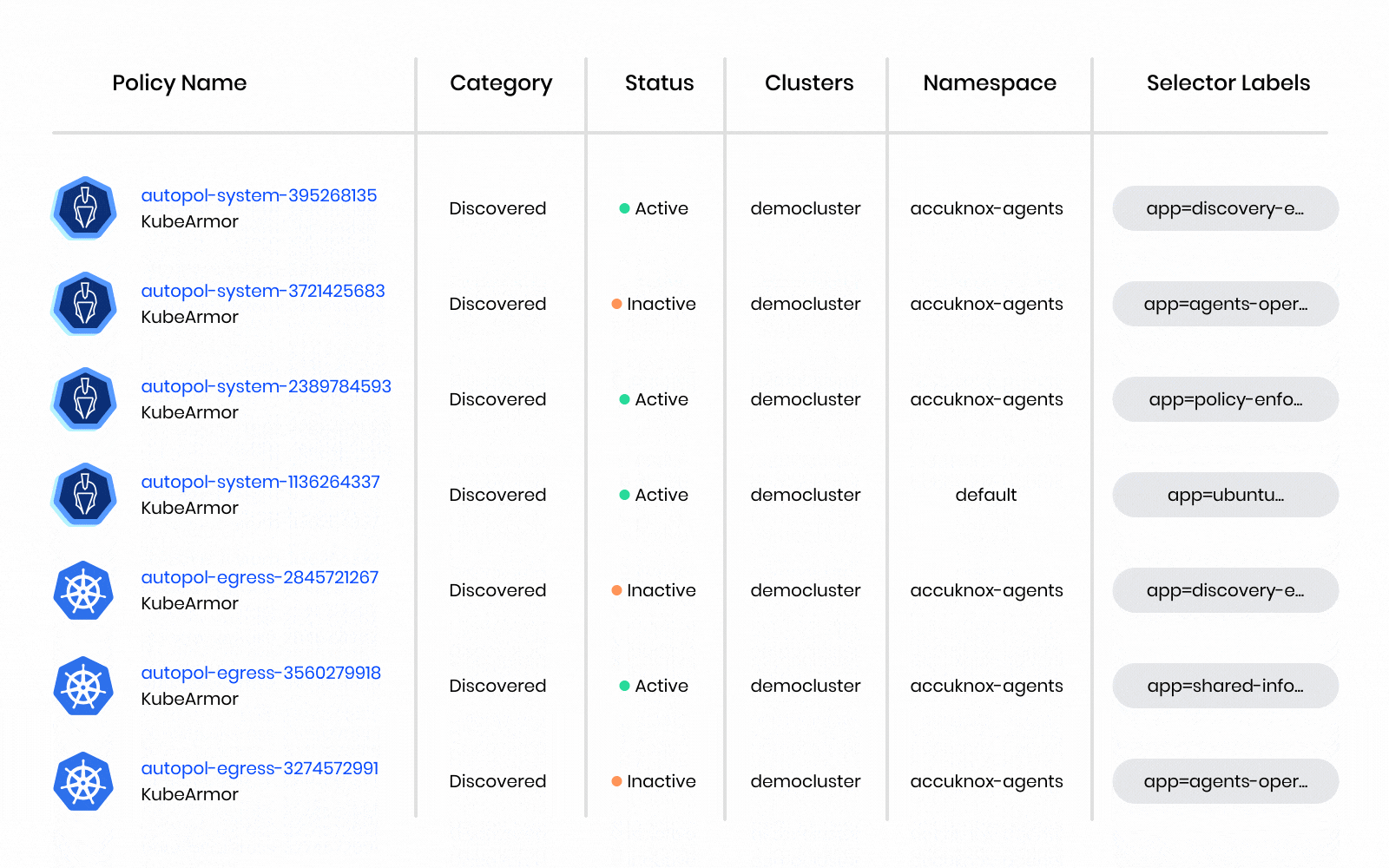
- Detailed Telemetry for Auditing & Container Forensics
- Integration with EDR, SIEM, AppSec, SOAR, etc.
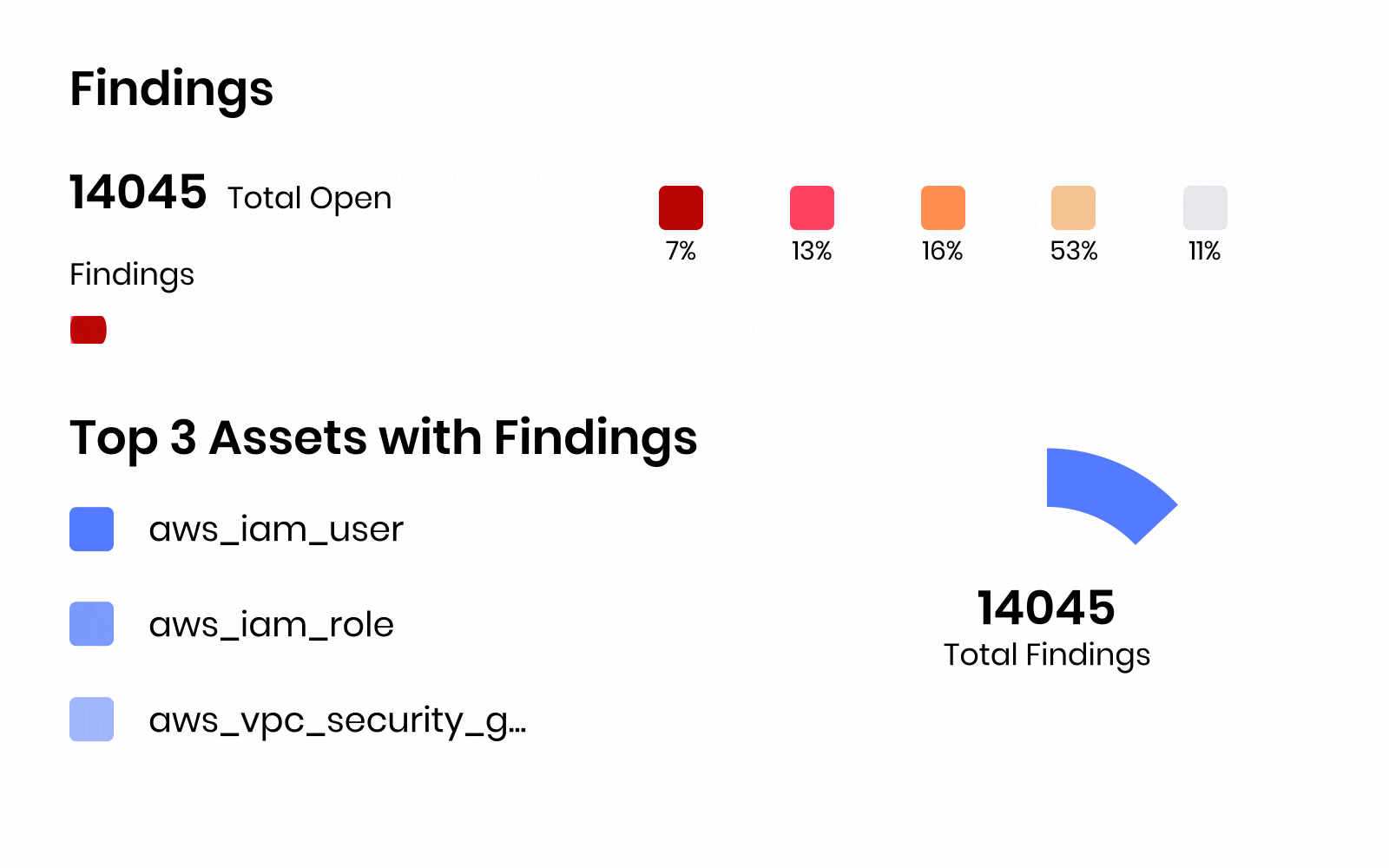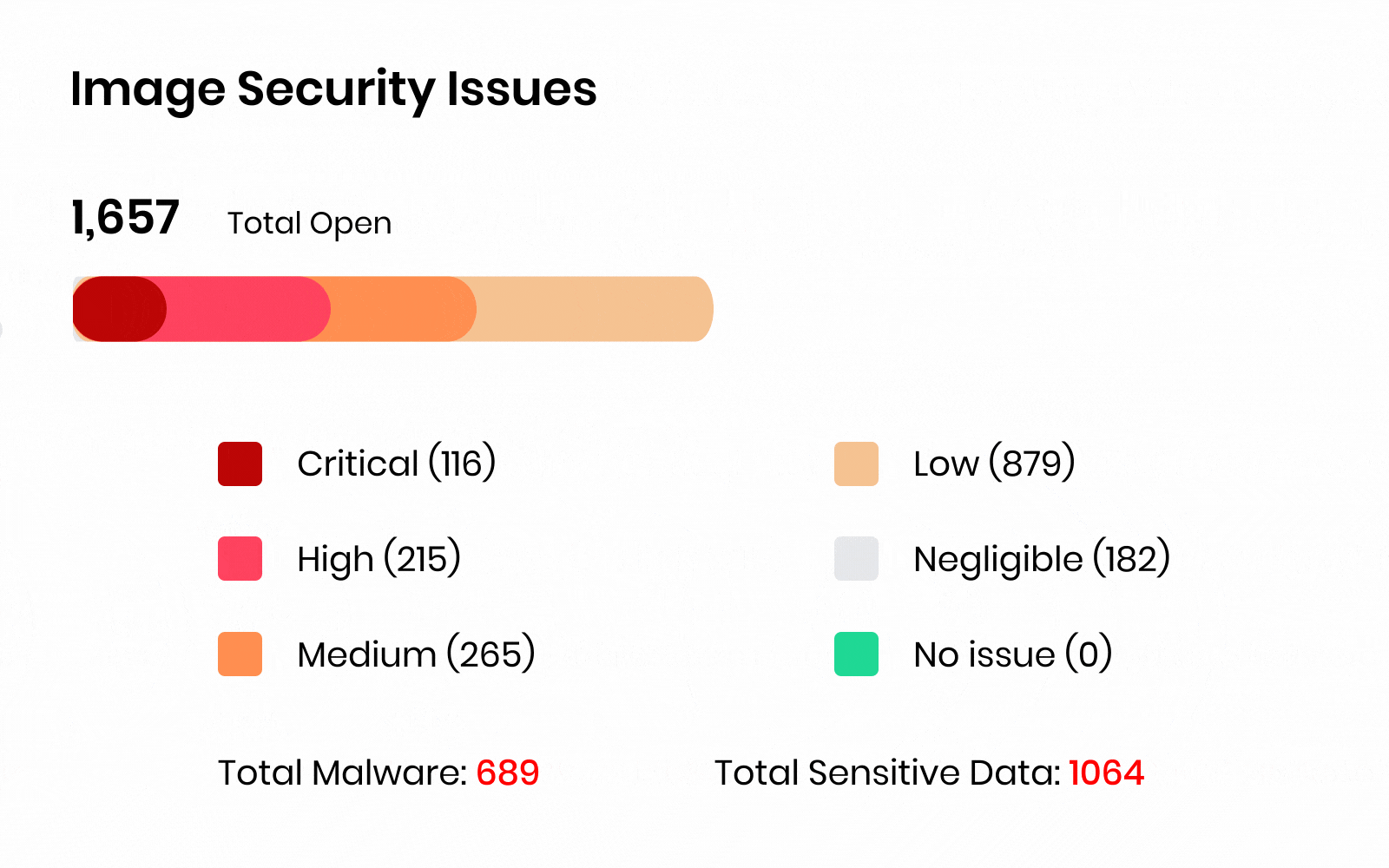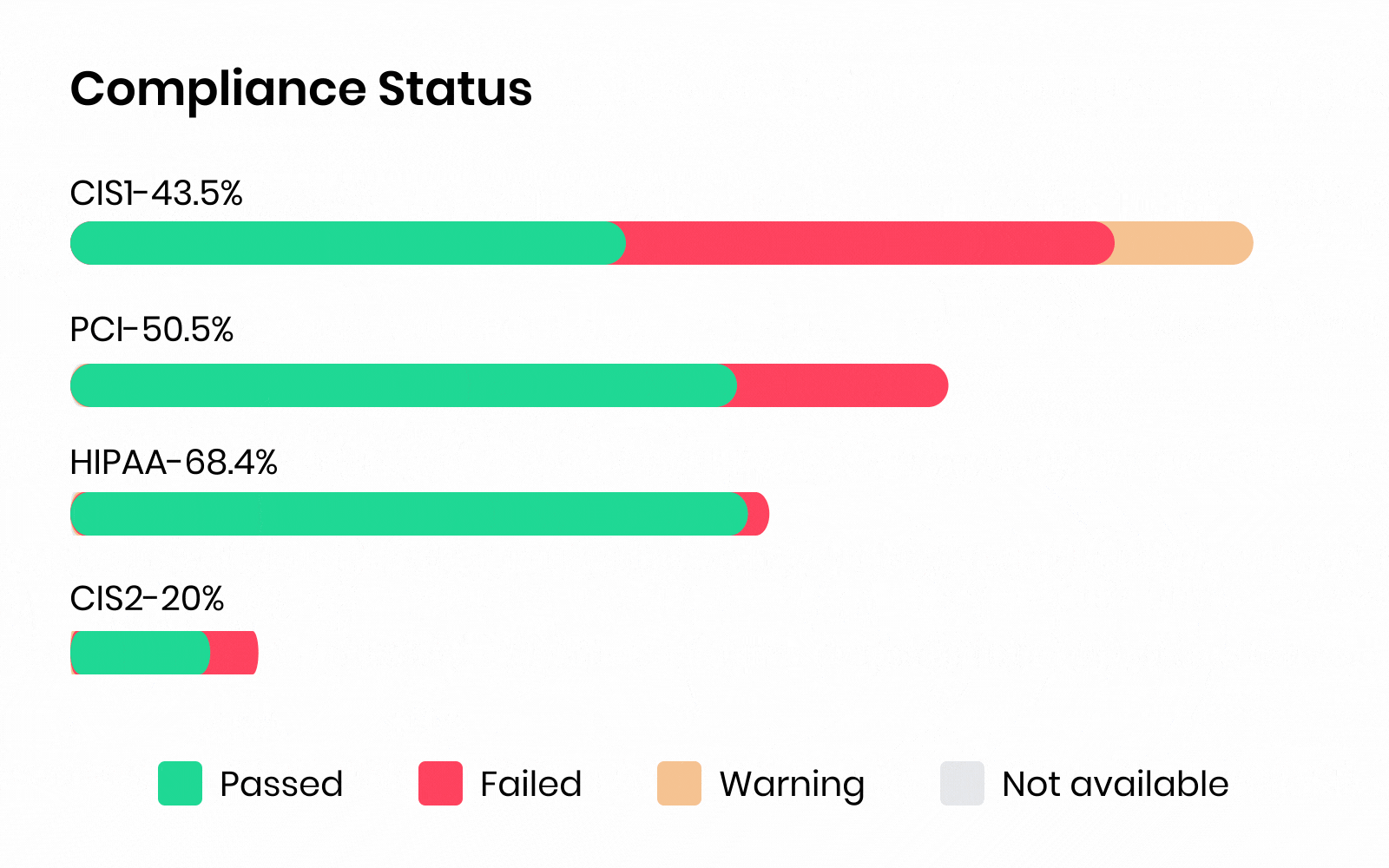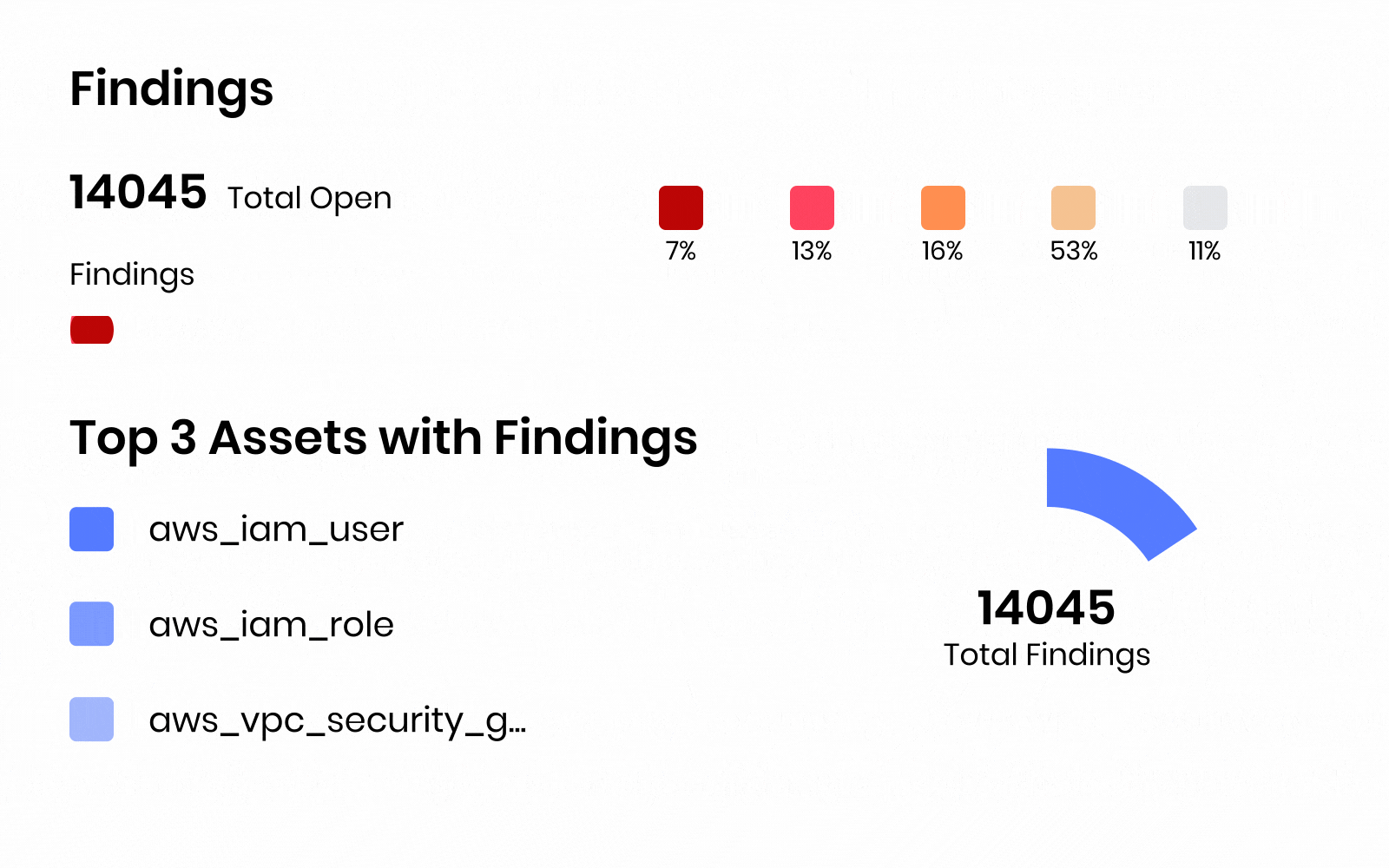
Zero Trust CNAPP that secures Build to Runtime
Advanced cloud-native security solution providing comprehensive protection from code to cloud, ensuring trust and integrity throughout your application lifecycle.
Yes, AccuKnox can integrate with
11+
Container Registries
3+
Notification Tools
4+
SIEM
4+
Ticketing Tools
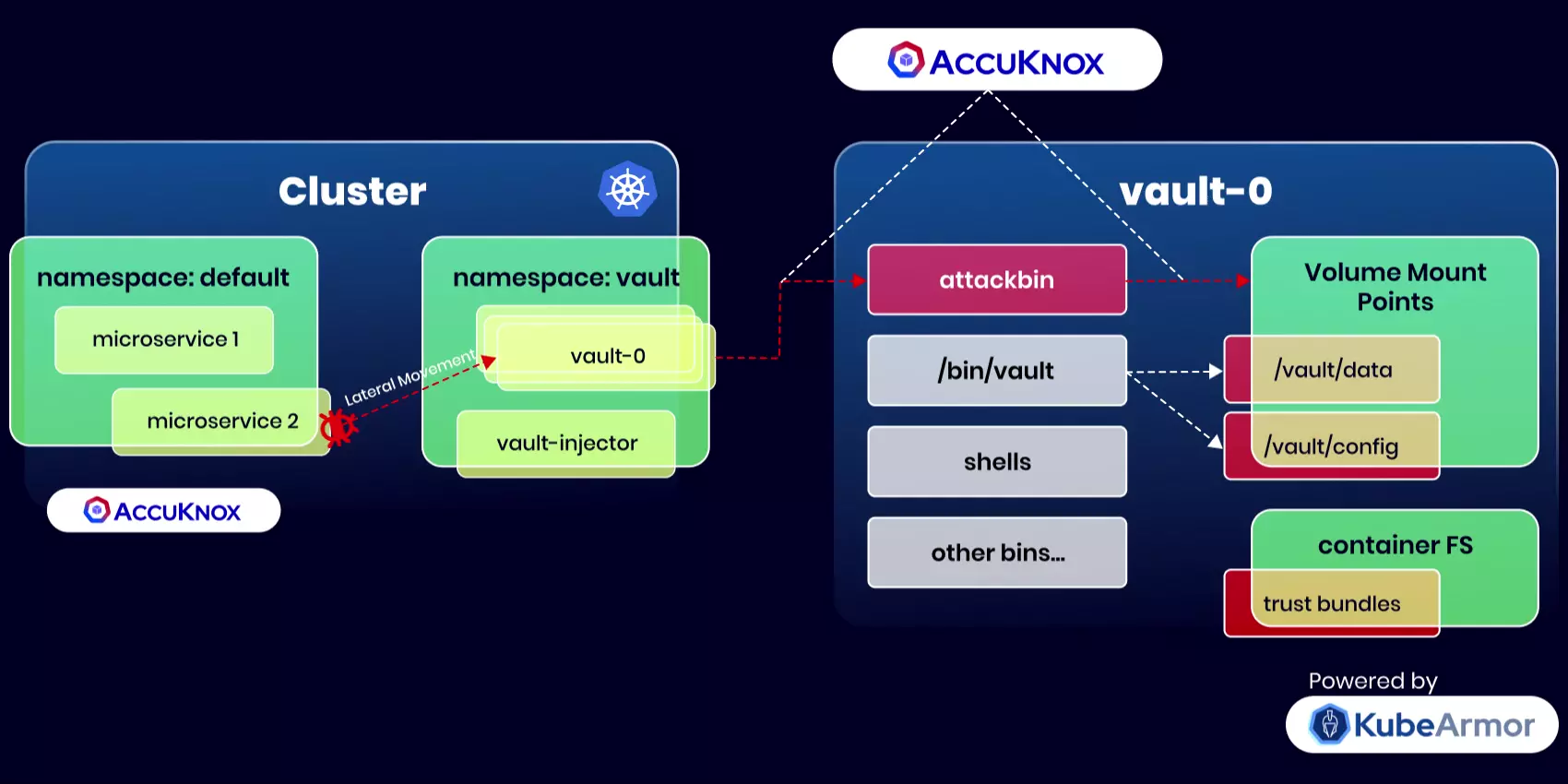
Secure your Secrets Manager
HashiCorp Vault Hardening
- Restrict access to HashiCorp Vault mount points in Pod
- Whitelist and provide fine grained access to ensure least permissive security controls
- Protect onprem Vault from advanced attacks (Ransomware, Bitcoin Miner, DDOS, etc.)
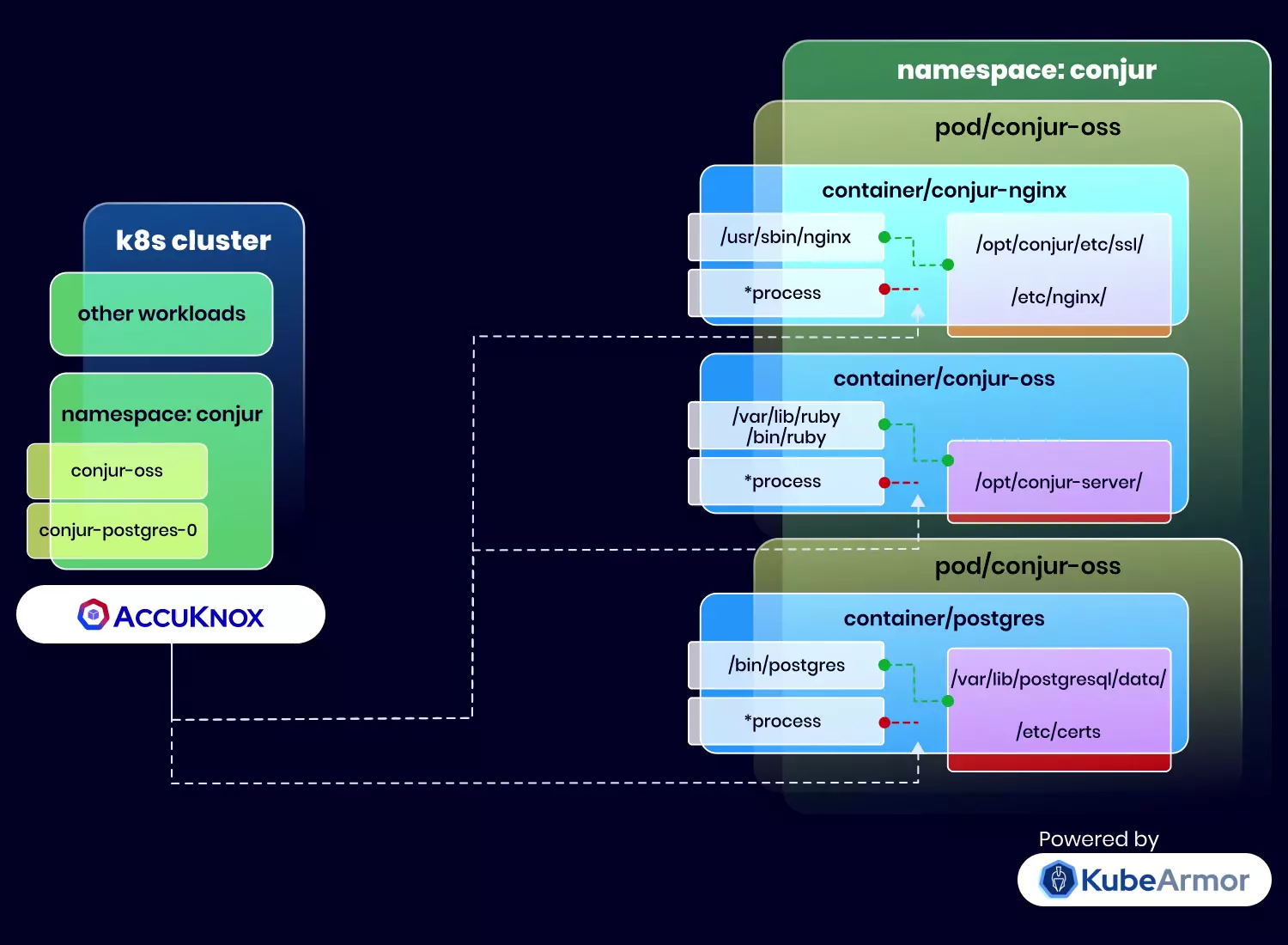
CyberArk Conjur Hardening
- Restrict access to conjur secrets mount points in Pod
- Allow access to certain paths only for certain process(es)
- Prevent Zero-Day attacks on mission-critical workload from insider-threats
“Build to Runtime” Security
Comprehensive Zero Trust Cloud Security Tool
- Comprehensive Agentless CSPM + eBPF & LSM powered CWPP
- OpenSource Anchored in KubeArmor, 700,000+ downloads
- Versatile Secures Modern (K8) and Traditional (VMs) assets
- Flexible Supports Public, Private, Hybrid and Federal Workloads
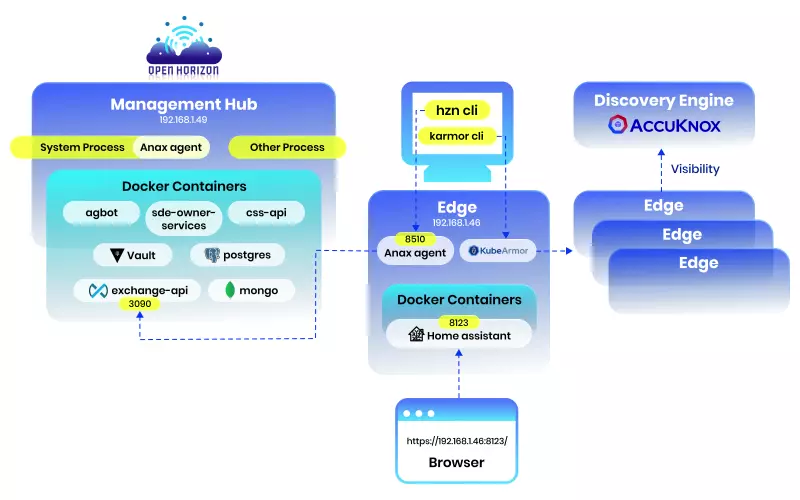
- Innovative 10+ patents, support for IoT/Edge, 5G workloads
Awards and Accolades





Federal Workload Protection for US Government Security
We provide Zero Trust security solution, adhering to federal regulatory standards. Secure air-gapped deployment with our advanced and comprehensive CNAPP security.
Don’t just take our word for it...
70%
INCREASE IN CRITICAL ISSUES RESOLUTION
5
SIEM TOOLS INTEGRATED
 We are very pleased to partner with a Modern, Cloud Native, Zero Trust CNAPP innovator like AccuKnox. Zero Trust security is a commitment we have to our customers. Their work with AWS furthers the value that AccuKnox can deliver to us.”
We are very pleased to partner with a Modern, Cloud Native, Zero Trust CNAPP innovator like AccuKnox. Zero Trust security is a commitment we have to our customers. Their work with AWS furthers the value that AccuKnox can deliver to us.”

80%
EFFICIENCY IN HANDLING FALSE POSITIVE ALERTS
5
MINUTES TO SOLVE KNOWN VULNERABILITIES
 Zero Trust security is Clint Health’s imperative and commitment we have to our customers. AccuKnox’s leading product combined with their successful track record of partnering with their customers forms the foundation for this objective.”
Zero Trust security is Clint Health’s imperative and commitment we have to our customers. AccuKnox’s leading product combined with their successful track record of partnering with their customers forms the foundation for this objective.”

50%
TIME REDUCED IN HANDLING CI/CD PIPELINE ISSUES
1
MINUTE TO OBTAIN INSTANT REPORTS
 Our client, a Large European CyberSecurity agency, was looking for a Zero Trust Security Solution that supports Private Cloud platforms. Our win is a clear testament to the value our clients see in this partnership.”
Our client, a Large European CyberSecurity agency, was looking for a Zero Trust Security Solution that supports Private Cloud platforms. Our win is a clear testament to the value our clients see in this partnership.”

AccuKnox Secures Multiple
Cloud, Cluster, Containers, Code Repositories
Integrate with CI/CD pipelines for Securing Cloud Workloads.
- Static Code Analysis Deeply analyze your code for vulnerabilities and weaknesses.
- CI/CD Pipelines Scanning Continuously scan your pipelines for security flaws and risks.
- Container Security Fortify your containers with robust security measures.
- Kubernetes Orchestration Seamlessly manage and secure your Kubernetes environments.
- Secret Scanning Detect and protect sensitive information from unauthorized access.

We’re an Innovator in Zero Trust Cloud Security Space
17
+TOOLS INTEGRATION
9
+PATENTS
27
+TRUSTED PARTNERS
33
+COMPLIANCE FRAMEWORKS
Trusted By Global Innovators









You cannot secure what you cannot see.
Your most sensitive information is stored on cloud and on premise infrastructure. Protect what is most important from cyber attacks. Real-time autonomous protection for your network's edges.
FAQs
AccuKnox supports allow-based policies which result in specific actions being allowed and denying/auditing everything else, which in turn is the zero trust principle – Never trust, always verify.
Multi-Cloud Coverage: AccuKnox provides a unified and insightful CNAPP dashboard and asset inventory across multiple cloud accounts. Imagine if the SecOps team wants to know how many Virtual Machines are currently deployed across all the cloud deployments. Currently, the Cloud-native users have to log in to each of the hyperscale dashboards and query individually.
With AccuKnox, you can get a consolidated asset inventory across multiple cloud providers. The SecOps teams can ask how many VMs I have in total. How many VMs have possible findings? AccuKnox can cover answers to the aggregated SecOps questions.
Multi-Tool Integration: Cloud providers focus primarily on the cloud assets. Users have code repos, IaC code, and container registries. AccuKnox provides a consolidated way to do risk assessment across Cloud, Container, Cluster, and Code assets (we call it 4C assets coverage).
Post-exploit Mitigation works by killing the suspicious process in response to an alert indicating malicious intent.
In this case, an attacker will be allowed to be able to execute its binary and disable the security controls, access logs, etc to circumvent the attack detection.
By the time the malicious process is killed, it might have already deleted, encrypted, or transmitted the sensitive contents.
Inline Mitigation works by preventing the malicious attack at the time of happening itself.
It doesn’t allow the attack to happen by protecting the environment with a security policy or firewall.
AccuKnox leverages advanced Linux Security Modules (LSMs) such as AppArmor, BPF-LSM, and SELinux for inline mitigation.
AccuKnox CSPM, supports agentless scanning for Public Cloud Infrastructure.
For Infrastructure behind a firewall or Private Cloud, Accuknox CSPM leverages open source-based agents to manage remote nodes for Automated reporting, Error log Delivery, Microservice Monitoring, User Shell Activity, and Resource Monitoring.
AccuKnox CWPP, leverages the open-source CNCF sandbox project KubeArmor for scanning and inline mitigation from known attacks.
Altogether AccuKnox provides complete static and runtime security for a variety of workloads whether they are on Public/Private Cloud, VM, Baremetal, or pure-containerized workload.
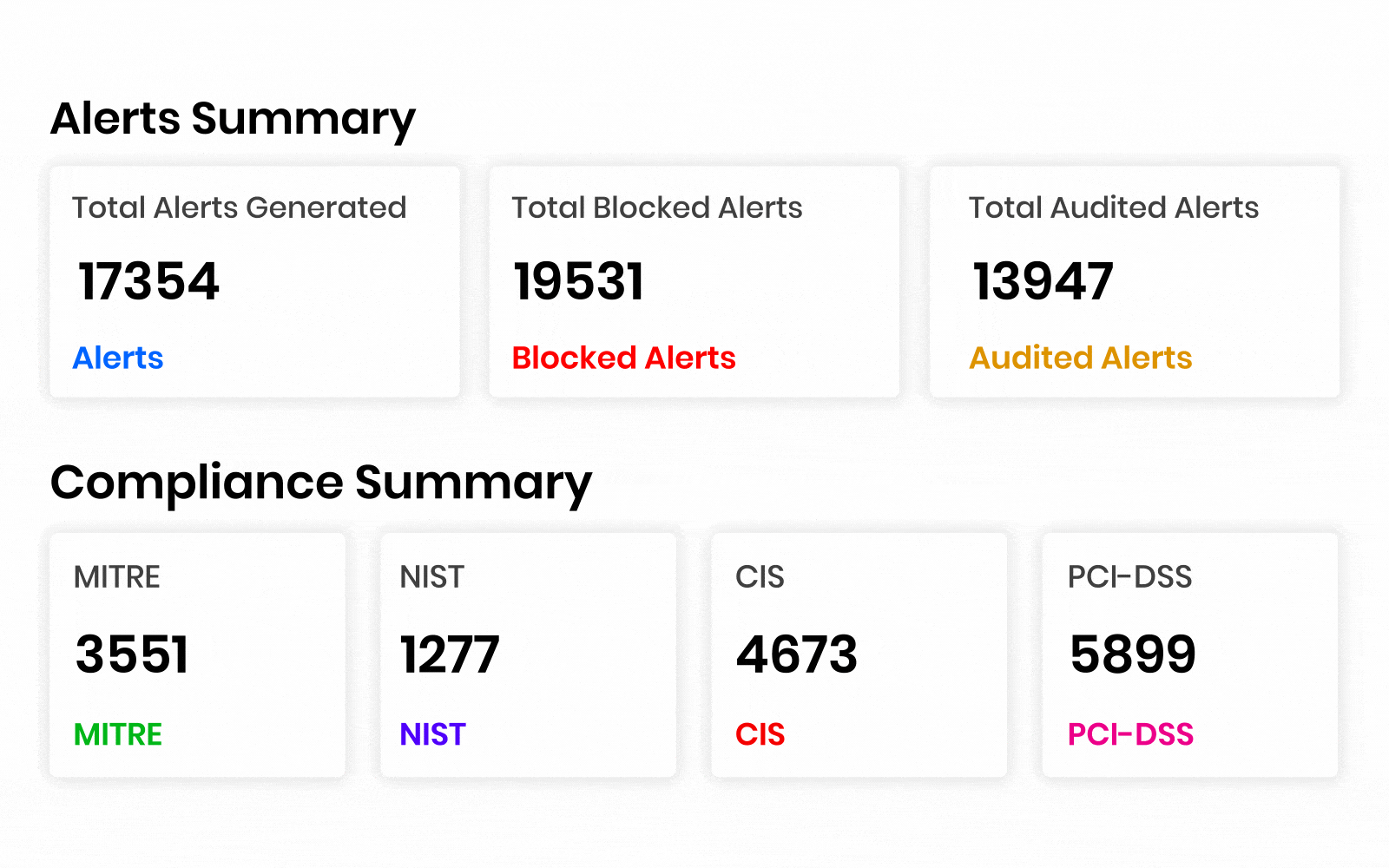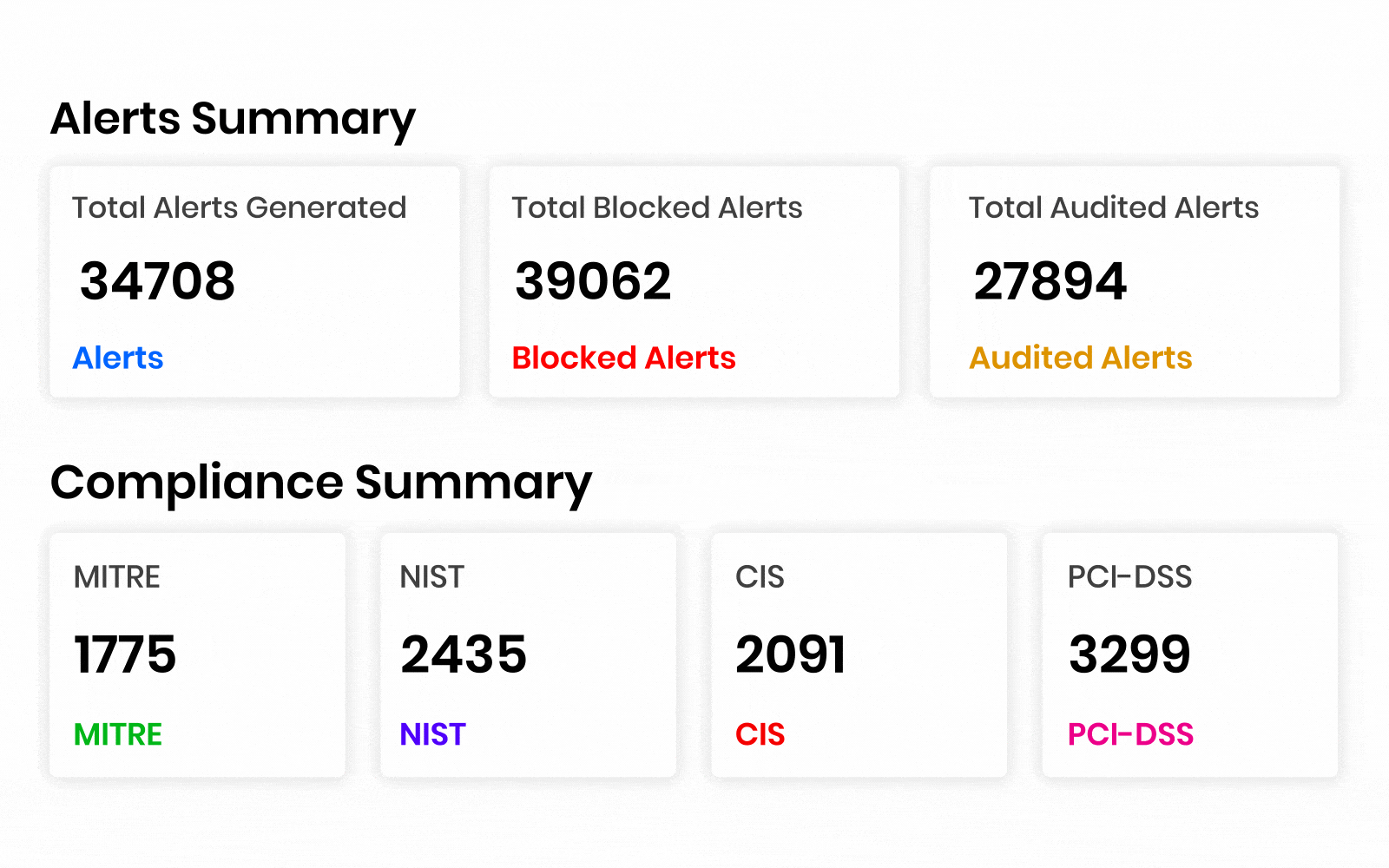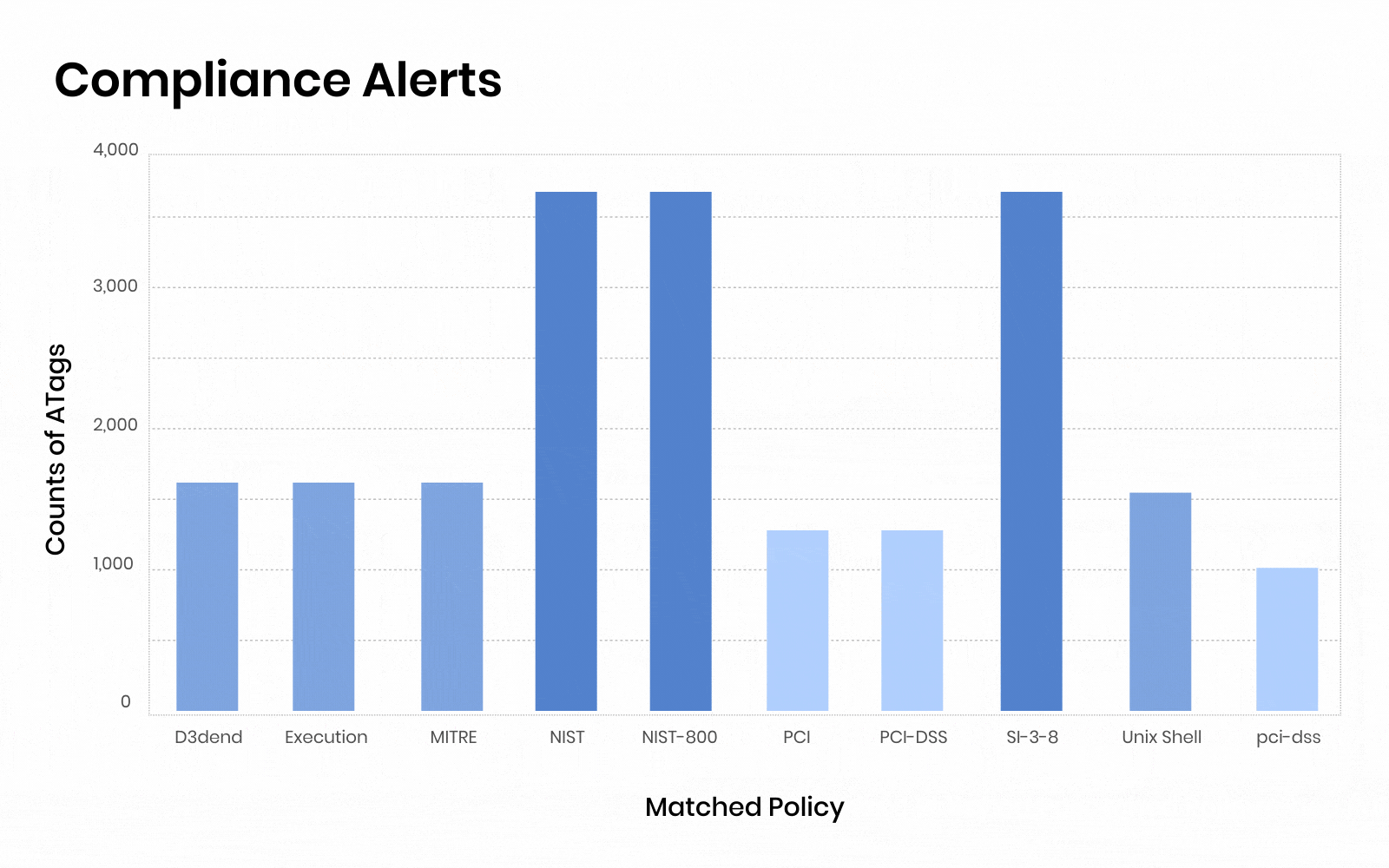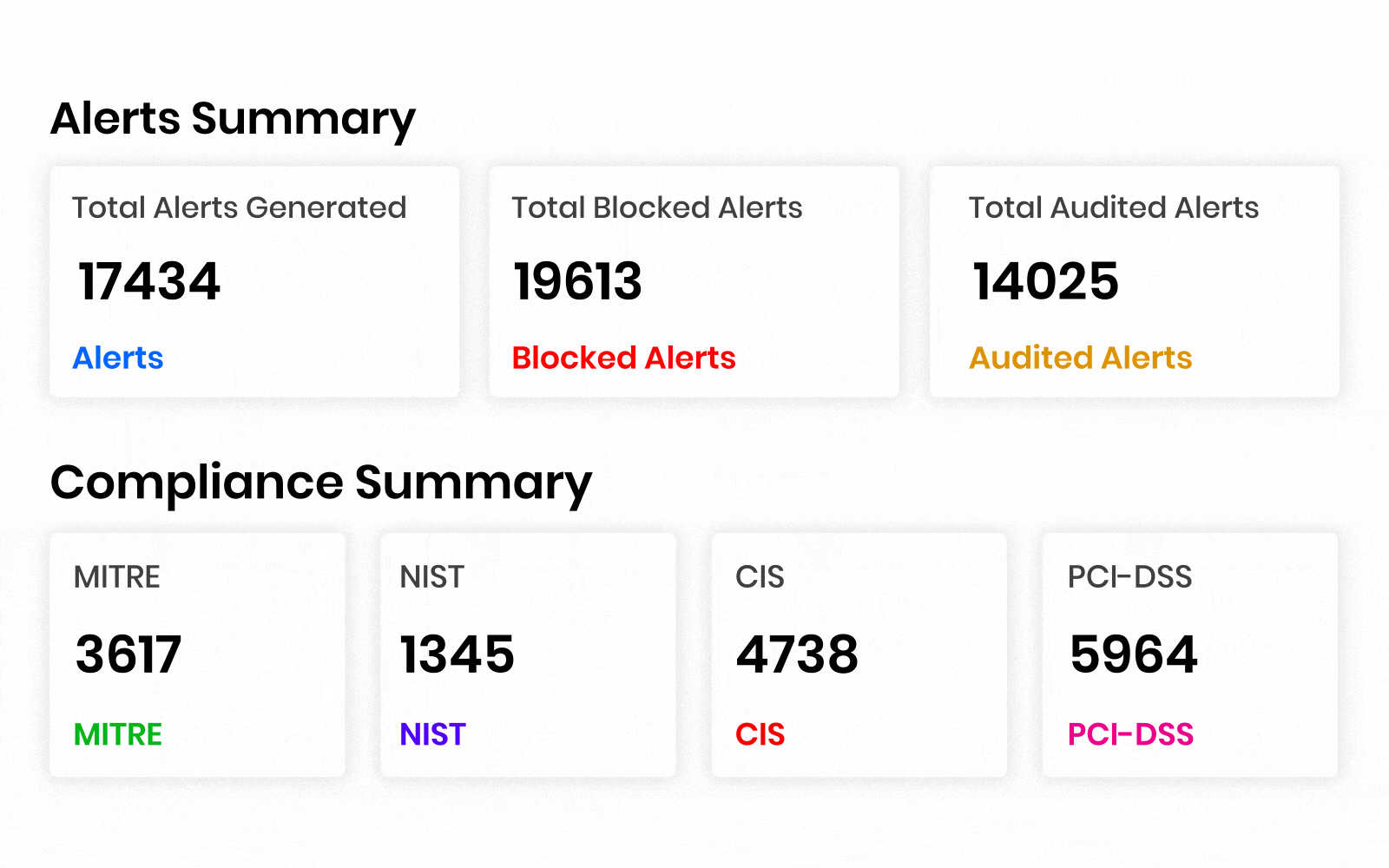
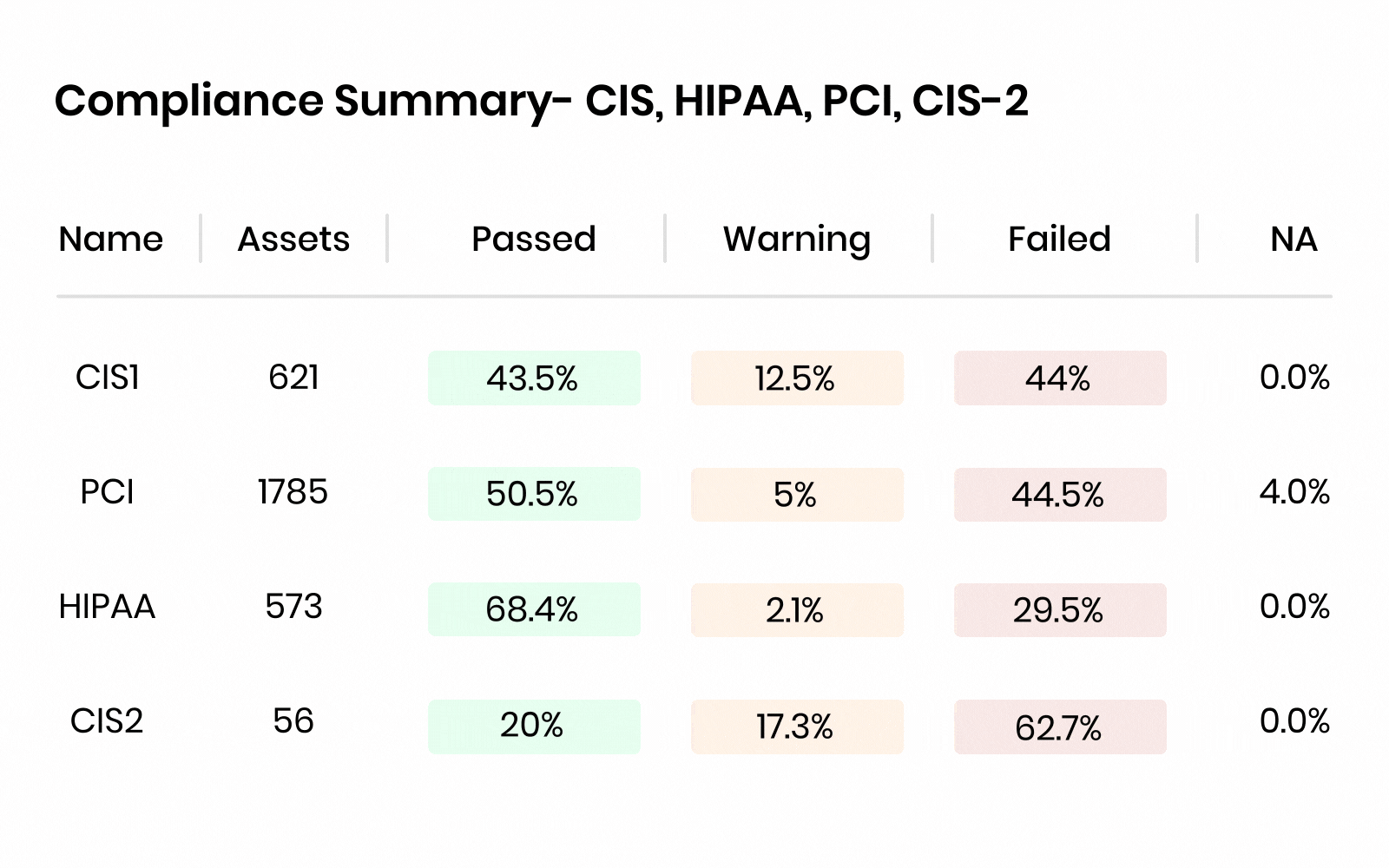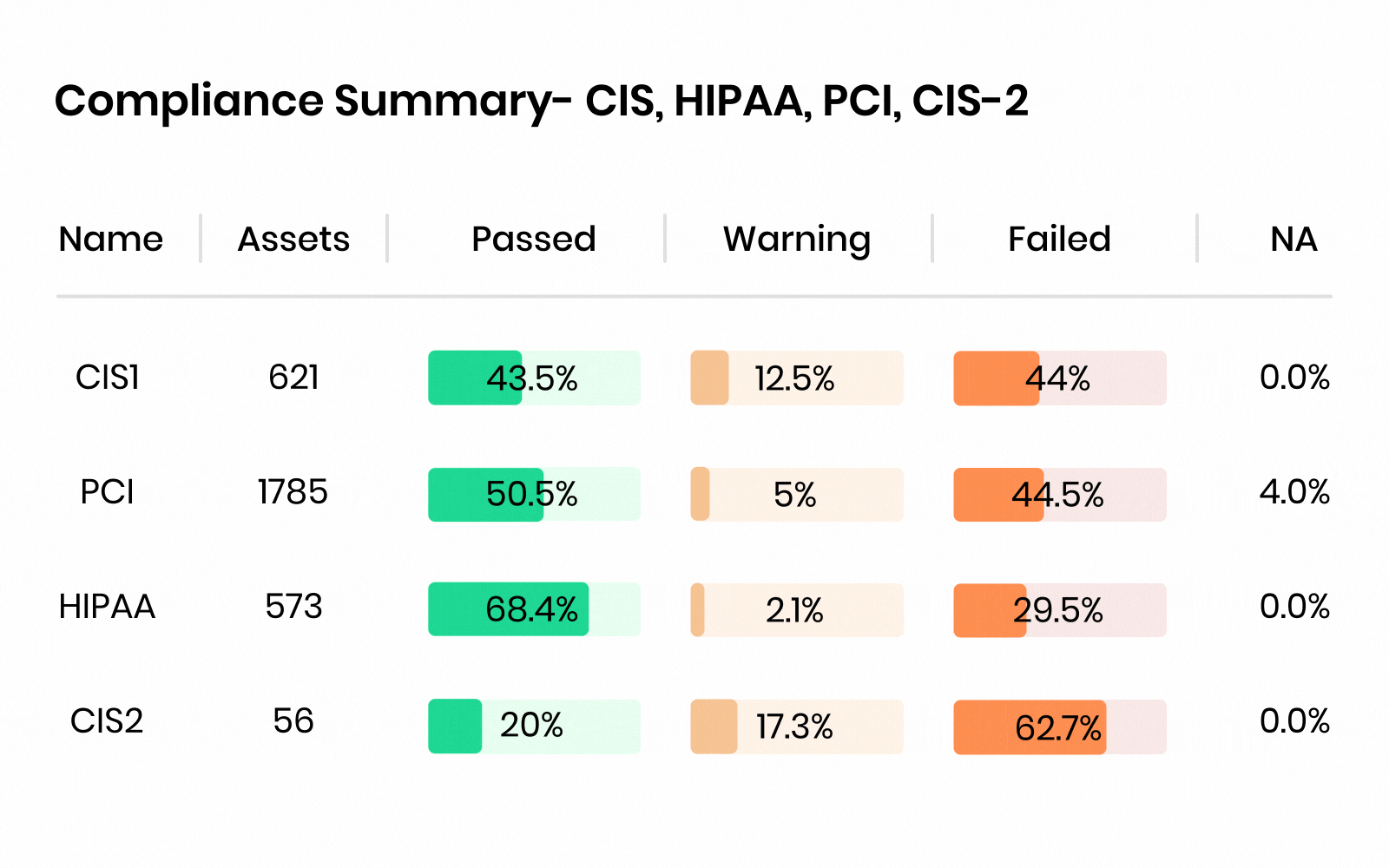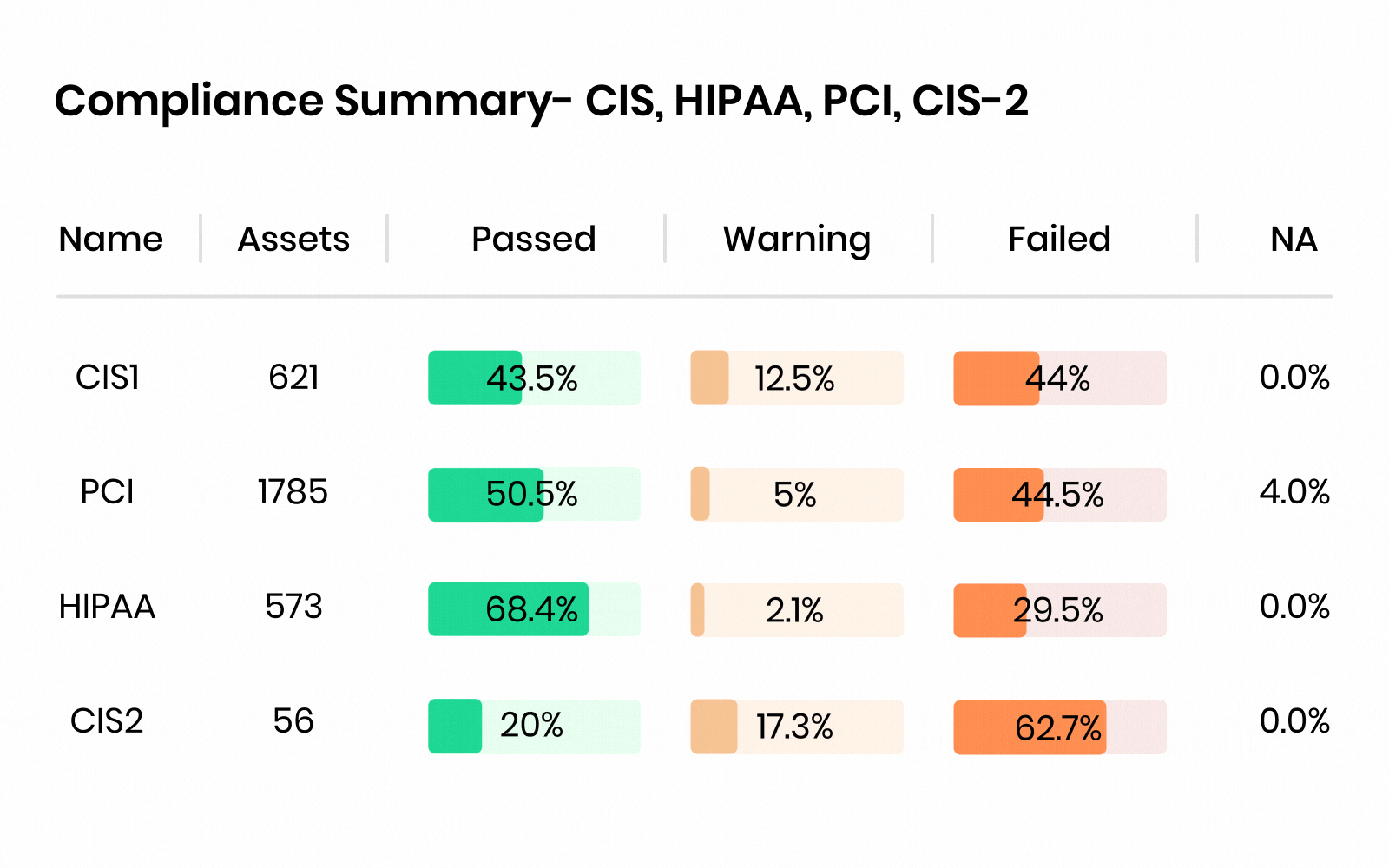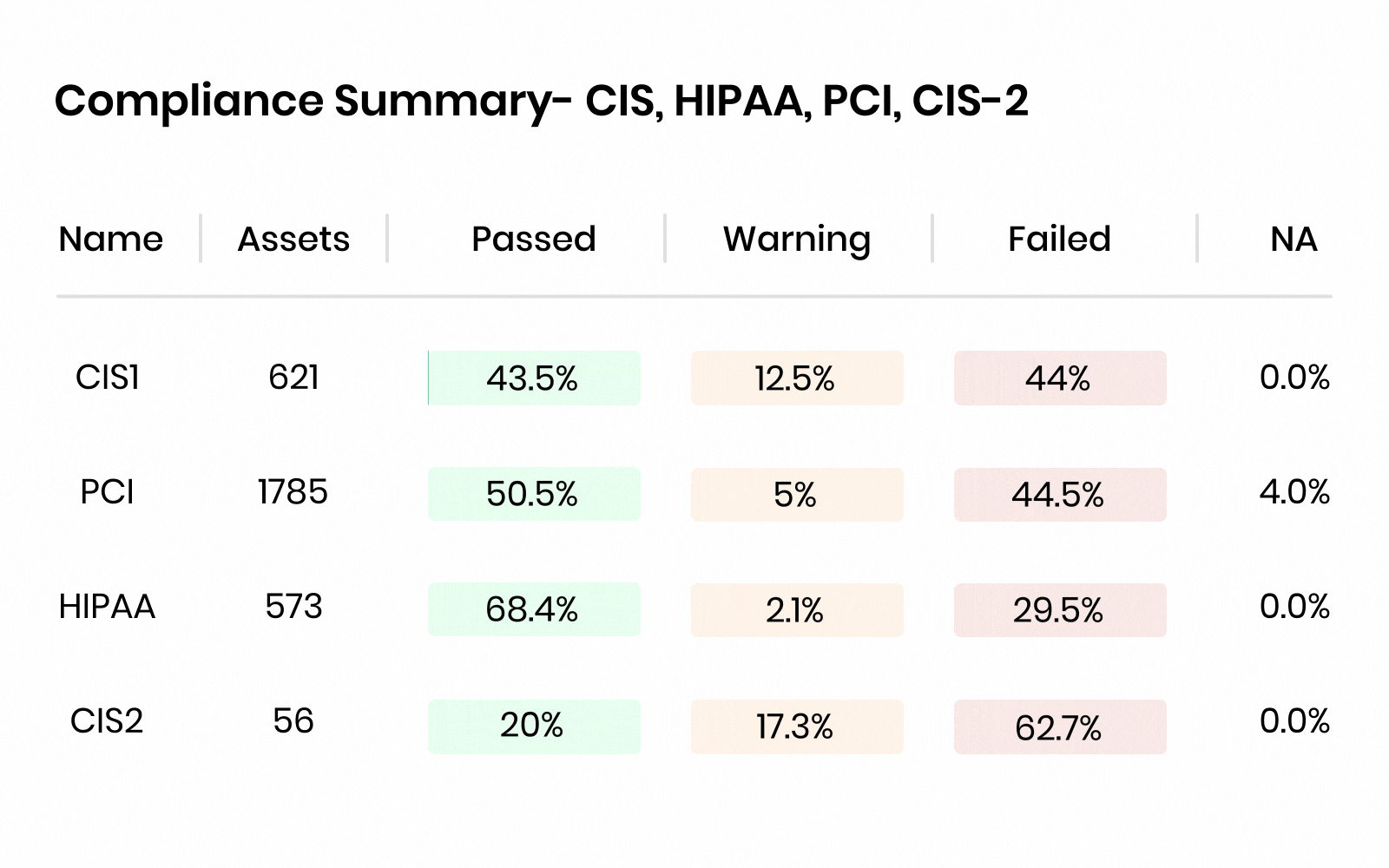
AccuKnox’s CNAPP compliance has 30+ compliance framework coverage and governance from various benchmarks like:
HIPAA, GDPR, SOC2 Type 2, ISO 27001, NIST CSF, NIST SP 800-53, NIST 800-171, FedRamp, ISO 27017, IS0 27018, SOC 3, California Consumer Privacy Act (CCPA), FISMA, APRA 234, VAIT, BAIT, FERPA, COPPA, HITRUST CSF, LGPD, Azure CIS Benchmarks v1.3.0, CSPM Encryption Program, Korean Financial Security Agency Guidelines, Azure CIS Benchmark v2.0.0