Cloud Workload Protection Platform (CWPP)
Monitor runtime protection in multi cloud architecture with access to real-time alerts, compliance status, and asset coverage in just a few clicks. Stay in control of your cluster and namespace security.
FREE PRODUCT TOUR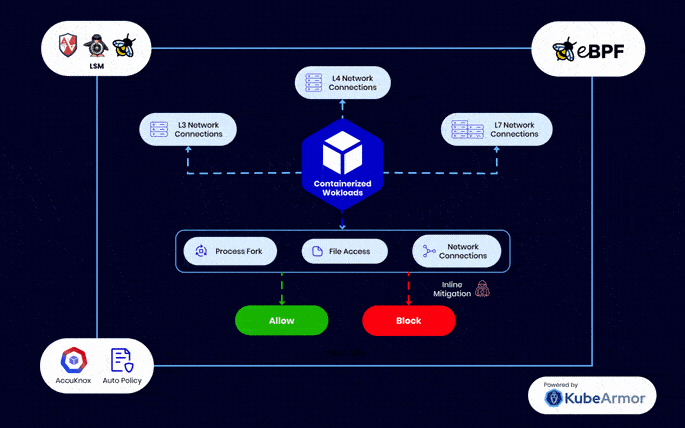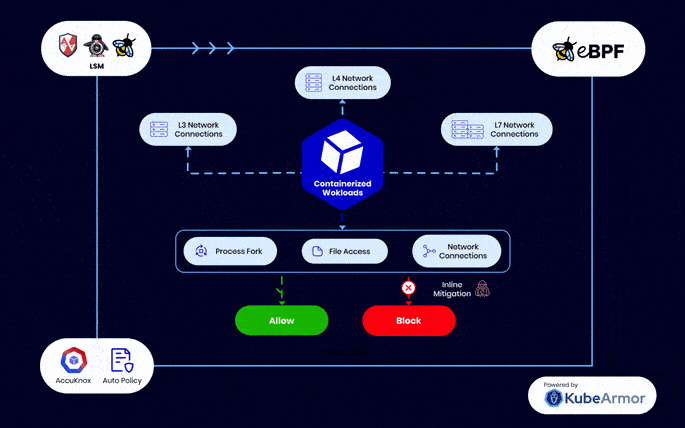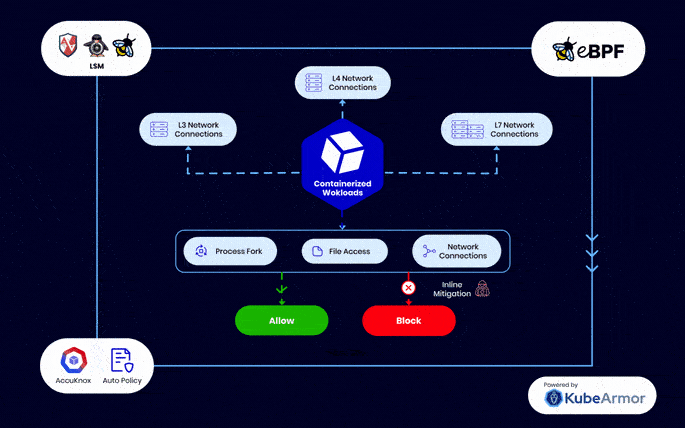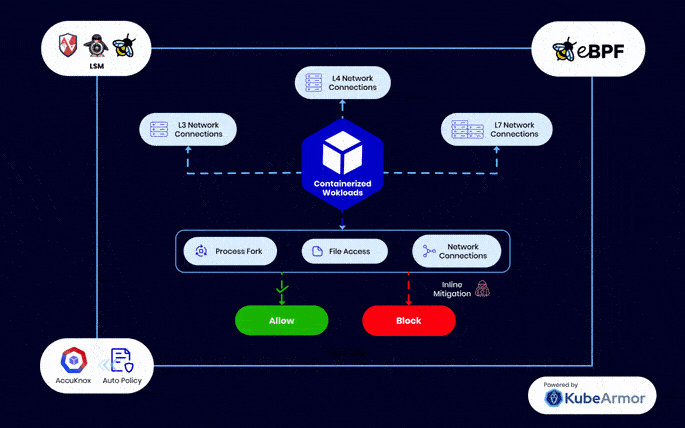
eBPF – Industry Standard Workload Protection
Multi Cloud Vulnerabilities
CWPP ensures consistent visibility and control across hybrid, multi-cloud environments, mitigating vulnerabilities associated with diverse server workloads
Application Pod Vulnerabilities
AccuKnox’s CWPP, leverages KubeArmor and prevents potential exploits, safeguarding against attackers who gain access to application pods and attempt remote code execution.
Detect & Respond Model Challenges
Unlike other runtime security engines which provide a false sense of security as the attacks are mitigated too late, KubeArmor, created by AccuKnox, can perform inline mitigation against Zero Day attacks
Modern Workload Protection
eBPF and BPF LSM in AccuKnox’s CWPP provides modern workload protection without requiring changes to kernel source code, offering enhanced security while maintaining a user-friendly interface
One aggregated CNAPP platform to consolidated siloed toolings

Agent-based Low Intrusion CWPP Platform
Fortifying Applications, Enforcing Zero Trust, Ensuring Security Resilience
- Our CWPP is based on the Zero Trust fundamentals that align with NIST guidelines and Gartner Recommendations.
- We anticipate, adapt and provide proactive remediation to prevent cloud attacks.
- Secure your workloads
- Automated Zero Trust policy generation
- Customizable and fine grained policy control (observe/audit, enforce)
- Reduced alert fatigue with zero false positives
- Hardening policies based on MITRE, NIST, CIS, PCIDSS

Unique CWPP Offerings
Combining advanced technologies for proactive security, inline remediation, and efficient extension of kernel capabilities, setting a new standard in cloud workload protection.

![]()
App Behavior
- Discover the behavior of workloads running in public or private clouds, on-premises in VMs/BareMetal, or in Kubernetes and containerized environments.
- AccuKnox auto detects and recommends Behavioral Policies based on app observability.
- File system, processes and networks that are granted access

Application Micro segmentation
- Micro segmentation by Pod level isolation, fine-grained control & Application-aware Policies.
- Detects which specific process requires network access and careful whitelisting
- Derive network understanding from CNI (agnostic to type) to construct L3, L4 and L7 layers of understanding
- Ensures workload security by isolating workloads and protecting lateral movement or unauthorized access

Understand the practical steps to transform your cloud security with Enterprise Grade Zero Trust CNAPP.
App Hardening
- Readymade hardening policies based on industry leading compliance frameworks like CIS, MITRE, NIST-800-53, and STIGs.
- These policies help secure workloads by reducing attack surface through block-based recommendations.
- Auto recommendations to the cluster and customizable.
- All violations blocked with inline mitigation approach.
- Tweak and create customized policies is also possible


Network Micro Segmentation
- Helps discover the application behavior of the workloads running in the public cloud, private cloud, or on-prem in VMs/BareMetal or local Kubernetes orchestrated or unorchestrated pure containerized cluster.
- Auto-detects and recommends Behavioral policies based on app observability.
- File system, processes and networks that are granted access
Zero Trust
Top Use Cases in Workload Security
Auto discovered Zero Trust policy
Automatically Generated Hardening Policies Based on Standard Compliance Framework. Our system has the capability to suggest hardening policies based on common compliance frameworks such as MITRE, NIST, PCI-DSS, and CIS.
Custom Zero Trust policy
Using the Policy Editor Tool to Personalize Policy Creation
Inline Remediation
Ensuring Application Uptime and Zero Trust Posture with Inline Remediation, With a robust, declarative policy in place, it’s possible to execute inline remediation against runtime attacks like APT vulnerability and log4j. This approach helps to maintain the uptime and zero trust posture of your applications, ensuring their continued protection.
Network Micro Segmentation
Isolating Workloads and Restricting Traffic to Prevent Malicious Lateral Movements is simplified. To prevent malicious lateral movements, it is important to have the ability to isolate workloads and restrict traffic.
Self Guided Tour
How to Prevent execution of malicious code in Jupyter Notebook
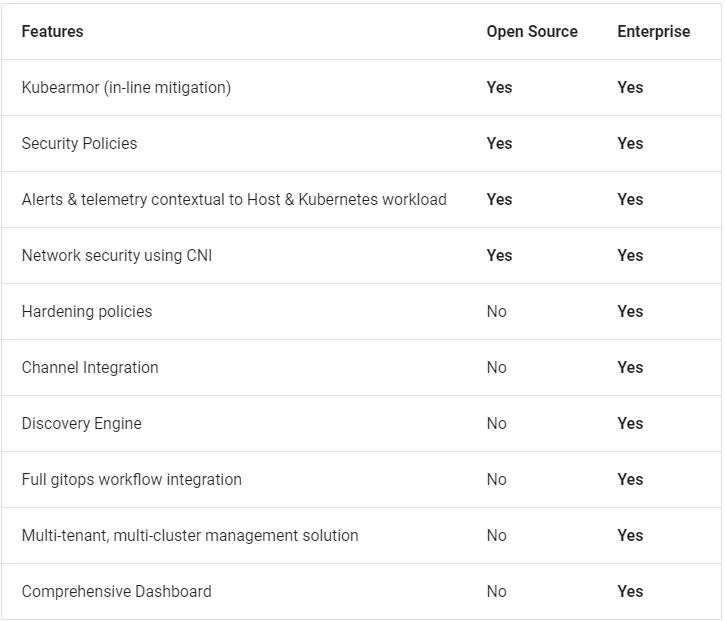
CWPP Pricing
AccuKnox is a Gen-AI-powered Zero Trust Cloud Native Security Platform that provides comprehensive security for public and private cloud deployments.
Trusted By Global Innovators

CWPP Product Tour
FAQ
AccuKnox CWPP provides micro segmentation at the lowest possible granularity level which is also the smallest execution unit in Kubernetes i.e. pods.
Our CWPP solution helps you to identify process execution requests from the pods, network connections the pods are trying to make internally or externally, and the system the pods are accessing.
By observing the behavior of a particular pod and restricting that behavior so that it functions according to the expected flow of process/events/traffic, one can develop a least permissive security posture by creating whitelisting policies and auditing/denying everything else.
KubeArmor is a security solution for Kubernetes and cloud native applications that help protect your workloads from attacks and threats.
By providing a set of hardening policies that are based on industry leading compliance and attack frameworks such as CIS, MITRE, NIST-800-53, STIGs, and 30+ compliances.
These policies are designed to help you secure your workloads in a way that is compliant with these frameworks and recommended best practices.
Accuknox CWPP solution provides a Discovery Engine agent that assesses the security posture of your workloads and auto discovers the policy set required to put the workload in least permissive mode.
Our CWPP tool also provides a Shared Informer Agent which collects information about clusters like pods, nodes, namespaces, etc.
The Policy Discovery Engine discovers the policies using the workload and cluster information that is relayed by the Shared Informer Agent.
AccuKnox supports
- SaaS, PaaS, IaaS
- AWS, GCP, Azure
- Kubernetes – fully supported; refer to supported distributions
- Serverless – Fargate and ECS supported
With AccuKnox, you can set up monitoring for assets or groups of assets to get alerts for changes observed in their metadata (software version, etc.)
Our Drift detection capability is inherently monitoring the compliance checks (pass/fail) that have changed between scans.
We collect alerts and telemetry generated by KubeArmor and Cilium. These alerts are part of our CWPP offering. These alerts are generated for the events that have violated/complied with a policy.
For these alerts, notifications can be enabled as well through channels like Slack, email, etc.













