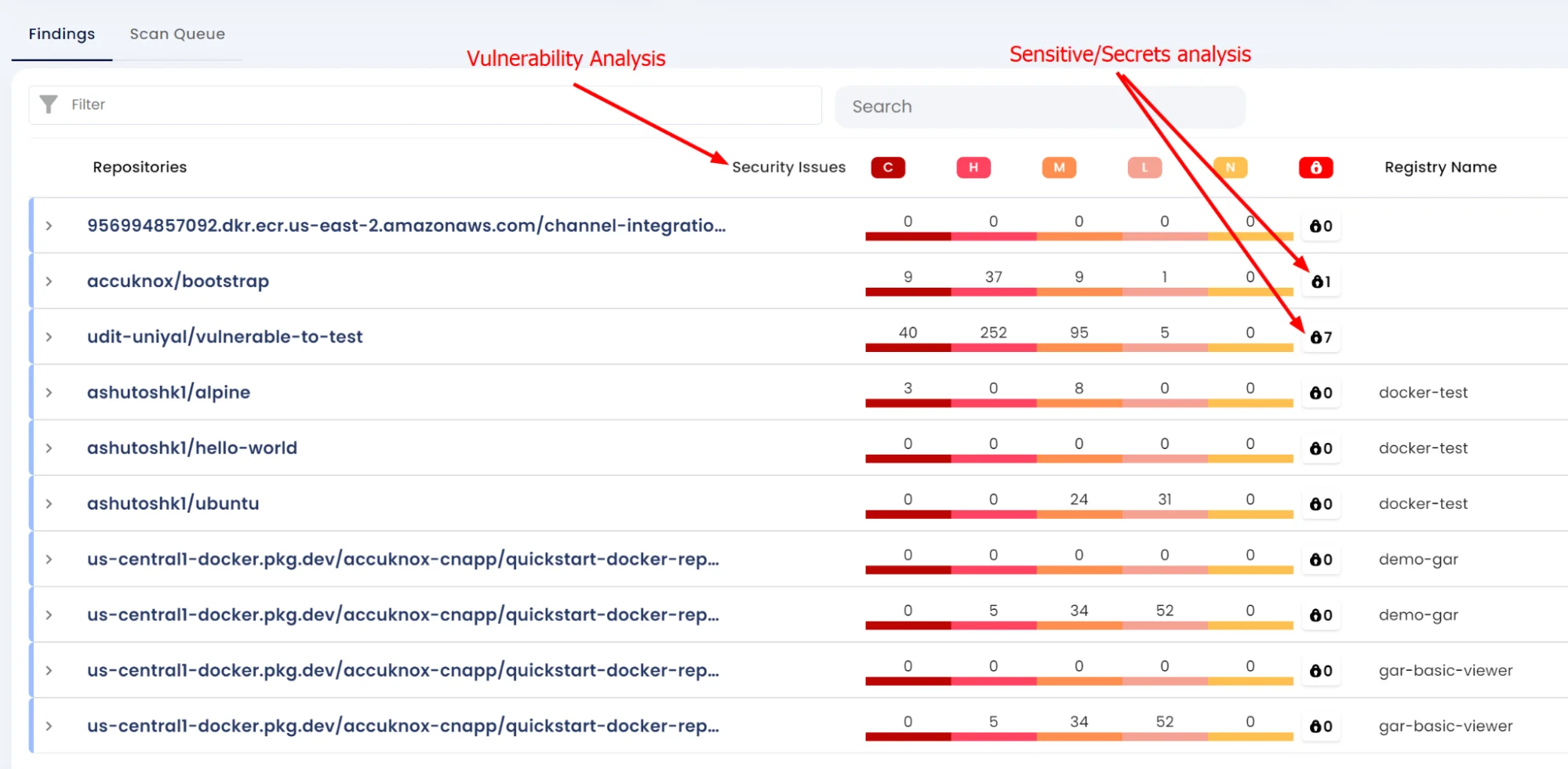
CSPM
- Asset Inventory
- Misconfiguration
- Baseline and Drift Detection
- Container Security
- Vulnerability Management
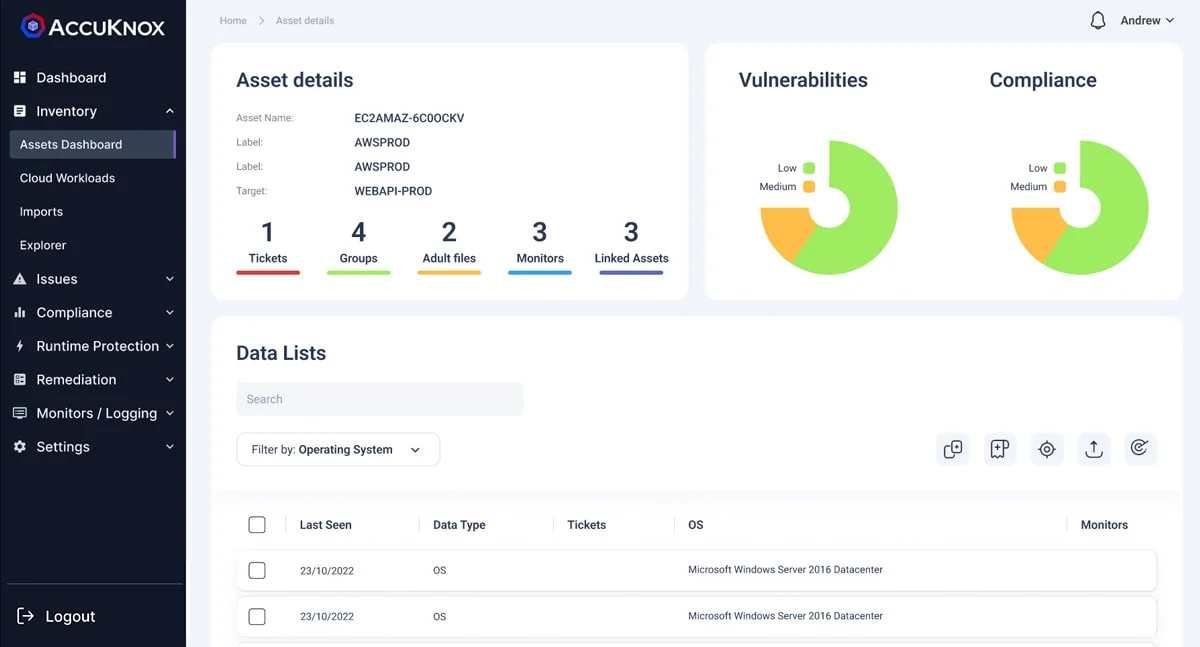
- Identifies assets and provides visibility across a multi-cloud infrastructure
- Associates misconfigurations and vulnerabilities with asset
- Categorize assets in type of cloud resource and further allow assets to be in a customized group
- Segregated assets based on different environments (dev/test or prod) and tagging
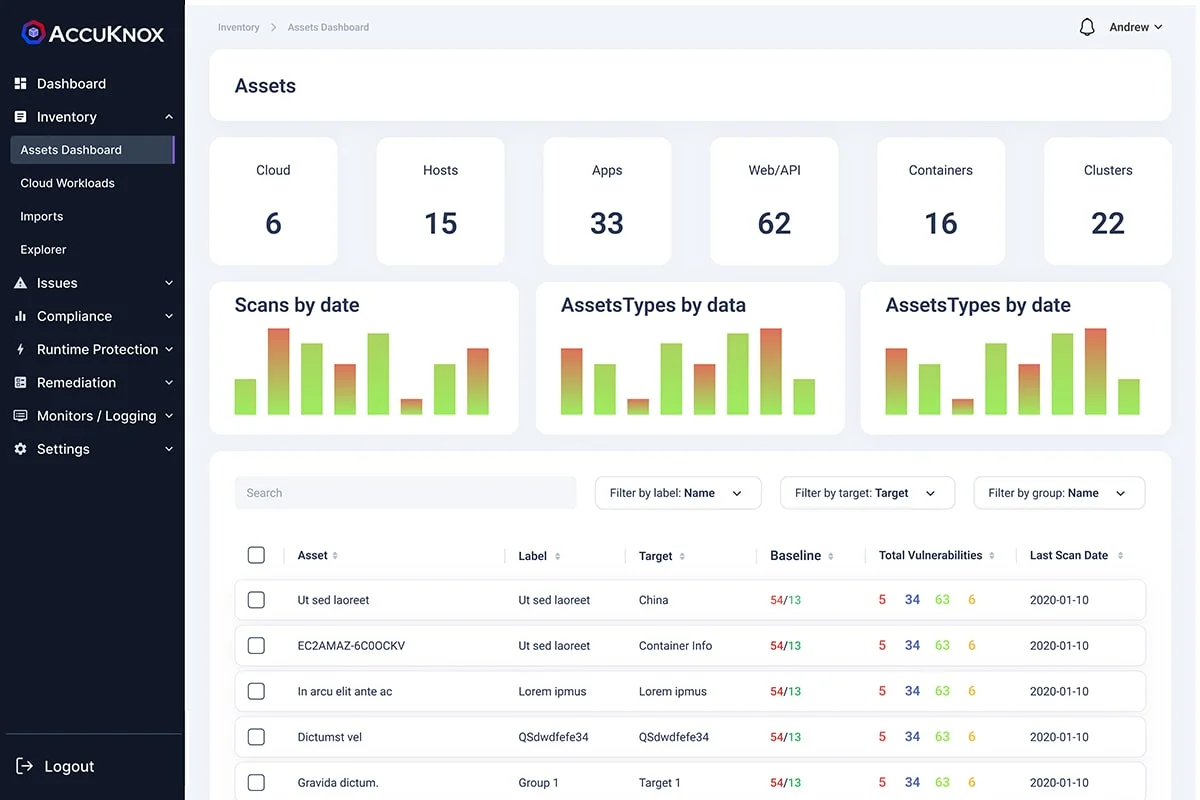
CWPP
- App Behavior
- Application Microsegmentation
- Network Microsegmentation
- App Hardening
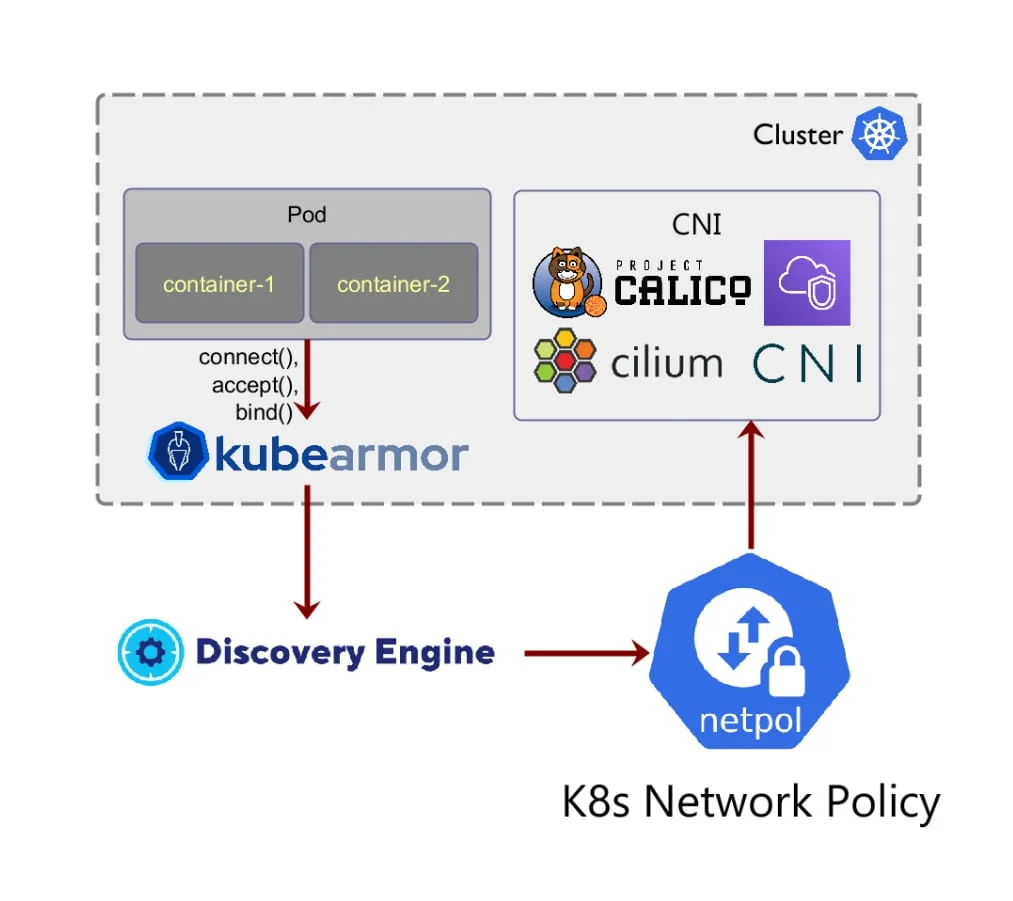
App Behavior
AccuKnox Runtime Security helps you discover the Application Behavior of the workloads running in Public Cloud, Private Cloud, or On-prem in VM/BareMetal or local Kubernetes orchestrated cluster or unorchestrated pure-containerized cluster.
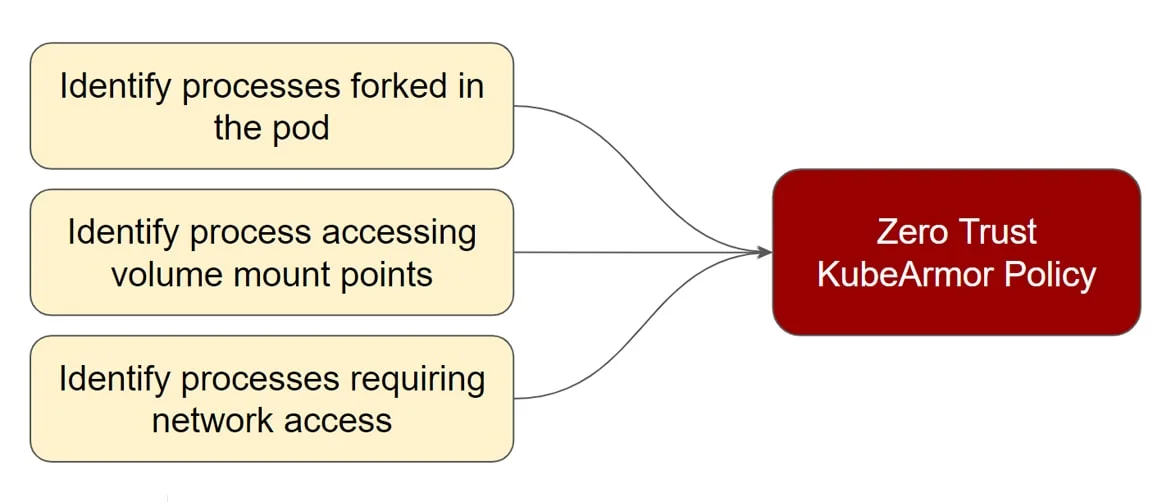
AccuKnox auto-detects and recommends Behavioral Policies based on app observability
- File system access for processes
- Processes that are getting accessed
- network access for certain process
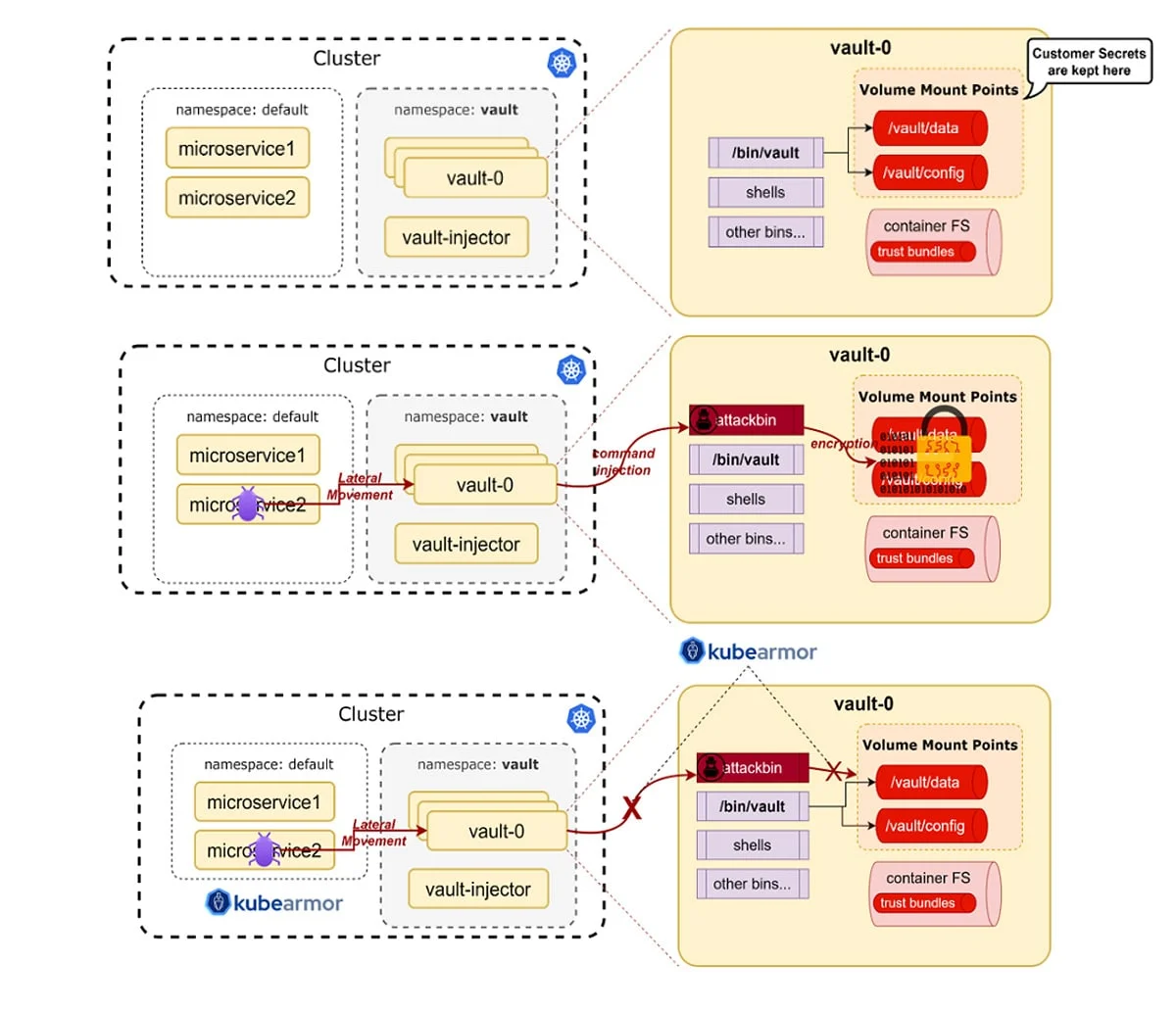
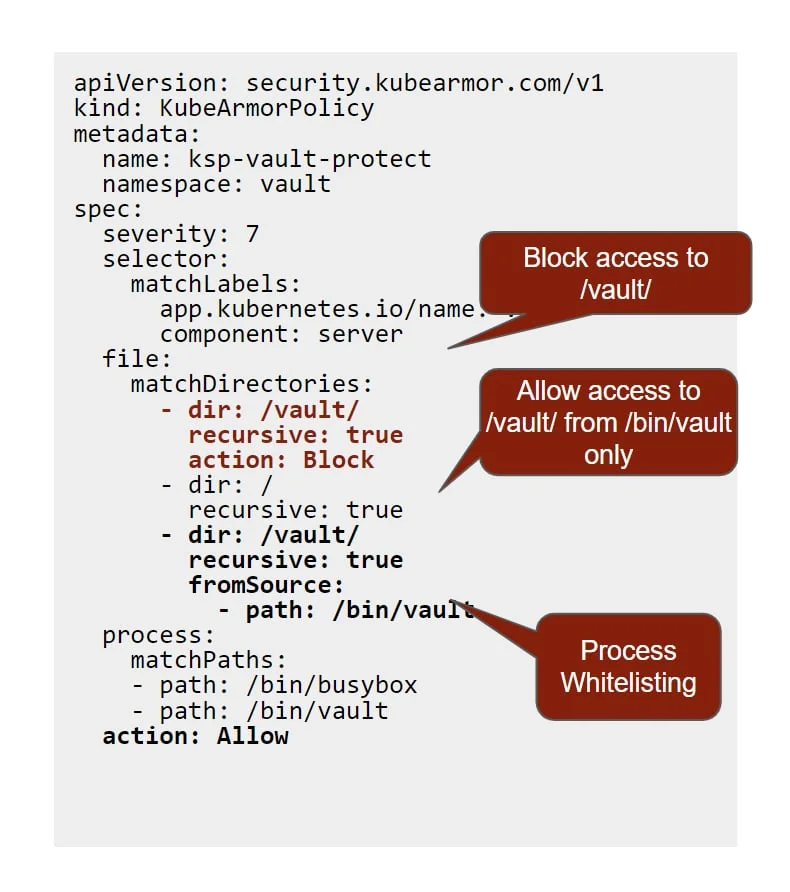
Securing Secrets
- Hashicorp Vault
- Cyberark Conjur
Ransomware Attacks on HashiCorp Vault:
HashiCorp Vault helps organizations reduce the risk of breaches and data exposure with identity-based security automation and encryption as a service.
If any ransomware attacker tries to compromise the security of the pod and gets access to the vault pod, they can do a command injection and encrypt the secrets stored in the Volume mount points. Then the organizations have to pay millions of dollars to get back their secrets decrypted
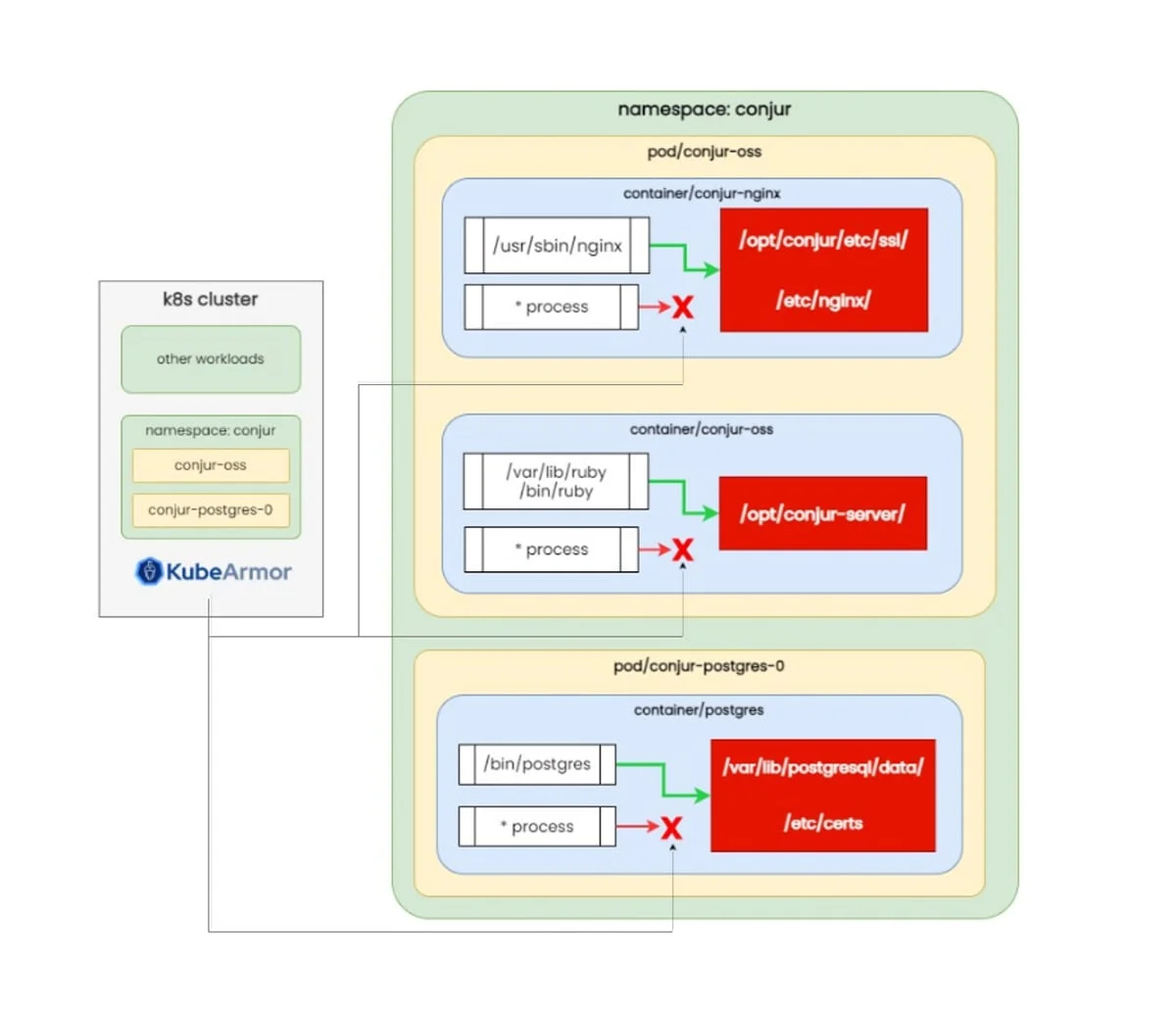
Fortifying Vault with AccuKnox Security
AccuKnox helps in identifying default security posture when the vault is accessing the volume mount process concerning: –
- Process that is accessing volume mount point
- Path from where its getting accessed
Based on this behavior, we can restrict operation to these specific processes from a specific path. Hence, even in the case of a breach, any Remote Code Execution will be blocked instantly
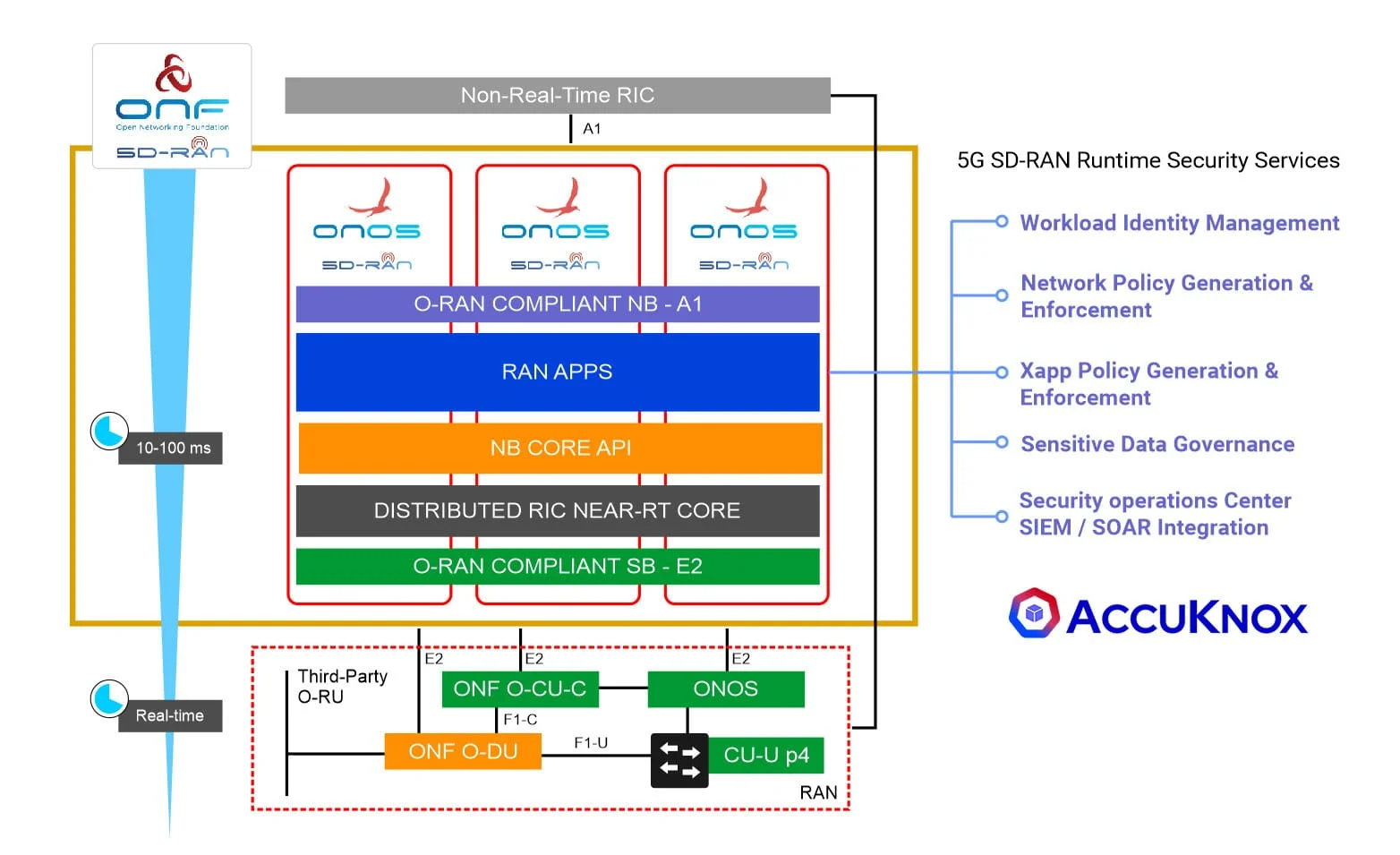
5G Security
- Problem Statement
- How do we secure
Defend the Backbone: Fortify Your 5G Control Plane with AccuKnox Security
The most critical part of 5G is the control plane.
- nRT-RIC (near-RealTime RIC) built on micro-ONOS using a microservice architecture hosted on Kubernetes (K8s).
- SD-RAN control functions are containerized and deployed by Kubernetes as extensible workloads (or xApps).
While this fosters rapid innovation in the control plane it also poses challenges regarding the stability and security of deployed xApps such as:
- Permissive process-level constraints
- Authenticated identities
- Data flow privacy
- Comprehensive runtime monitoring
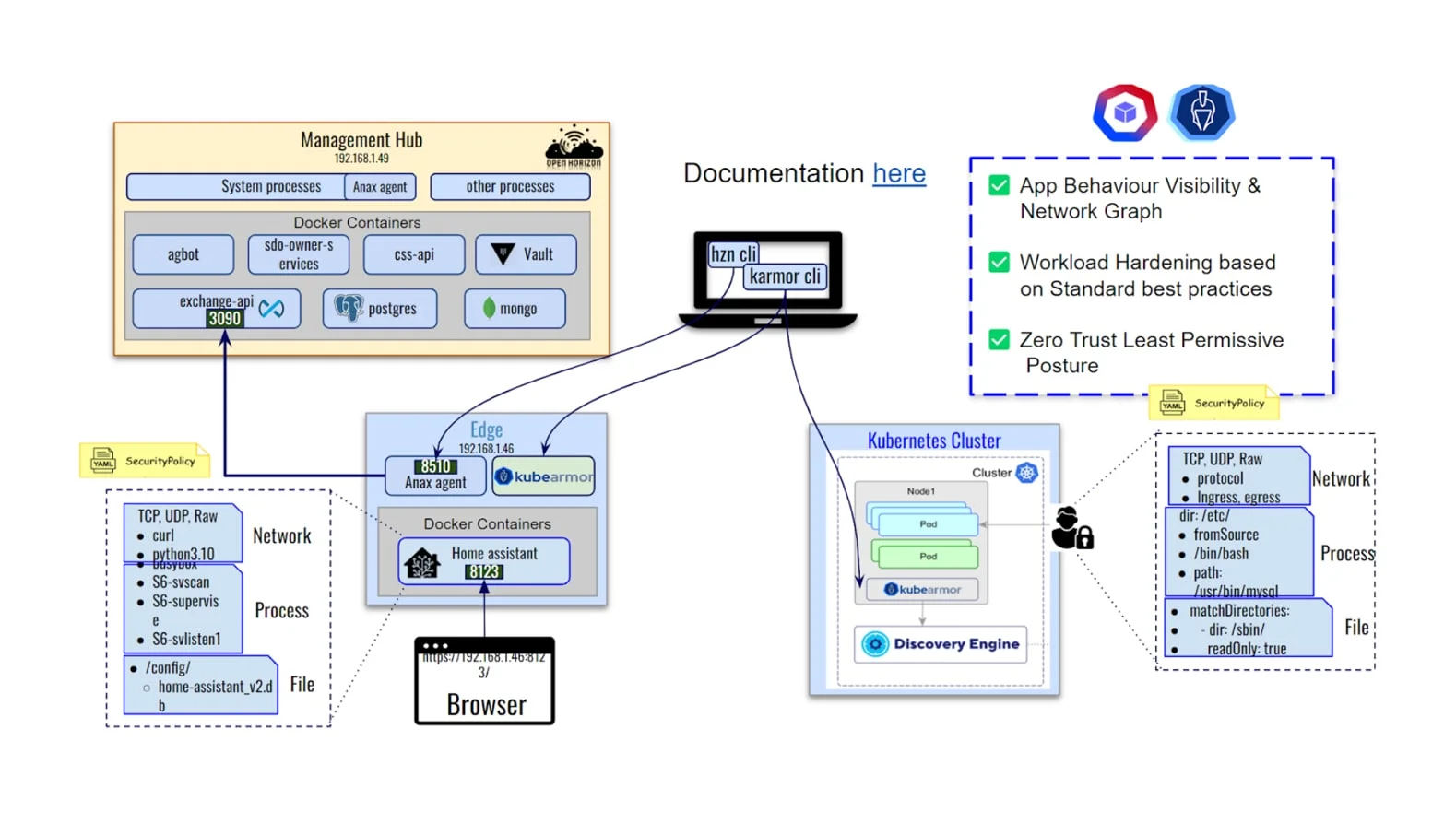
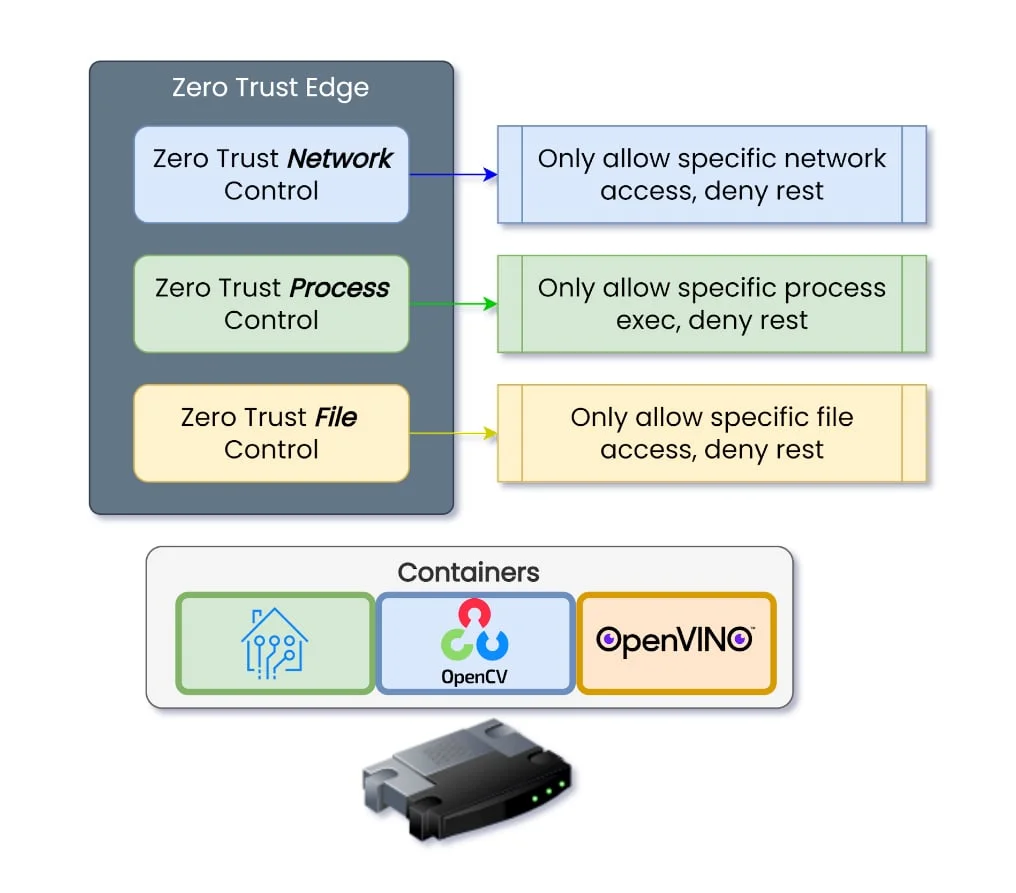
Zero Trust Edge Security
- Network and Application perspective
- Securing IBM Open Horizon
Zero Trust both from Network and Application perspective
- Network: Only allow known entities to connect to the edge device, deny everything else.
- Application: Only allow known processes to operate within the container, deny everything else.
Sensitive Data: Only allow known processes to access sensitive data
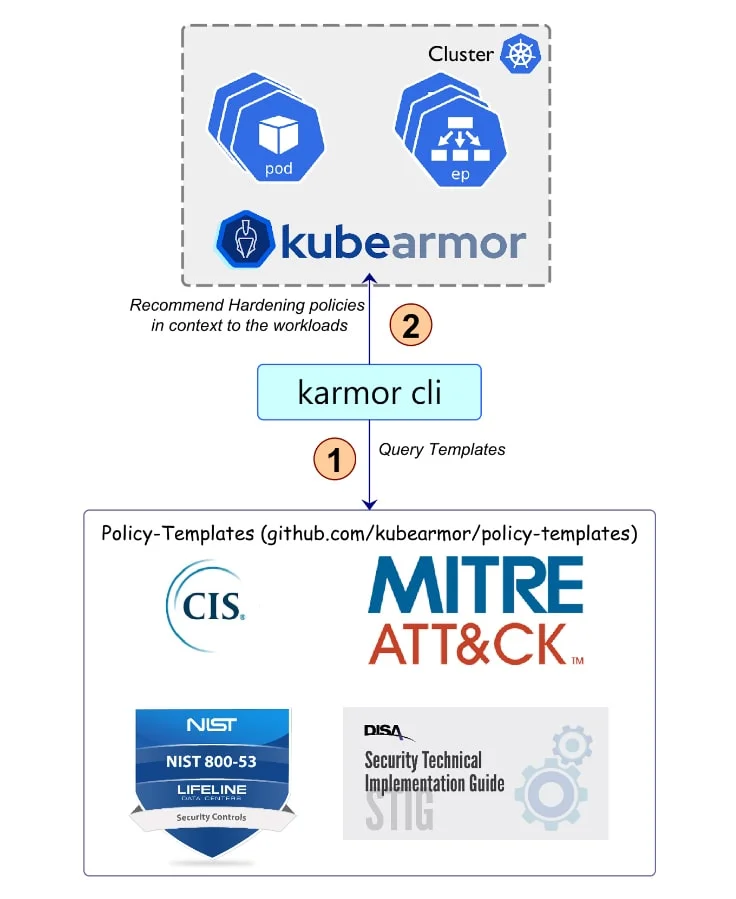
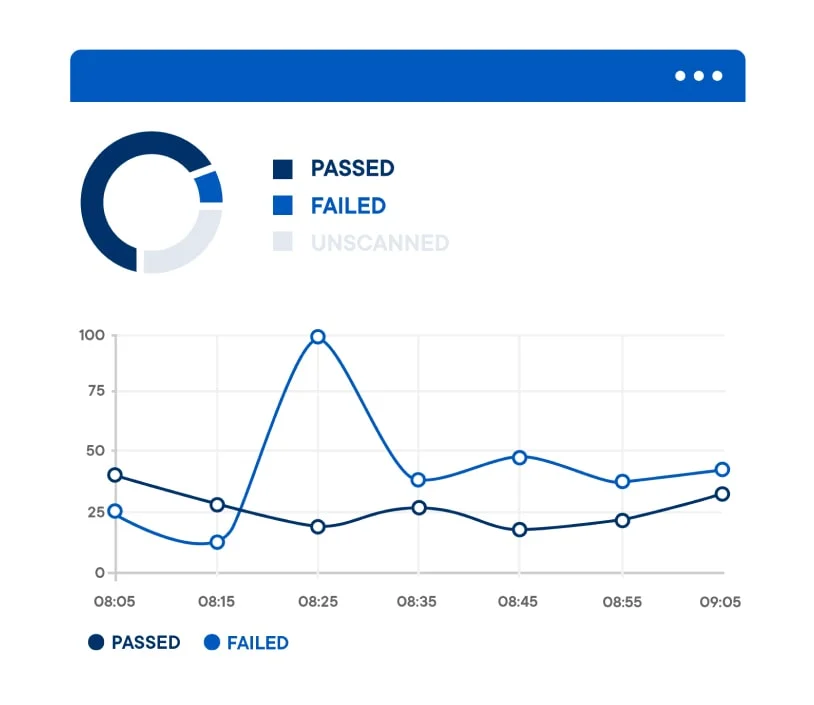
Compliance & Reporting
AccuKnox delivers NIST, MITRE, CIS, and DISA compliance reports:
- Get the continuous compliance summary for cloud resources and applications based on governance and standard framework such as –
- CIS
- MITRE
- NIST
- PCI-DSS
- Get alerts when those compliance controls are violated
- Get namespace based alerts and compliance summary
Policy as code
- Overview
Embrace the Next Generation of Security with Policy-as-Code
- Auto-recommended Policy-as-Code, a powerful framework that combines security policies and code to fortify your digital landscape
- Enforce security best practices, detect vulnerabilities, and ensure compliance throughout your entire software development lifecycle
- Customize curated Policies with a simple Policy Editor UI Tool
Zero Day Attack
- Overview
- Zero-Trust Posture
- Hildegard
AccuKnox delivers Zero Trust security controls to thwart several attack vectors by preventing:
- Backdoor fetch-store-exec operations from subverted process or embedded malicious logic
- Unauthorized network Interface usage
- Unauthorized file system manipulations
- Prevents unauthorized process execution, termination, thread hijacking
- Prevents unauthorized administrative functions and command invocations
- Introduces strong identity management for all cross-container communications
- Produces fine-grain app-level audits and alerts for all permission violations
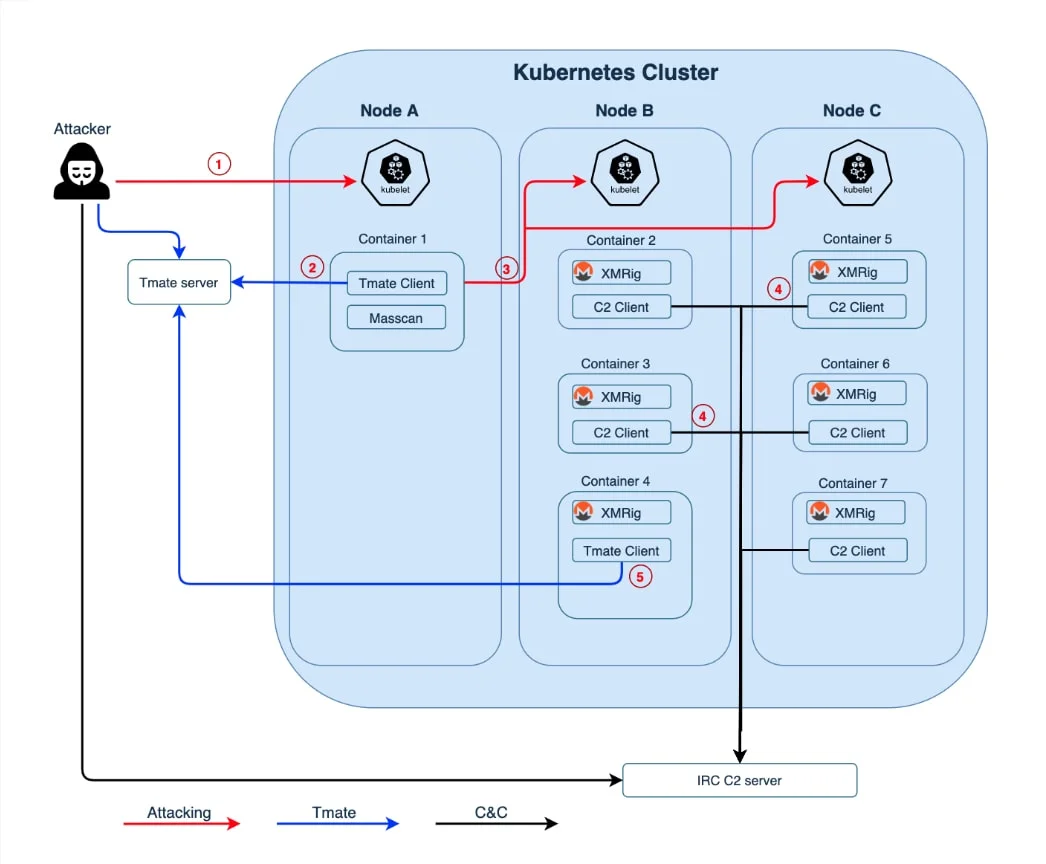
DevSecOps
In keeping with every organization’s goal to bridge the chasm between development, operations, and security, AccuKnox delivers all its capabilities in a DevSecOps model allowing organizations to innovate at the speed that their business calls for without adding disproportionate security and operations overhead
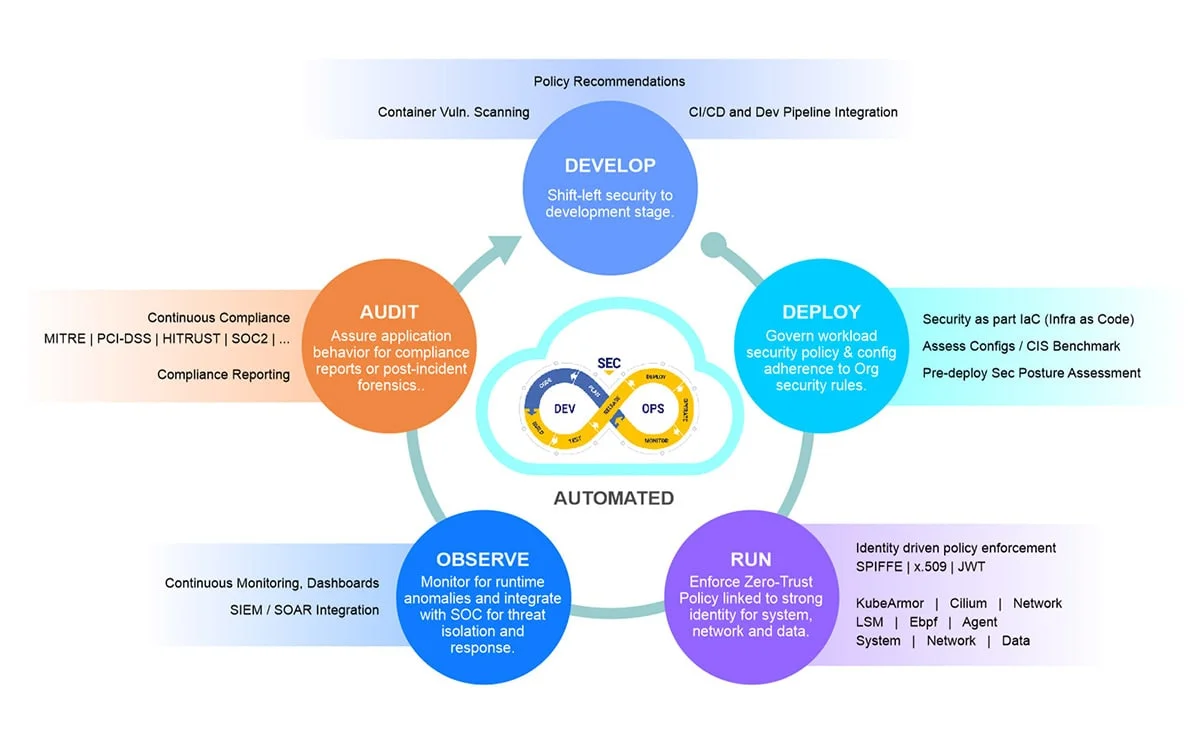
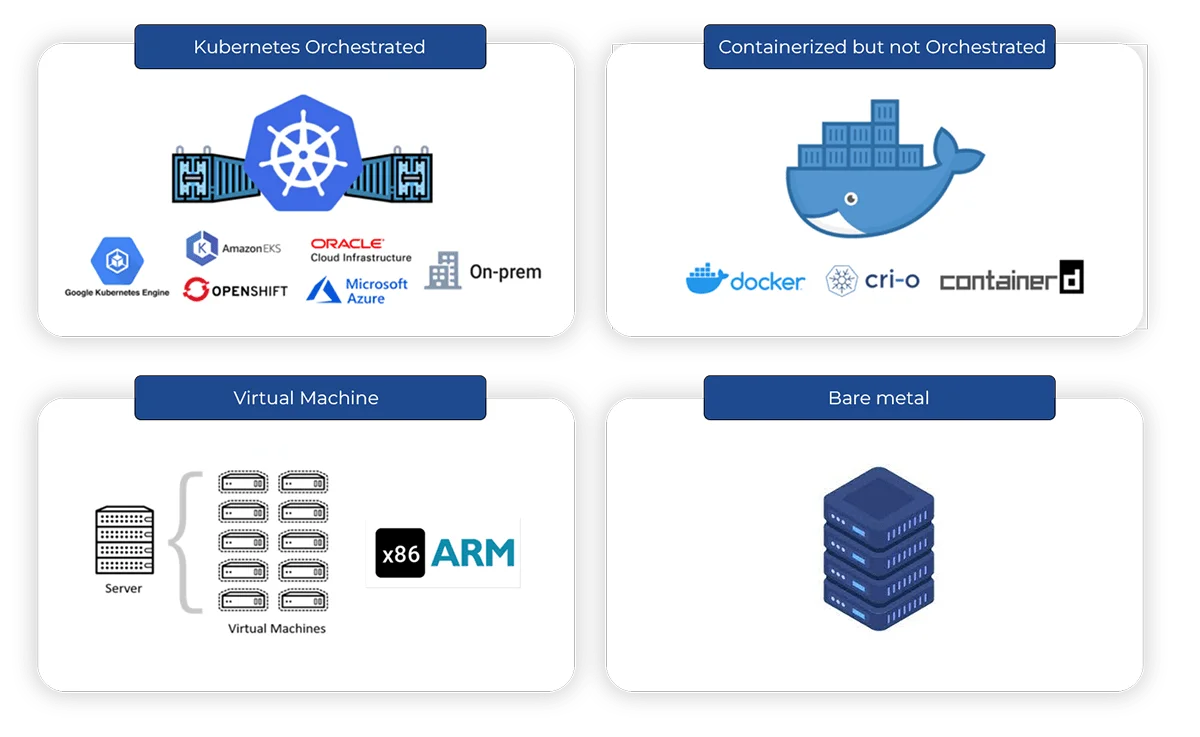
Deployment
- Deployment Options
- Public Cloud
- Private Cloud
Deployment Options
AccuKnox offers one of the most flexible deployment options: Public Cloud, Private Cloud, Multi-Cloud. We have one of the most flexible architecture which allows us to offer a durable roadmap that covers Zero Trust Security for IoT/Edge and 5G workloads.
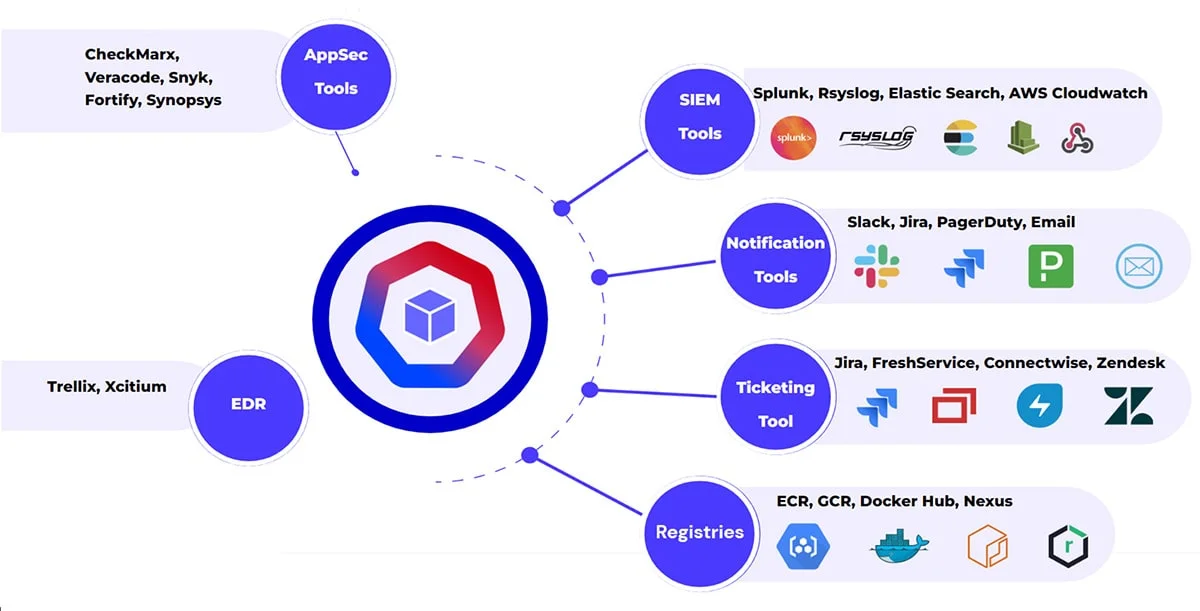
Integrations
This depicts the integrations we support. This is an ever-expanding list it takes us 2-4 weeks to support a new platform.
FAQs
Image scan: involves scanning individual images either from the CI/CD pipeline when the images themselves are created or through registries.
Registry Scan: Registry is a repository that contains a bunch of container images. Certain vendors allow only CI/CD-based scanning, while others allow CI/CD + registry scanning.
Our RAT tool is specific software that is deployed to check whether the configurations are correct/as per best practices.
E.g., if you scan an Ubuntu image, we will know if any vulnerabilities exist, but once the Ubuntu image is deployed and if it doesn’t use the right configuration (from best practices perspective), it is still open to attack.
Configuration is subject to change after the image is deployed and hence needs separate analysis. AccuKnox’s RAT uses best practices from DISA STIGs currently.
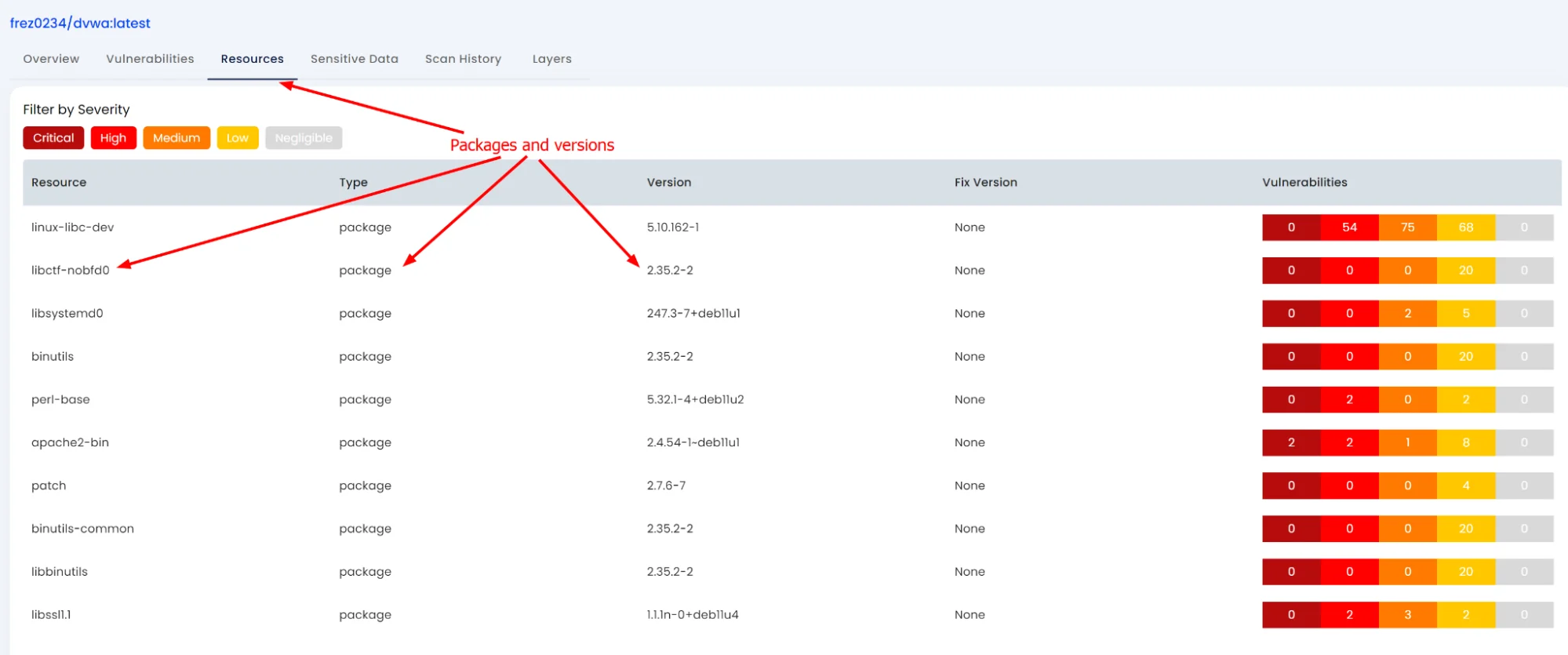
Getting a software composition as a whole and subsequently analyzing the Software composition.
Software composition refers to the breakdown of the software into individual layers, packages, modules, etc.
Subsequently, an analysis can be performed on it to check for risky modules, sensitive assets, license issues (for e.g., use of GPL components), etc.
Furthermore, the analysis could include user queries if a specific package is present across all the images/software they have deployed. The composition is shown as follows:
It becomes important to have a security solution that not just provides observability in different forms of deployment but can also provide real-time enforcement.
AccuKnox provides holistic security to Edge and 5G ORAN workloads in mission-critical deployments. Refer to https://www.accuknox.com/federal
You will get hardening policies via the AccuKnox enforcement engine AccuKnox.