Gen AI LLM Powered Agentless Cloud Security Posture Management (CSPM)
Continuously detect and remediate misconfigurations, and prioritize the most significant cloud risks from build to runtime across your public and private clouds - AWS, Azure, GCP, Alibaba Cloud, OCI, Redhat, OpenShift, VMware, and more.
GET CSPM DEMOBoost your enterprise cloud security posture & strategy with end-to-end visibility
AccuKnox CSPM (Cloud Security Posture Management) consists a set of advanced tools and applications that help your organization to monitor and manage cloud security posture. Our CSPM security leverages agentless technology to secure multi-cloud environments. Get enhanced visibility, risk, posture assessment, misconfiguration identification and compliance protocols with 360° CSPM security.
Gain complete visibility into your cloud security posture with CSPM security
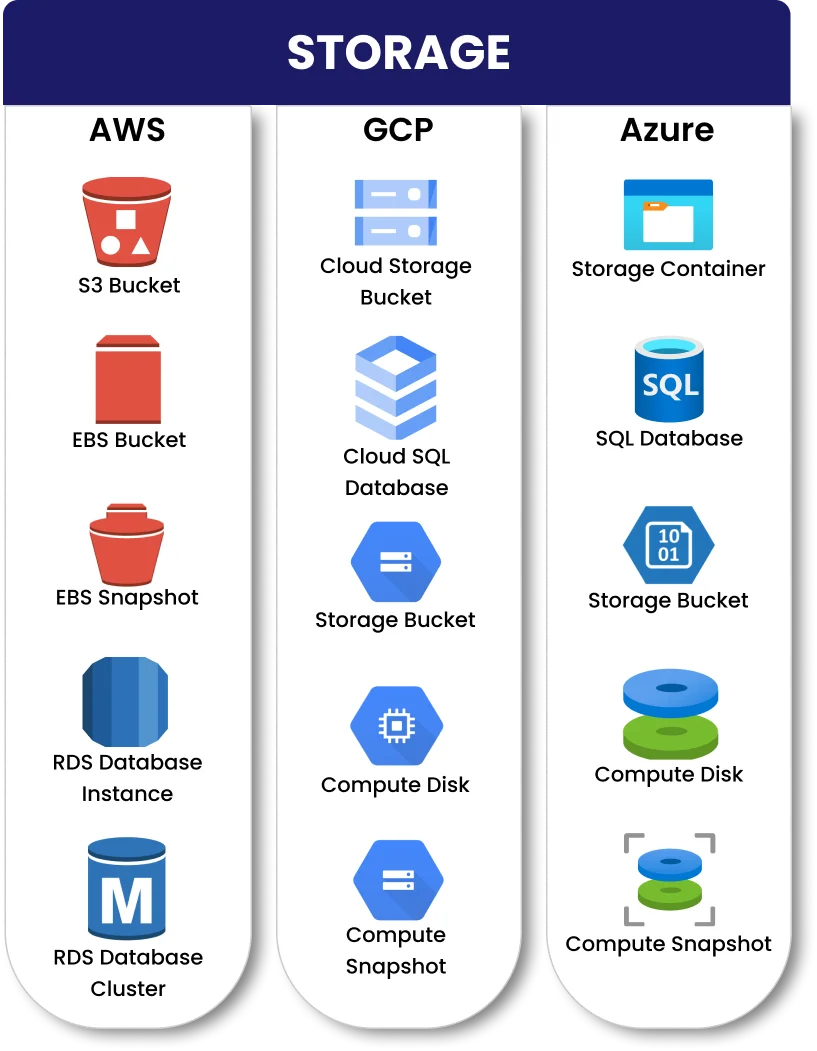
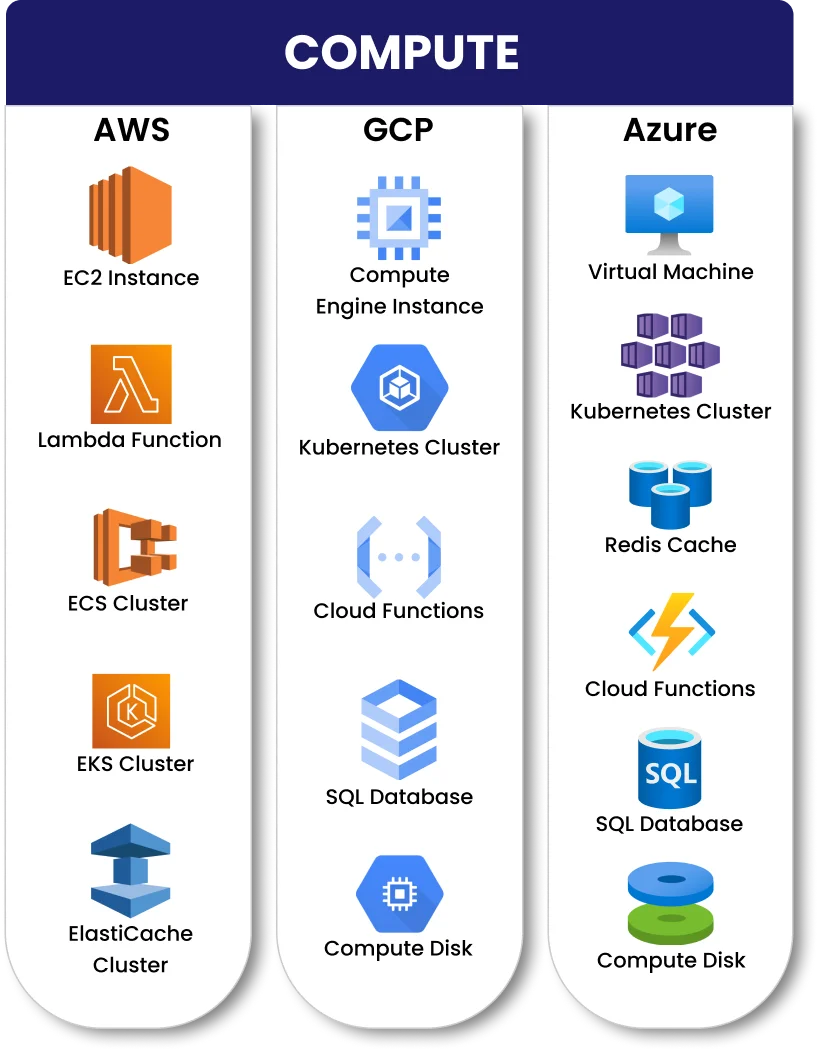
- Multi-cloud (AWS, Azure, GCP) asset inventory and misconfiguration detection.
- Prioritization of findings, integrated ticketing, and other channel integrations.
- Integrations with third-party tooling (open source and licensed) to augment the findings.
- Ability to scan the assets from the SaaS, on-prem, and CI/CD model.
- Ability to scan, and protect Kubernetes and other containerized environments using Zero trust policies, CIS, STIGs, MITRE, NIST.
- Runtime enforcement, Container security/forensics
- Kubernetes Identity and Entitlements management (KIEM)

Worried about cloud misconfigurations and vulnerabilities?
AccuKnox CSPM (Cloud Security Posture Management) consists a set of advanced tools and applications that help your organization to monitor and manage cloud security posture. Our CSPM security leverages agentless technology to secure multi-cloud environments. Get enhanced visibility, risk, posture assessment, misconfiguration identification and compliance protocols with 360° CSPM security.

How to Achieve Full Transparency of your Cloud Security Posture
Comprehensive CSPM for Compliance, Drift Detection & Monitoring
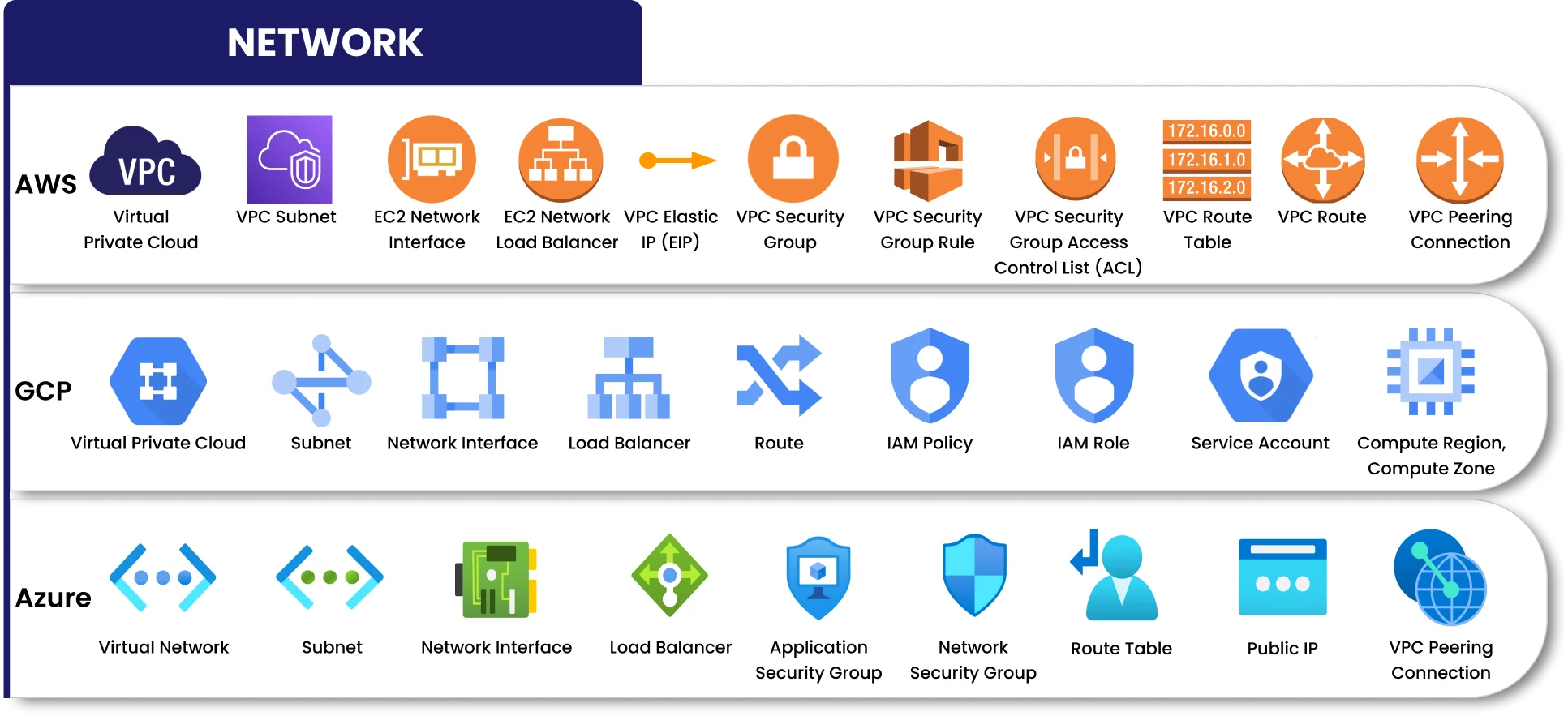
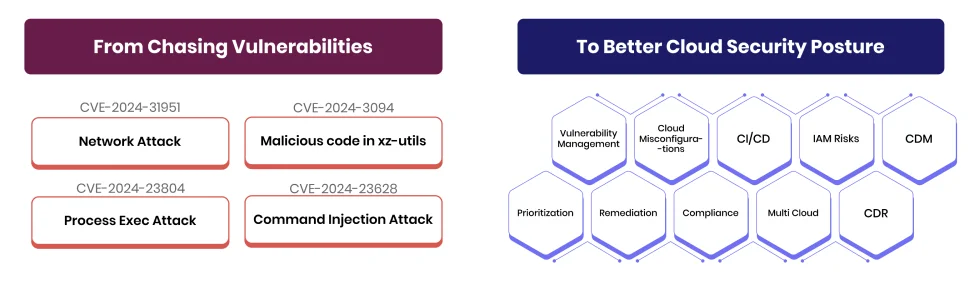
End-to-End Contextual CSPM Security
AccuKnox surpasses traditional CSPM solutions by offering a comprehensive security approach. Beyond just identifying, prioritizing, and fixing misconfigurations, AccuKnox empowers you with rich context surrounding each issue. This deeper understanding enables you to make informed decisions by providing a complete visibility of the associated risk profile.
- Cloud attack path analysis
- Prioritize network and identity exposure
- Complete context and cloud visibility into the Who/Where/What
- Scan for exposure to high-severity misconfigurations, compliance violations, and vulnerabilities.
- Automatic posture management, risk findings, prioritization and remediation
- Confidenty address regulatory compliance requirements with continuous monitoring
We are very pleased to partner with a Modern, Cloud Native, Zero Trust CNAPP innovator like AccuKnox. Zero Trust security is a commitment we have to our customers. Their work with AWS furthers the value that AccuKnox can deliver to us.”
Zero Trust security is Clint Health’s imperative and commitment we have to our customers. AccuKnox’s leading product combined with their successful track record of partnering with their customers forms the foundation for this objective.”
AccuKnox’s powerful combination of CSPM and CWPP; OpenSource foundations; In-line Zero Trust Security; Support for Public and Private Clouds; made them the ideal partner for us. Our client, a Large European Cyber Security agency, was looking for a Zero Trust Security Solution that supports Private Cloud platforms. Our win is a clear testament to the value our clients see in this partnership. We look forward to many more successes ahead.”
CSPM Pricing
Our pricing for the CSPM solution is based on the value delivered. CSPM tool pricing model depends on a few specific factors that exist in your cloud environment e.g. number of code repositories, workloads, assets, images, nodes etc.
Trusted By Global Innovators









Got questions on CSPM? We’ve you covered
Cloud security posture management (CSPM) is a set of products that continually manage IaaS and PaaS security posture by preventing, detecting, and responding to cloud infrastructure problems. The core of CSPM uses common frameworks, legal standards, and organizational rules to proactively and reactively identify and analyze the risk/trust of cloud service configuration and security settings. If a problem is detected, remedial options (automatic or manual) are presented.
According to Gartner’s research study, the most effective cloud service assaults are the consequence of client misconfiguration and mismanagement. CSPM is a set of solutions that aim to mitigate the risk of public cloud data or compliance breaches. Gartner has recognized CSPM as a new market segment for suppliers. The Magic Quadrant divides technology suppliers into four categories, whereas Critical Capabilities provides a more in-depth look at their services.
CSPM gives you insight across cloud environments, allowing you to swiftly discover and correct configuration issues through automation. CSPM tools monitor and mitigate risk across an organization’s whole cloud attack surface using both visibility and continuous monitoring.
Cloud security posture management (CSPM) is a technique for managing public cloud infrastructure risk that automates the detection and correction of misconfigurations across cloud resources such as Amazon EC2 instances. Its main feature is the continuous evaluation of cloud posture, which saves time, money, and resources by offering automatic and guided correction for small and frequent issues.
Consider CPSM best practices for securing a complex cloud environment, including –
- Strong identity and access control
- Continuous monitoring
- AI-driven threat detection
- Enterprise-wide incident response.
Strong passwords and safe access control rules can help to reduce the danger of stolen credentials. Continuous monitoring offers a complete picture of the external attack surface, enabling more effective risk management. AI-powered threat detection identifies harmful activity using deep learning and predictive analytics. An incident response strategy can assist prevent costly delays in detection and cleanup.
CSPM products are mostly used by security teams, compliance officials, and cloud administrators inside an enterprise.
CWPP tools are typically used by security teams, DevOps engineers, and cloud administrators. It protects against risks from misconfigurations, missing updates, and commercial threats from noncompliance.
CNAPP manages application scanning, runtime protection of apps, and security policies. It is implemented at the application level.
CSPM automates the process of identifying policy breaches and cloud configuration concerns.
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed