Future-Proof 5G ORAN Security
5GNAPP that delivers centralized security finely tuned for the demands of lightning quick 5G, simplifying risk assesment and policy enforcement.
SCHEDULE DEMO5GNAPP Vision
5GNAPP advocates for an all-in-one 5G-native management platform. The goal is to simplify the management of the security posture of 5G network assets. This draws inspiration from existing IP networks and cloud asset management principles. 5GNAPP aims to make 5G security management an intuitive and streamlined process.
Why 5G Security Matters?
5G enables New Architectures
- Increased Attack Surface
- Processing at the edge
- Distributed Arch, multiple layers/vendors
- Wide range of devices
- Use of general cloud providers
- Running mission critical apps

STREAMLINED FRAMEWORK FOR
5G/IOT SECURITY
Edge/5G Security Tooling
AccuKnox has partnered with SRI International to provide advanced 5G Security for a variety of deployment models.
Contact Support
Current Trends
- Incremental Firewall Improvements (e.g., NGFWs)
- Enhanced UE Security (USIM/UICC)
- Secure Transport for SBA
- CNAPP Migration for 5G Security
- Service Mesh Integration
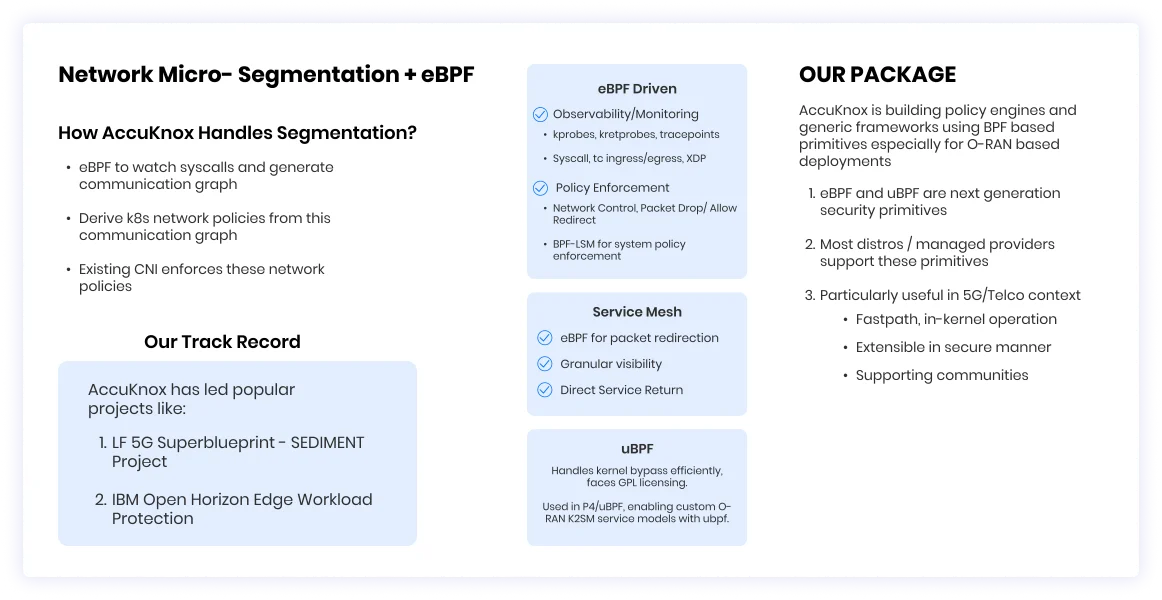
- Network Microsegmentation
- 5G-driven Architectural Evolution
- Federal Zero Trust Mandates
- Network Slicing Implementation
- Extreme Isolation in Shared Resources
- Multi-Cluster Deployments at Scale
5G Attack Vectors
| O-RAN Threats | AccuKnox Protection |
|---|---|
| T-O-RAN-01: Exploits insecure designs. | Advanced threat detection and containment measures, safeguarding against malware and unauthorized access. |
| T-O-RAN-02: Targets misconfigurations. | Enforces stringent configuration policies, minimizing the risk of misconfigurations and enhancing overall system resilience. |
| T-NEAR-RT-01: Explores malicious xApps. | Behavioral analysis to detect and prevent unauthorized activities, securing against malicious xApps and ensuring UE privacy. |

AccuKnox's enterprise CNAPP + 5G solution enhances network protection by implementing multi-layer security primitives and addressing the impracticality of manual deployment in distributed environments.
What We Deliver in 5GNAPP
The 5GNAPP management system is poised to deliver a spectrum of security functions. Each will play a fundamental role in fortifying the security of 5G networks:
- Validation of Configurations. Rigorous validation of SD-RAN Kubernetes configurations. Ensure that the network's infrastructure adheres to best practices and standards.
- xApp and RIC Security Compliance. 5GNAPP autonomously generates YAML policies for xApp and the NRT-RIC. Simplify compliance with security policies.
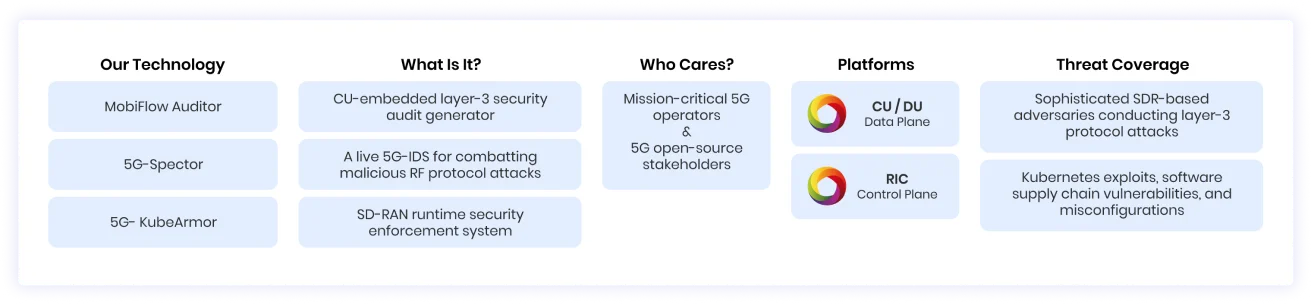
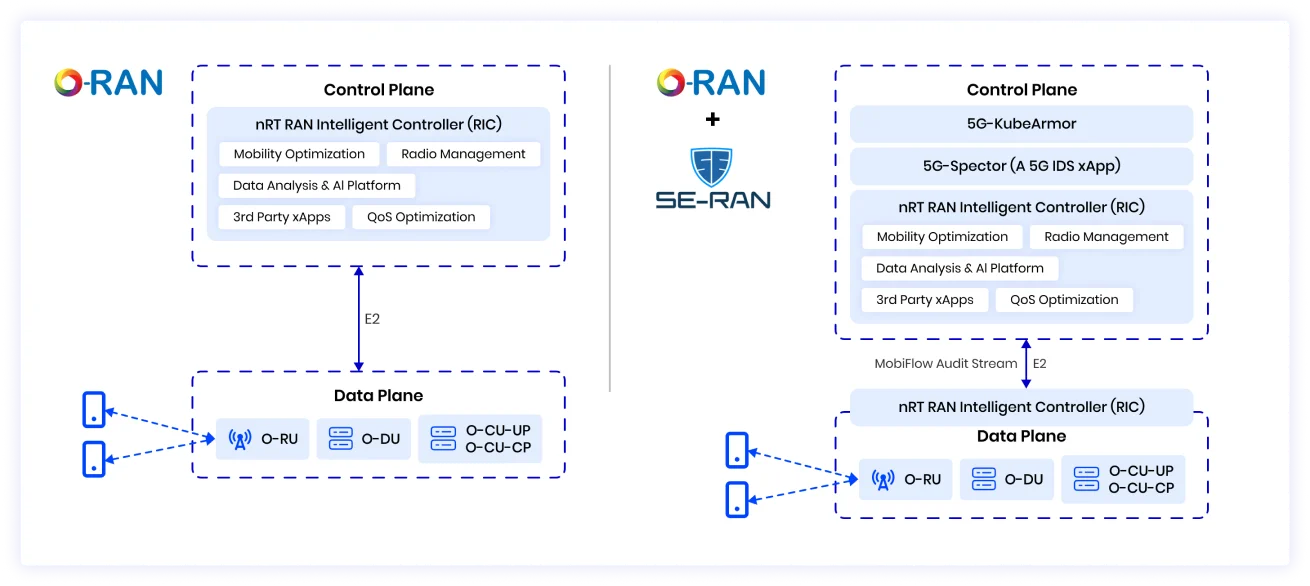
- Control Plane Compliance Enforcement. Leveraging 5G-KubeArmor, 5GNAPP aids in continuous monitoring of control plane policies. Prevent security breaches in real-time.
- Live RF-Threat Monitoring. By integrating 5G-Spector, the system offers real-time 5G Intrusion Detection System (IDS) analyses of MobiFlow security audit streams. Prompt detection of RF-based attacks and anomalies in RAN operations as they unfold.
- Governance of Audits. Consodilated report generation to capture vital security-relevant statistics at the base station layer. Security policy violations, warning alerts, RF-attack detection alerts from 5G-Spector, and summaries of SD-RAN configuration validations.

3.2 Billion
5G Connections by 2026
Research analysts and practitioners claim that the number of 5G connections is expected to skyrocket. Gear up with AccuKnox 5G Security Toolkit
Scenario Based Insights
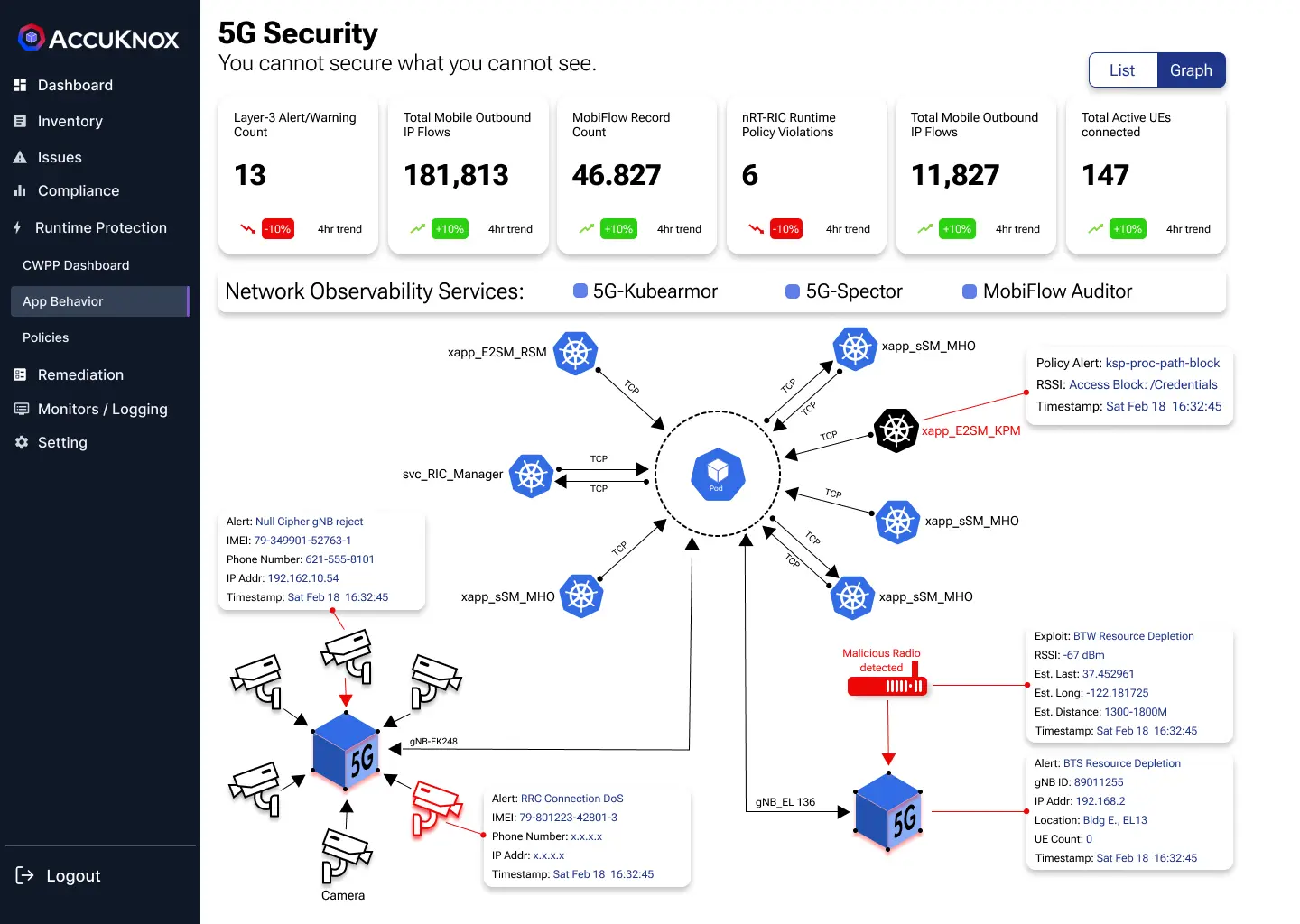
In a 5G network facing malicious actors, 5GNAPP's capabilities help monitor and manage security. MobiFlow Auditor provides insights into UE-to-base-station interactions, while 5G-Spector identifies hostile RF actors, offering real-time alerts. 5G-KubeArmor enforces application-layer security policies, adding a layer of defense. These components enable 5GNAPP to effectively monitor and manage the security of every asset within the network.
ACCUKNOX 5GKUBEARMOR
- 5G KubeArmor Integration: Enhanced 5G security with KubeArmor for robust protection.
- Istio-Nephio Integration: Seamless Istio integration with Nephio for advanced network security.
- OpenTelemetry Discovery-Engine: Discover/catalog API requests, auto-generate Istio policies.
- Rate-Control Policies: Discovery Engine enforces rate-control, alerts on excessive subscription requests.
- Extended Goal - Uprobes Traffic Discovery: Uprobes-based traffic discovery for heightened visibility.
ACCUKNOX 5GNAPP
- Consolidated Application Behavior View: Insight into RIC and UE behaviors in 5G networks.
- Entity Relationship Understanding: Identify and understand entity relationships for policy setting.
- Communication Pattern Showcase: Display UE + RIC communication patterns for informed decision-making.
AccuKnox in 5G/Open Communities
Multi-Layer Zero Trust Focus To Shield 5G Assets Across Multi-Cloud Workloads
- TSC Member for LF Nephio and LF Open Horizon.
- Recognized as an Intel Smart Edge Partner.
- Contributed Open Source Policy Templates for ENISA and MITRE FIGHT.
- Lead Maintainer for CNCF KubeArmor Project.
- Active involvement in 5GSec.com with collaborative efforts from AccuKnox, Stanford Research, and Ohio University.
- Acknowledged with NSF and DoD Awards for notable contributions in Research.
- Established partnership as a RedHat Telco Partner.
- Engaged in 5G-SBP (Smart Building Platform) and 5G Open Innovation Labs.
- Developed K8TLS Service Endpoint Scanner for enhanced Kubernetes security.

5G-Native Asset Protection Platform
Multi-Layer Zero Trust Focus To Shield 5G Assets Across Multi-Cloud Workloads
- Configuration management
- Least-permissive xApp/RIC policy generation
- Runtime compliance enforcement
- Runtime monitoring
- Threat response
- Audit governance