Cloud Native Runtime Security with Inline Prevention
Protect your cloud native applications, workloads, and software systems at scale from security vulnerabilities and threats during their execution with inline runtime security.
SEE RUNTIME SECURITY IN ACTION
“First-of-its-kind runtime security engine leveraging BPF-LSM at its core. Full Kubernetes (K8s) security including network micro-segmentation, Zero Trust policy discovery, workload hardening, and Kubernetes Identity and Entitlements Management (KIEM)”
Why is Runtime Security Imperative?
Your cloud-native apps demand a modern approach to security—one that is embedded and adaptive instead of reactive and outdated.
Rules and manual configurations left unmanaged quickly become irrelevant, leaving critical attack surfaces neglected and extremely vulnerable. AccuKnox Runtime Security takes the guesswork out of securing dynamic cloud environments with:
- Intelligent Guardrails that self-adapt access policies at runtime before misuse and exposure.
- 360° Infrastructure Mapping for continuous discovery across ephemeral environments. Know your terrain.
- Risk-focused alerting powered by embedded analytics to cut through the noise and focus on what matters most.
- Auto-Remediation Playbooks that codify and automate response procedures for consistent protection.
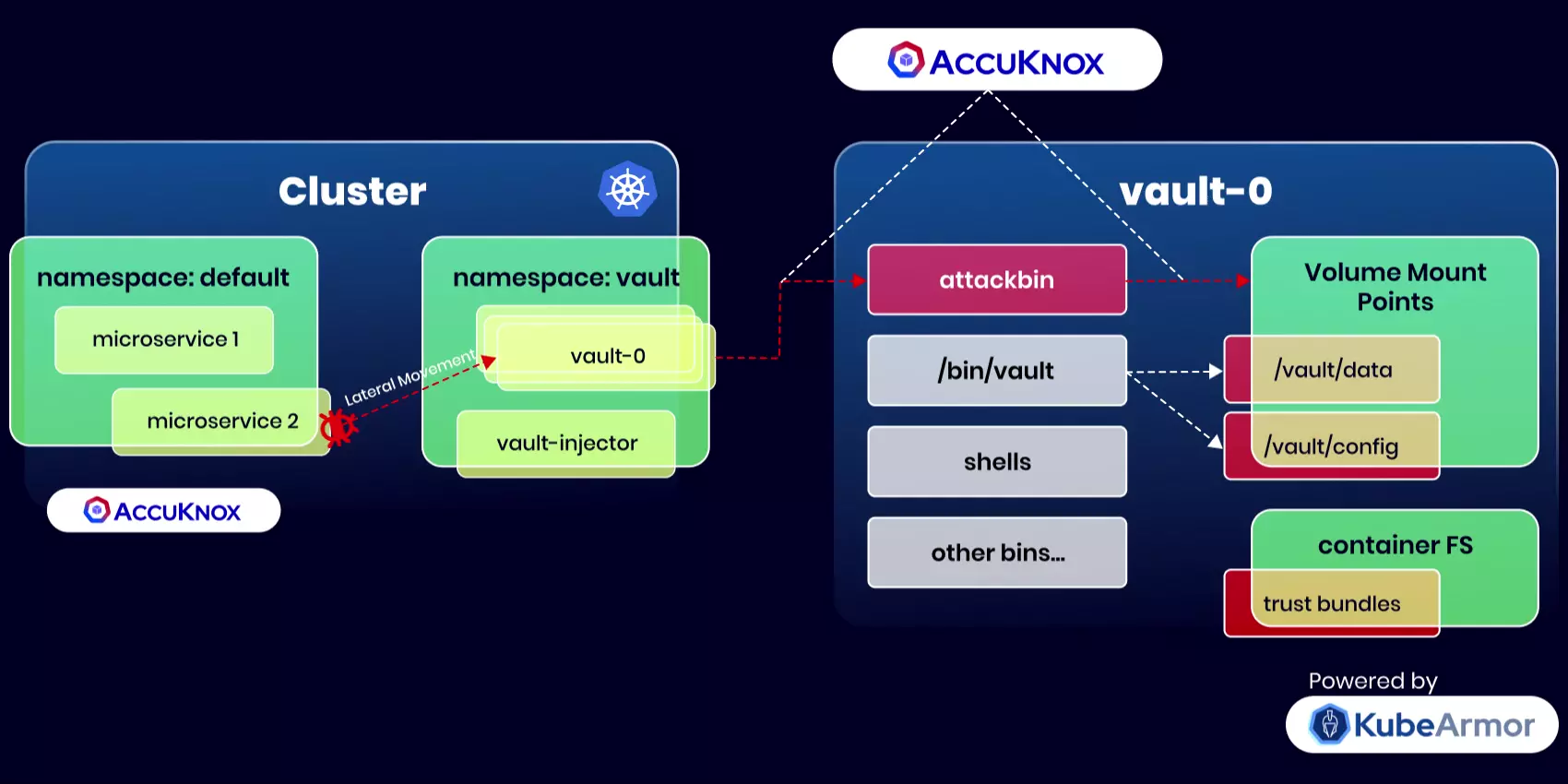
Secure your Secrets Manager
HashiCorp Vault Hardening
- Restrict access to HashiCorp Vault mount points in Pod
- Whitelist and provide fine grained access to ensure least permissive security controls
- Protect onprem Vault from advanced attacks (Ransomware, Bitcoin Miner, DDOS, etc.)
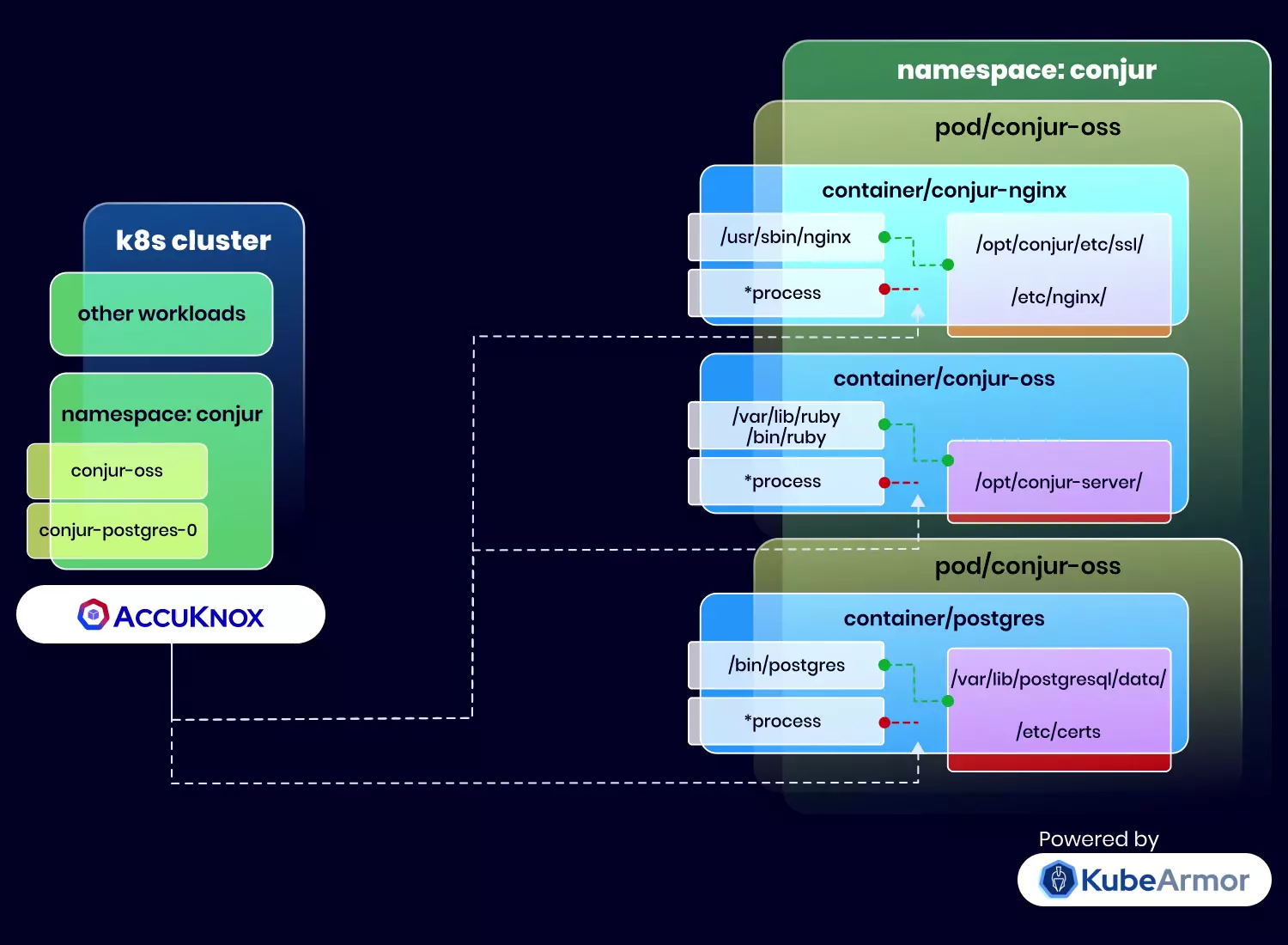
CyberArk Conjur Hardening
- CyberArk Conjur Hardening
- Allow access to certain paths only for certain process(es)
- Prevent Zero-Day attacks on mission-critical workload from insider-threats
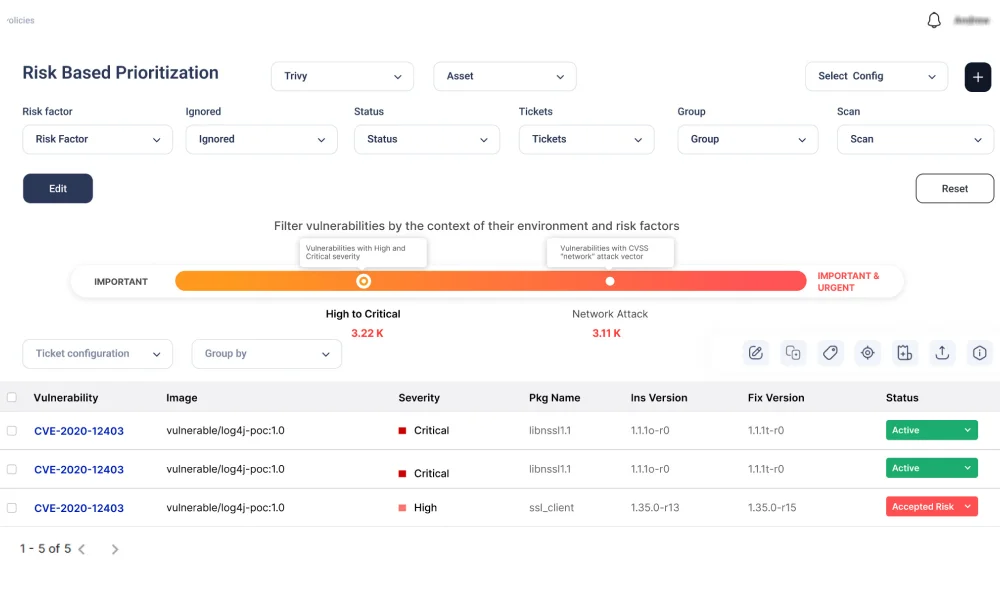
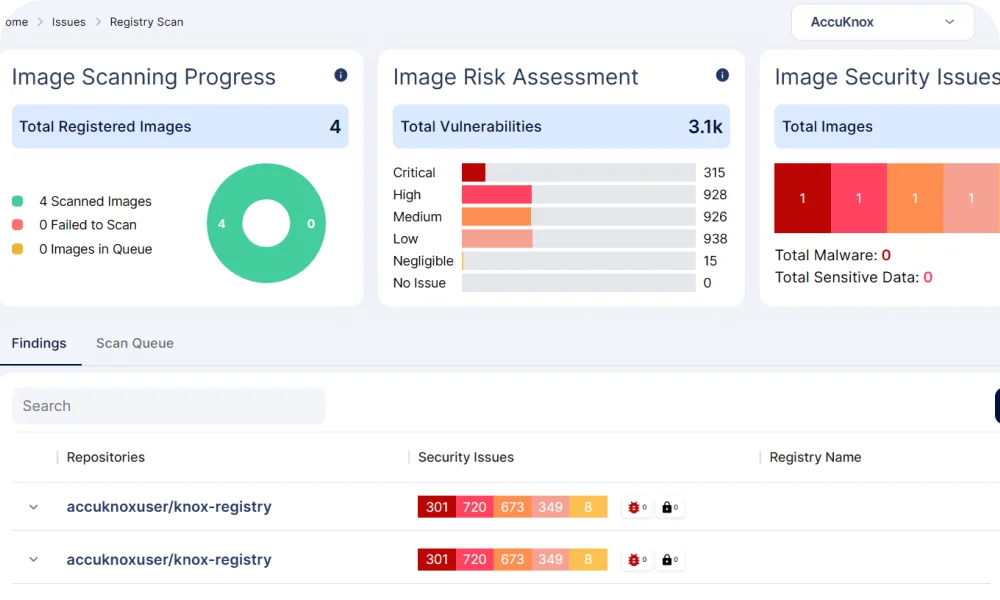
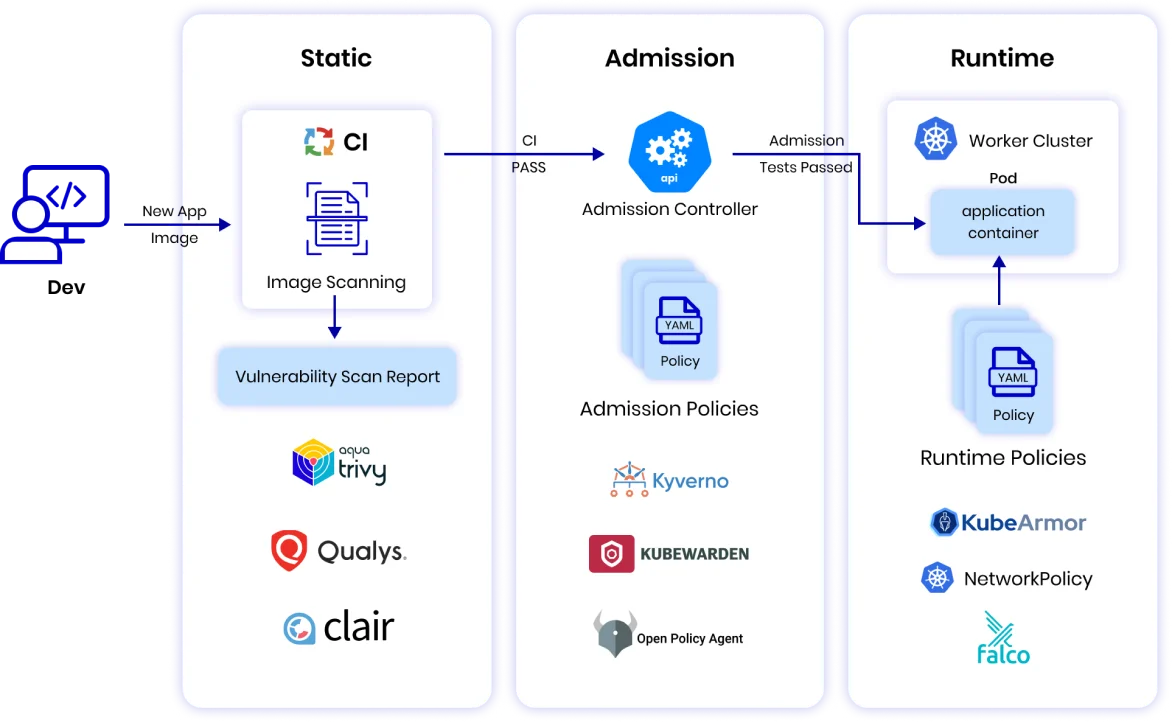
Build to Runtime Security
| Type of Scanner /Capabilities | Agents | Unauthenticated Network Scanner | Authenticated Scanner | Cloud Security Posture Manager | |
|---|---|---|---|---|---|
| Risk to Scanned Assets |
|
|
|
|
|
| Security Visibility Depth |
|
|
|
|
|
| Security Visibility Breadth |
|
|
|
|
|
| Vulnerability Detection |
|
|
|
|
|
| Malware Detection |
|
|
|
|
|
| INFRA, OS, Apps, & Data Inventory |
|
|
|
|
|
| Cloud Level Misconfiguration Detection |
|
|
|
|
|
| Scan Stopped Machines |
|
|
|
|
|
Stop Playing Catch-up with Yesterday's Threats
Runtime Security is an inseparable component of cloud workload protection. It focuses on protecting cloud-native applications while they are actively running in production environments. In essence, it is the last line of defense against cyber threats and vulnerabilities that may exploit weaknesses in an application during its execution.
Enterprises
Enterprises across various industries need Runtime Security to safeguard their cloud-native applications and sensitive data. Security breaches can have devastating consequences, including data breaches, financial losses, and reputational damage.
- Ensure Cloud-Native Application Security
- Prevent Data Breaches
- Avoid Financial Losses
- Protect Reputation
Cloud-Native Application Developers
Developers play a crucial role in ensuring the security of their applications during runtime. They need the tools and solutions to monitor application behavior and respond to potential threats effectively.
- Monitor Application Behavior
- Respond to Threats
- Implement Security Tools
Regulatory Compliance Team
Industries are subject to strict Governance, Risk and Compliance. Runtime Security helps organizations comply with these regulations, avoiding hefty fines and legal issues.
- Ensure GRC Adherence
- Avoid Fines & Legal Issues
- Maintain Compliance Documentation
Get total visibility into your cloud environment and pinpoint the most critical risks with intelligent and adaptive runtime security
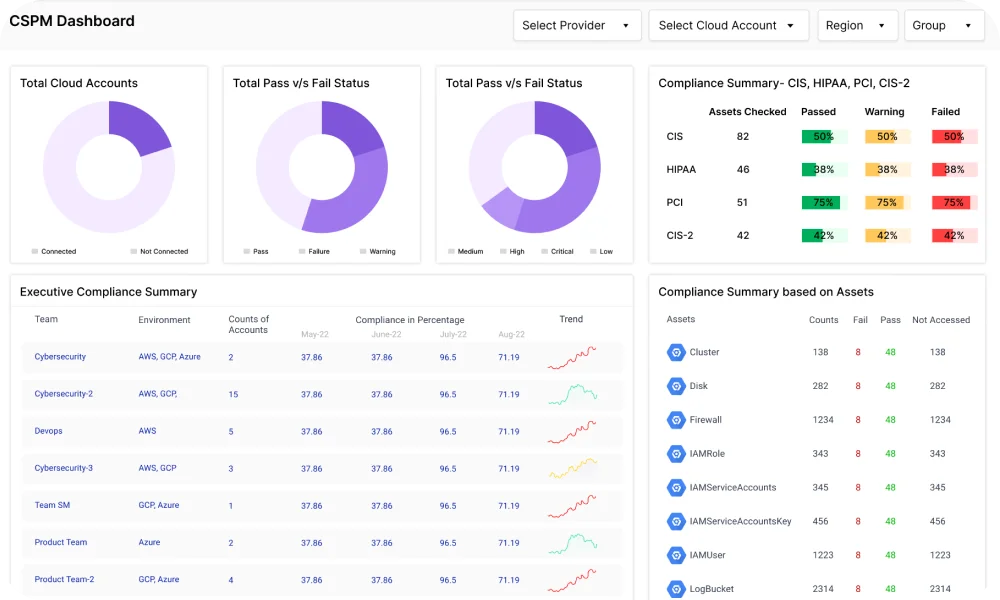
We’re at the forefront of the Zero Trust CNAPP Security. We provide an integrated approach to cloud security that combines:
- Agentless Cloud Security Posture Management (CSPM)
- Kubernetes Security Posture Management (KSPM)
- eBPF + LSM Powered Cloud Workload Protection Platform (CWPP)
Here’s how our Zero Trust cloud security solutions help organization’s achieve inline runtime security.
Automatic Zero Trust Policies
This ensures that only authorized entities gain access to cloud-native applications.
Comprehensive Reporting
Ability to generate deep-scan security reports and audits. Unmatched visibility into application’s security posture.
Application Behavior and Workload Hardening
Both these features are accessible via a centralized dashboard to measure risks and proactively protect against threats.
Network Microsegmentation
The platform facilitates network micro segmentation. This accelerates the isolation of critical application components.
SIEM/SOAR Integrations
We offer the ability to integrate with SIEM and SOAR platforms. This means elevated threat detection and response capabilities.
Multi-Cloud Support
Our multi-cloud, multi-cluster, and multi-tenant SaaS model ensures flexibility and scalability for diverse cloud-native environments.
| Cloud Security | Static Security | Runtime Security |
|---|---|---|
| CSPM (Cloud Security Posture Management) | Utilize CSPM tools for security compliance assessment | Continuously monitor and enforce security policies |
| CWPP (Cloud Workload Protection Platform) | Harden cloud-native workloads and components | Secure workloads against vulnerabilities and threats |
| Securing Secrets | Secure handling and storage, encryption, access control | Strong identity and access management, regular rotation |
| 5G Security | Develop with 5G security considerations | Implement 5G-compatible security measures |
| Compliance & Reporting | Create compliance policies aligned with standards | Continuous compliance checks, reporting, remediation |
| Policy as Code | Create security rules as code, integrate into SDLC | Consistently implement policies through automation |
| Zero-Day Attack | Use proactive methods, e.g., threat modeling | Install intrusion detection and prevention tools |
| DevSecOps | Integrate security into DevOps pipeline | Continuously monitor and evaluate security |
| Deployment | Create secure deployment pipelines, automate processes | Implement runtime deployment security controls |
| Integrations | Plan and implement security integrations | Continuous monitoring and management for security |
Use Cases of Runtime Security
- Runtime Application Behavior - Observability
- Simplified Cloud Container Security
- Detect Container Vulnerabilities and Threats at Runtime
- Streamline Compliance and Governance
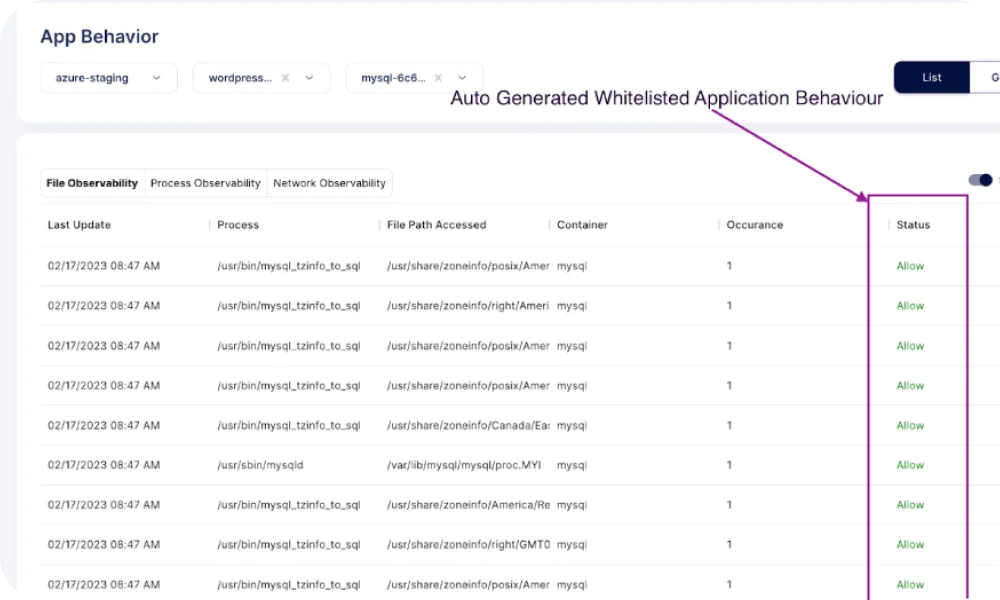
Runtime Application Behavior – Observability
- File Observability provides information about file access within the pod (including the process of accessing the file and its status).
- Process observability shows all processes executing in the pod, including pods or containers, and any processes that are blocked from execution.
Got questions on runtime security? We've got you covered!
Runtime security protects cloud applications in production by guarding against exploits and attacks in real time during execution. It’s the last line of defense for cloud workloads operating in the public cloud, private cloud, and hybrid environments.
The main types are host-based and application-based runtime security including:
- Container Runtime Security – Secures the container runtime environment and infrastructure that containers run on top of. Very critical for fortifying containers.
- Kubernetes Runtime Security – Ensures pods and services are configured correctly. Focuses on securing the Kubernetes container orchestration runtime environment.
- Cloud-Native Application Runtime Security – Secures cloud-native applications while running, through policies, encryption, monitoring, and other controls. Deals with dynamic cloud environments.
Use least privilege access, enable anomaly detection, monitor service accounts activity, implement runtime application self-protection checks, turn on API security, enable runtime encryption, integrate with a CWPP, and automate policy enforcement.
CWPP provides unified security across build, deploy and runtime stages. Runtime security is a key component of a modern CWPP to protect production workloads across public, private, and hybrid clouds.
- Hardening host OS
- Securing identities
- Enabling logging
- Masking data
- Microsegmentation rules
- Vulnerability management
- Firewall policies
- Integrating runtime security into CI/CD pipelines.
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
Total Exposed Attacks in 2024 Costed