Data is the New Oil
Data is new oil Don’t let it become your Plutonium, Welcome to Zero Trust Data Security! I presume you were shocked by Amazon’s fine of $888M for EU Data Violations. Granted this amount is < 0.5% of Amazon’s market, and Amazon can comfortably deal with this, most companies cannot deal with a challenge that is […]
Reading Time: 4 minutes
Table of Contents
Data is new oil Don’t let it become your Plutonium, Welcome to Zero Trust Data Security!
I presume you were shocked by Amazon’s fine of $888M for EU Data Violations. Granted this amount is < 0.5% of Amazon’s market, and Amazon can comfortably deal with this, most companies cannot deal with a challenge that is a fraction of this.
As if this was not bad enough, in the last few days T-Mobile announced that 40 Million of their customer records were compromised.
Both Amazon and T-Mobile are world class organizations with “best in class” IT and Security teams. We would shudder to think of what is in store for an average or sub-par organization.
It is amply obvious that consumers are taking their data privacy very seriously. And as you would expect regulators are taking note. Very
comprehensive regulatory frameworks like GDPR, CCPA are a natural consequence of this. And Cyberthreat actors too. Willie Sutton, the infamous bank robber when asked why he robbed banks quipped “Because that’s where the money is”!. Cyberthreat actors I suppose will have a similar response.
So why is this such a big problem? Data related challenges include:
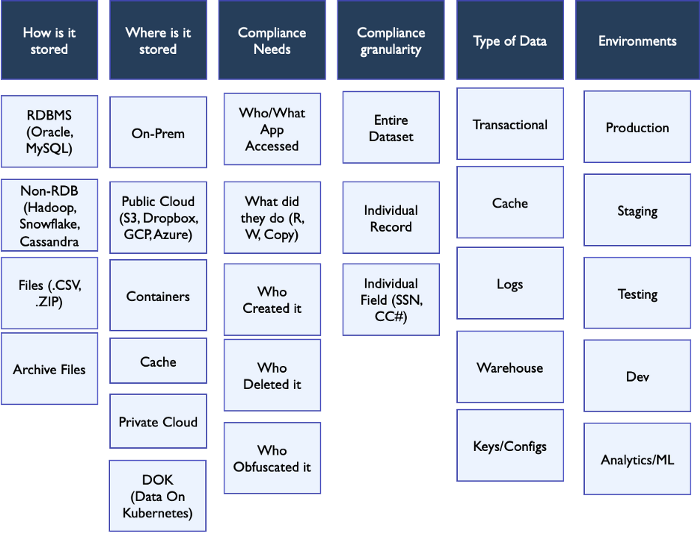
Data is no longer in Relational Databases. In fact, more data resides outside RDBMS
Cloud migration is making the data even more dispersed — On-premises, Private Cloud, Multi-Cloud (given that a recent survey indicates that over 92% of enterprises plan to adopt a multi-cloud strategy)
Migration to microservices is driving democratization of the data
Need for access restrictions are becoming stricter given the regulatory pressure
ML/AI research is creating new environments where data is being copied
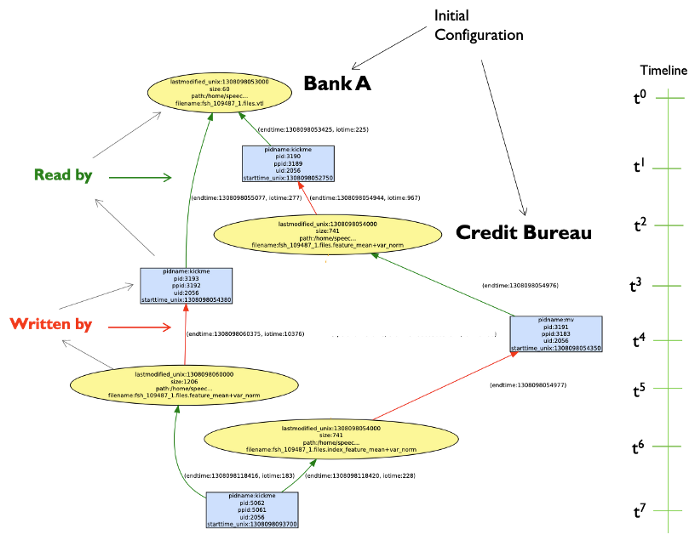
In essence, data is dispersed, distributed, diverse and hard to track, manage, monitor. As the age-old adage in security goes, “you cannot manage something you cannot monitor”. This is outlined in the following graphic
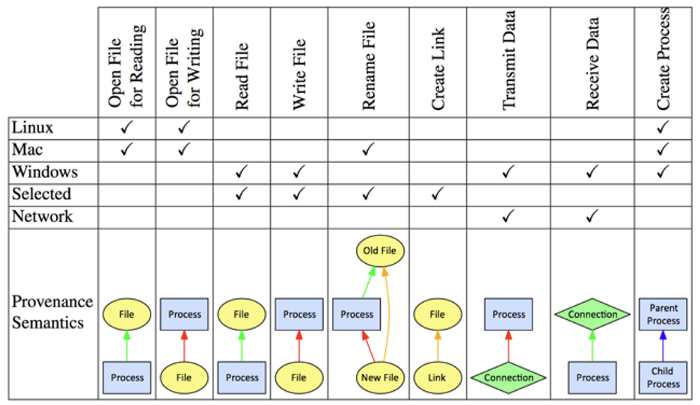
AccuKnox Data Security is anchored on over 10 years of seminal research at SRI International, in the area of Data Provenance [1].
AccuKnox Data Provenance engine provides answers to the following questions:
▪ Which process [e.g., app] was used to create this data object [e.g., file]?
▪ When the process ran, what were the other data objects it wrote?
▪ What data objects did the process read?
▪ Could any data have flowed from this data object to that data object which is untrusted?
▪ What is the sensitivity of a given data flow or connection between processes?
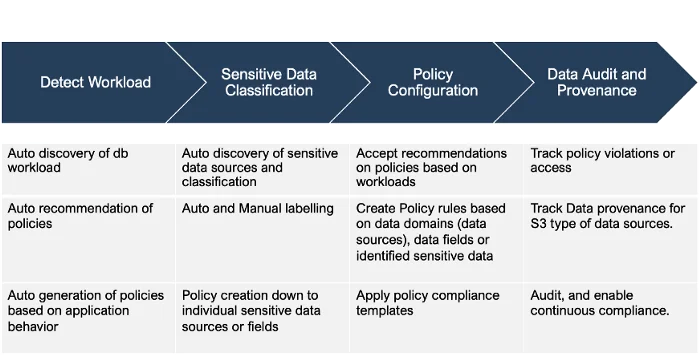
AccuKnox is a very comprehensive Data Security platform that allows organizations to deal with current and emerging Data Security challenges.
It allows organizations to get a full audit trail of their sensitive data
Gartner shares our thoughts on the current data challenges faced by most companies and governments.
“Organizations face huge challenges recovering from the impacts of the 2020 global crisis, new work-from-home strategies, and the faster adoption of hybrid and multi-cloud services. A data security strategy must address increasing risks associated with data residency, privacy and malicious activities” Gartner 2020
Amazon and T-Mobile find themselves in an unenviable position. Both are top flight organizations with world class IT and Security Departments. We would shudder to think what in store for an average, middle-of-the road Acme Corp. A strategic asset like Data (Oil) if not appropriately managed can quickly turn into a liability (Plutonium). “Fortune favors the prepared mind”, said Louis Pasteur. As it pertains to Cybersecurity and in particular Data Security, a Zero Trust posture and advanced platforms like AccuKnox can help organizations be better prepared to detect, thwart, and combat current and emerging threats.
With AccuKnox, you are prepared to answer the foundational questions regarding your data such as –
- Where is my data and how is it stored?
- Which parts of my data are sensitive and require protection to achieve what compliance standards?
- Which user, what process, which application, which micro-service has access to what data?
- Is all my data of similar sensitivity being protected with same level of restrictions regardless of where it resides and how it is stored?
- While I am sure access to the data from the application layer is protected, can I be sure about the access from system level?
- AccuKnox helps you answer this and many, several questions that organizations are unprepared or underprepared to answer.
References
[1] Scaling SPADE to “Big Provenance”, Ashish Gehani, et al.
Authors
Nat Natraj is the co-founder/CEO of AccuKnox.
AccuKnox provides a Zero Trust Run-time Kubernetes Security platform. AccuKnox is built in partnership with SRI and is anchored on seminal inventions in the areas of: Container Security, Anomaly Detection and Data Provenance. AccuKnox can be deployed in Public and Private Cloud environments. Visit www.accuknox.com or follow us on Twitter (@accuknox).
Nagi Prabhu is a seasoned Tech Leader with a successful track record of delivering $3B+ in Market Value. He advises AccuKnox and other innovators in the areas of Product Strategy in the areas of SAAS, Data, Cloud, etc.
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
Total Exposed Attacks in 2024 Costed