Top 10 Emerging Cybersecurity Threats. 2030 DevSecOps Radar.
Explore the latest cybersecurity threats that affect DevSecOps teams and the risks associated with software dependencies that compromise the supply chain.
Reading Time: 9 minutes
Table of Contents
Modern software development focuses on DevSecOps, merging development, security, and operations. DevSecOps aims to create secure software by integrating security throughout development. It’s important to keep up with changing cybersecurity threats. Security professionals must stay ahead as threats evolve.
This article explores major cybersecurity risks expected by 2030. Understanding these up-and-coming threats eases the adoption of active measures to reduce risks.
Software Dependency Compromise in the Supply Chain
Software Dependency Compromise in the Supply Chain refers to the security risks associated with third-party software components and dependencies used in software development. It highlights the vulnerabilities that can arise when organizations rely on external libraries, frameworks, or modules that may contain malicious code or have security flaws.
These dependencies, if compromised, can serve as entry points for attackers to gain unauthorized access, steal sensitive data, or introduce malicious functionality into software systems. Such compromises can occur at various stages of the software supply chain, including during development, distribution, or deployment.
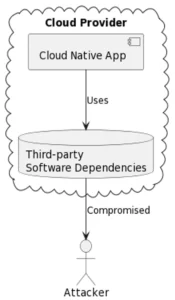
- During the SolarWinds attack, a backdoor was inserted into software updates.
- Another attack targeted Codecov, giving hackers access to sensitive data.
Can you imagine the impact on organizations, including government agencies?
Compromised software dependencies lead to serious consequences. Think about data breaches that result in financial loss and damage to reputation. What if attackers gain control over critical systems? And don’t forget the danger of spreading malware through compromised dependencies. Plus, supply chain disruptions cause delays and frustration for businesses and customers.
How do organizations reduce the risks of supply chain compromise?
Focus on a proactive approach.
- ☑ Start with comprehensive vulnerability scanning and continuous monitoring of dependencies. Install strict access controls and verify the integrity of software components.
- ☑ To secure distribution channels, build trusted partnerships with vendors.
- ☑ Conduct regular security assessments.
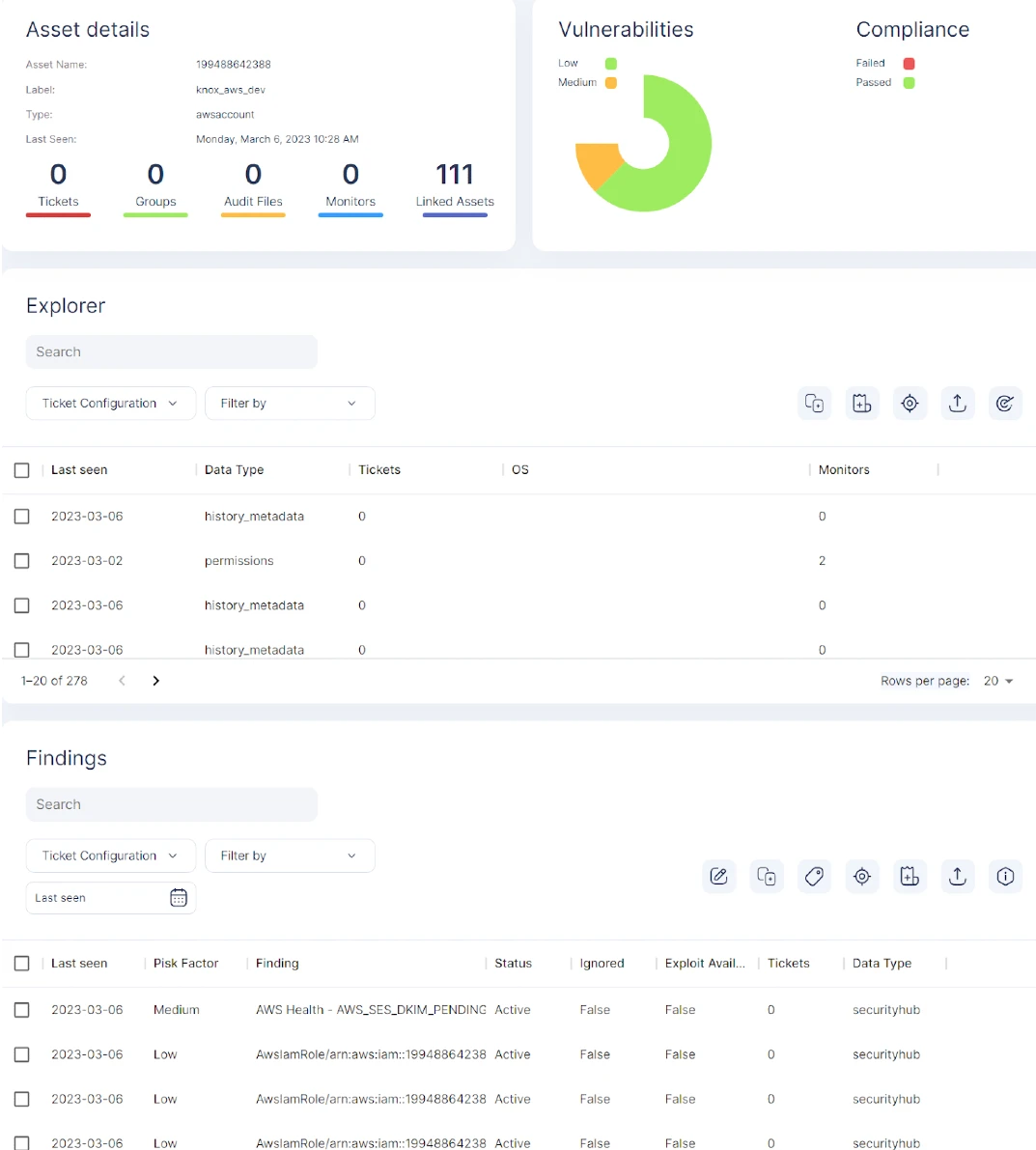
Our Cloud Native Application Protection platform offers a comprehensive way of detecting vulnerabilities and dependencies in the open source packages through both static and dynamic security. Our CSPM tool scans the infrastructure and saves the scan data in S3 buckets where we query regularly to prioritize and de-duplicate vulnerabilities detected.
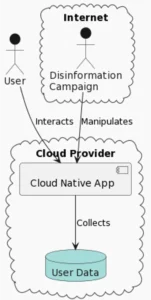
Modernized Disinformation Campaigns
These campaigns involve spreading false information on purpose. The intent is to manipulate opinions or gain an advantage.
In DevSecOps, disinformation campaigns cause serious trouble. They target your organization, employees, or customers with false information to create chaos. Erosion of trust and disruption of operations leads to enormous losses.
Bad actors use different tactics in advanced disinformation campaigns. They:
- ➞ Create fake social media accounts
- ➞ Spread manipulated content
- ➞ Exploit controversies
- ➞ Trick and deceive people using social engineering techniques
Adopt the ZT security mindset. Believe nothing until the source is validated. Stay watchful and combat these disinformation campaigns.
To tackle disinformation threats, there are a few recommendations to consider.
- ☑ Educate your employees about media literacy and critical thinking. This will help them spot false information.
- ☑ Set up strong monitoring systems to detect suspicious activities and content.
- ☑ Develop incident response plans for disinformation incidents.
The world of disinformation campaigns keeps changing, posing big challenges for organizations. While this is not a novel threat, its likelihood paired with impact is worrying.
Authoritarianism and Privacy Loss in the Rise of Digital Surveillance
How to ensure compliance with regulations? How to protect customers’ privacy in this surveillance-driven landscape? These are the questions security professionals must consider.
Digital surveillance has prevailed, and it’s leading to a significant loss of privacy. Governments and organizations are monitoring online activities. Which raises concerns about your freedoms.
If you’re adopting DevSecOps practices, digital surveillance has a big impact. Surveillance risk increases as sensitive data and operations move to the cloud. Professionals must consider how surveillance affects infrastructure, applications, and data security.
How to protect against these risks and maintain your privacy?
- ☑ Have strong encryption practices.
- ☑ Establish access controls and authentication mechanisms.
- ☑ Track and audit access to sensitive data, and follow privacy regulations.
- ☑ Prioritize data privacy and security throughout the development and deployment.
This will earn the trust of your stakeholders—especially in this age of increasing digital surveillance. AccuKnox assesses security infrastructure, analyzing cloud health and compliance. Our dashboard generates reports on compliance risks and vulnerabilities. It supports technical compliance and legal governance with popular frameworks (STIG, CIS, NIST CSF, HIPAA, MITRE, etc.). This will definitely add value to compliance and reduce the friction of surveillance.
Cyber-Physical Ecosystems: Human Error and Exploited Legacy Systems
Human Errors lead to vulnerabilities in cyber-physical systems. Hackers exploit errors like incorrect setups, ignorance, or inadvertent activities. Let’s investigate these dangers to learn more about their implications.
Compromised legacy systems threaten cyber-physical ecosystems. These antiquated systems lack robust security safeguards. This makes them attractive targets for attackers. To guarantee thorough security planning, study the risks related to older systems.
How do you avoid all this hassle?
- ☑ Train your employees on security procedures and potential hazards.
- ☑ Assess and audit your systems to identify legacy system vulnerabilities.
- ☑ To address known vulnerabilities, install security patches and updates.
- ☑ Use a layered defense approach with intrusion detection and prevention systems.
Human errors have existed ever since the launch of the digital age, so this is nothing new. But the complexity of cloud-native deployment is daunting. Single points of failure are only growing in number, which is why we wanted to point your attention to this issue. Take action now to safeguard yourself against common vulnerabilities and exposures.
Targeted Attacks Enhanced by Smart Device Data
Malicious parties use smart devices to sneak in and orchestrate attacks like ransomware. Their objective is to get into your private data store. Hold it hostage. And charge you for recovery. Do you know how they’re using smart device data to make their attacks stronger?
When smart devices get taken over, it’s a big problem for your DevSecOps setup. These devices, like IoT gadgets or phones, connect to your cloud apps and give hackers a way in.
Start beefing up smart devices in your DevSecOps setup with these tips:
- ☑ Manage your devices. Keep track of everything that falls under your domain.
- ☑ Use strong passwords, keep them updated, and check for any breaches. Use modern encryption like RSA.
- ☑ Separate your smart devices from critical assets in your network. This limits their performance and functionality.
- ☑ Use an automated system that watches for anomalies. And don’t forget to teach your team about the risks and how to be safe.
Finding weak links in your system from the perspective of the hacker allows you to have a stronger DevSecOps setup. Take action, use smart strategies, and stay on the lookout to keep your important information safe from sneaky attacks. This is where we’d like to introduce you to our on-prem installation guide. For some security professionals, it is the go-to approach.
Lack of Space-Based Infrastructure Analysis and Object Control
Industries relying on space systems, like telecom and navigation, face unique challenges. These risks in space tech are projected to advance in 2030. Vulnerabilities in space assets disrupt data transmission and operations and cause financial losses.
Imagine a telecom company relying on satellites for global communication. If assets lack analysis and control, unauthorized access and disruptions could occur. Moreover, they cannot make heads or tails of their consumer base. This harms finances, reputation, and security.
How can you tackle these challenges while keeping a focus on securing the future?
- ☑ Use strong authentication and encryption for space communication.
- ☑ Assess vulnerabilities and watch assets for threats.
- ☑ Have data replicated and duplicate images. Compliance. Availability. Reliability.
Collaborate with space agencies and experts for emerging practices. Invest in security and partnerships to mitigate risks and protect operations.
Try out our tools to manage vulnerabilities as part of CSPM, such as flagging false positives, waiting for third parties to take action, accepting risks, and more. It also offers compliance reports for 3PAO auditing based on different security governance. This helps to take corrective action and meet SLA requirements.
Rise of Advanced Hybrid Threats and Unanticipated Modus Operandi
Advanced hybrid threats are becoming a growing concern. To target cloud-native apps, attackers use social engineering, malware, and cloud vulnerabilities. To mitigate the impact of these threats on security, you must first understand them.
| Threat Type | Impact |
| Phishing Campaigns |
|
| Malicious Code Injection |
|
| Synergy between Threats |
|
Finance, healthcare, and e-commerce are all affected by hybrid threats.
- ☑ To prevent unauthorized access, use multi-factor authentication and strict access controls.
- ☑ Regular security assessments and penetration testing identify and address vulnerabilities.
- ☑ For early detection, deploy advanced threat detection systems such as behavior analytics.
Adopt preparedness strategies to combat advanced hybrid threats. Discard legacy tools. Embrace end-to-end security. Zero Trust is our recommendation! Tackle this head-on and fearlessly with AccuKnox. We provide state-of-the-art anomaly detection.
Cybersecurity Skill Gap
The industry faces a critical challenge: a shortage of skilled cybersecurity professionals. Recent studies show a global shortage of 3 million experts. This puts cloud native apps at risk from emerging threats. Addressing this gap is crucial to protect apps and data.
The lack of cybersecurity skills impacts DevSecOps teams and security practices. Research shows high demand (68%) but low talent availability (35%). This disparity makes apps vulnerable to malicious actors.
- ☑ A practical approach will bridge the skill gap and build a strong cybersecurity workforce.
- ☑ Continuous training and upskilling enhance the team’s capabilities.
- ☑ Collaboration with educational institutions and training providers brings in fresh talent.
- ☑ Automation and AI technologies boost security capabilities, reducing staff workload.
Promoting diversity and inclusion in cybersecurity is essential. Diverse teams are more innovative and better equipped to tackle challenges. Embracing diversity strengthens cybersecurity defenses. Investing in a resilient cybersecurity workforce safeguards our digital assets. Skilled professionals are critical in this evolving threat landscape. But due to scarce knowledgeable resources, the problem of securely fortifying cloud native applications is only getting worse.
| As Gene Spafford said, “The only truly secure system is one that is powered off, cast in concrete, and sealed in a lead-lined room with armed guards.” |
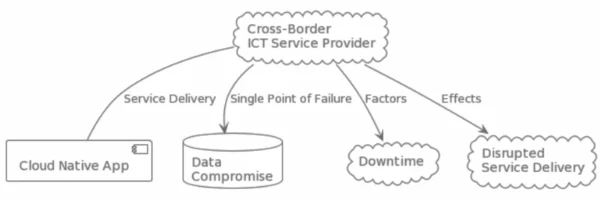
Single Points of Failure for Cross-Border ICT Service Providers
58% of organizations have already experienced a third-party breach. For example, Equifax’s data breach compromised millions of records. Diversify providers by using multiple options like AWS, Azure, and Google Cloud.
Relying on one provider risks disrupting service and app security. A single point of failure instantly disrupts service delivery, jeopardizing cloud native apps. Third-party breaches impact operations, causing downtime and data compromise.
- ☑ Reduce reliance on a single provider to distribute the risk.
- ☑ Always be monitoring and auditing service providers’ security practices.
- ☑ Eliminate risk by diversifying providers, monitoring security, and implementing strong controls.
AccuKnox has multi-cloud, multi-environment support so that you do not have to juggle. With us, you can analyze everything with an aggregated dashboard view. This aggregated view reflects data from across all your distributed cloud native applications! Imagine how much overhead and manual work that cuts down.
Understand risks, implement strategies, and safeguard cloud native apps globally. Remember: “Without aim there is no system.” Diversify and secure for success.
Threats from AI Abuse
With cyber dangers, AI has the potential for misuse and abuse. Moreover, studies show a 250% surge in AI-powered assaults. Knowing these risks is critical for safeguarding cloud native apps against rising attacks.
AI-powered risks have a large influence on DevSecOps techniques and security frameworks. AI-powered threats, in effect, bypass traditional defenses, exposing applications and sensitive data. To prevent vulnerabilities, update and patch AI systems.
Enterprises need practical actions to detect and mitigate AI-driven cyber threats. AccuKnox provides great solutions for this! Our platform will improve threat intelligence capabilities with superb anomaly detection technology.
DeepLocker malware uses AI to be evasive and target individuals or organizations. It’s one of the new classes of targeted and not so easy to identify attack tools. Such advanced assaults underscore the need to combat AI-driven threats.
Staying ahead of changing threats requires collaboration with cybersecurity specialists and knowledge exchange.
Conclusion
Emerging threats challenge cloud app security. Use proactive DevSecOps. AccuKnox CNAPP defends against threats.
DevSecOps plays a critical role in building resilient cybersecurity defenses. AccuKnox CNAPP provides comprehensive security measures. Easily mitigate AI abuse and cross-border vulnerabilities, thwart targeted attacks, and much more. We empower you to defend cloud native apps, ensuring data integrity, availability, and confidentiality. Stay updated, monitor, and adapt to evolving threats.
AccuKnox CNAPP protects against AI abuse, cross-border risks, and skill gaps. Trust our multi-function platform consisting of CWPP, CSPM, KSPM, IoT/Edge, and 5G with support for multi-environment for next-gen cloud native defense. We promise you’ll love us! Make the switch.
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
Total Exposed Attacks in 2024 Costed