Fulfill Cloud Security GRC Requirements with AccuKnox
In the complex landscape of cloud security, adhering to governance, risk, and compliance (GRC) requirements is paramount. AccuKnox CNAPP stands as a comprehensive solution that addresses GRC challenges head-on. This blog dissects the tools and features that our CNAPP platform includes that are needed to navigate compliance complexities.
Reading Time: 10 minutes
Table of Contents
What is Governance, Risk, and Compliance?
In today’s day and age, business operations are more complex, distributed, and dynamic. This modernization has brought immense growth potential. However, it has also introduced challenges regarding a methodical approach towards governance, risk, and compliance (GRC). It is a structured approach that integrates IT with corporate objectives. GRC consists of methods and tools to integrate innovation and adoption with an organization’s governance and risk management. Risks are controlled and compliance is achieved with legal and regulatory requirements.
Multi-tenant or large organizations usually require to function in an autonomous way within their distributed business environment but could still require centralized governance, reporting and benchmarking. Hence there is a need for a framework that can help organizations achieve GRC goals in a flexible and automated way. “Governance” refers to the principles, guidelines, or frameworks businesses use to accomplish objectives. These could be resource management, ethics, and openness to the public. This process involves identifying and addressing a variety of risks, including monetary, legal, strategic, and security-related ones.
Following rules, laws, and regulations is considered compliance. For example, HIPAA protects patient privacy. GRC tooling (like AccuKnox) assists firms by:
- Establishing rules from a common perspective
- Adhering to regulatory standards
- Making better decisions in a risk-aware environment.
Up-and-coming enterprises speed up data-driven decision-making, encourage ethical operations, and enhance cybersecurity by putting a GRC plan into place. It helps to build client trust. Adherence to data privacy laws like GDPR is also simplified.
What drives GRC implementation?
There are a lot of obstacles to success for any organization, regardless of the primary sector. Some of these are:
- Cyber risks
- Regulatory compliance
- Data privacy
- Uncertainties
- Rising risk management costs
- Complex third-party integrations.
These challenges demand a strategy to navigate towards goals. Conventional third-party risk management and regulatory compliance methods are insufficient. This led to the introduction of Global Risk Control as a unified approach. With it, stakeholders make accurate decisions. GRC helps businesses navigate these challenges and maintain their reputation and customer interest.
What are some of the common use-cases of GRC?
- The complex large enterprises may require to track and manage GRC among isolated yet connected business entities.
- Private equity portfolios that own several companies need to see conformance of GRC against their portfolio’s companies.
- Franchise companies may require GRC framework visibility into their franchises.
- Insurance firms that require to manage broker’s compliance consistently to meet regulatory obligations.
Suggested Guidelines
It is necessary to have an automation system serving as a single point of reference for security compliance. It must deliver regular audits for an ever-expanding set of relevant and sophisticated security requirements for software-defined data centers (SDDCs). To perform security hardening checks, the solution must scan particular configurations, produce gap analysis reports, and outline remedial procedures for any concerns it finds.
Improved availability, manageability, performance, recoverability, and security (AMPRS) are general criteria. Automated scans, which cut human labor and guarantee that your IT settings are operating at their best, give you access to information about security flaws like Log4Shell, Spectre, Meltdown, L1TF, and MDS. Compliance can be demonstrated over time using historical information on issue detection and remedies (which is perfect to match with configuration management or IT helpdesk reports to trace what impacted the environment).
Based on Runecast’s recommendations for Security Standards Compliance, an ideal GRC software has:
- ☑ The ability to rapidly monitor the objects and identify those having problems.
- ☑ A visual breakdown of problems that demonstrates their effects on both infrastructure and design elements.
- ☑ A list of the most frequent problems found in logs, together with a detailed summary status for each component of your infrastructure.
- ☑ Consistent, granular, and comprehensive reporting for all concerns in your settings.
Requirements for Essential Eight Compliance
Cloud infrastructures are not covered by Essential Eight compliance, which is designed to safeguard Microsoft Windows-based networks connected to the internet. Employing a risk-based methodology, organizations should choose an Essential Eight maturity level that best fits the needs of their security framework. According to the ACSC, attackers who put enough time, money, and effort into compromising targets won’t be stopped by maturity level three. Therefore, companies should take into account the remaining mitigation techniques from the Information Security Manual and the Strategies to Mitigate Cyber Security Incidents.
- Application control.
- Patch applications.
- Configuring Microsoft Office macro settings.
- User application hardening.
- Restricting administrative privileges.
- Patching operating systems.
- Multi-factor authentication.
- Regular backups.
Challenges of GRC Implementation
Security auditing and compliance are ongoing tasks. Many industry standards make too many attempts at universality and so look generic. It is difficult to adapt the many controls and requirements of security standards to the settings of your environment. Due to the dynamic, broad, and cross-industry nature, system administrators must stay current on all of them as changes occur. As you can expect, this is a demanding process. The major pain points include:
- Damage to the organization’s reputation and resultant financial loss
- Time needed for manual inspections and corrections
- External consultants needed to deal with the fallout from a breach
- Inadequate visibility of the environment’s compliance status
- Visibility into configurations drifts over time
- Bottlenecks and resource restrictions
- Reactive rather than proactive cleanup costs
- Penalties for failing to meet industry security requirements
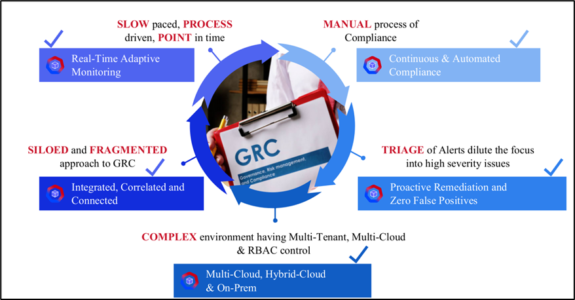
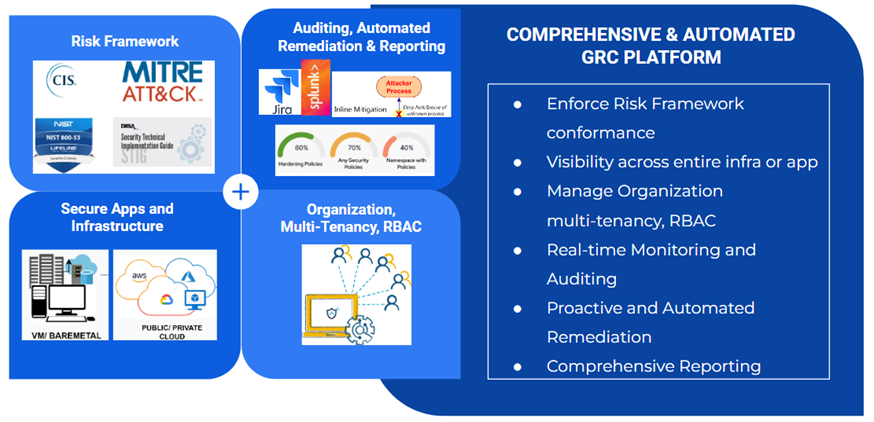
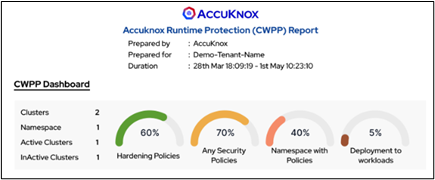
AccuKnox – Automated GRC Platform Overview
Governance
- Multi-tenancy, RBAC controls, Duties Separation, and so on
- Dashboards for CSPM, CWPP, and CNAPP
- App Behavior View, Multi-Cloud View
- Logging, monitoring, alerting, and auditing on a continuous basis
Risk
- Infrared Security Posture or Auto-Detect App
- Generated baseline and policy controls
- Whitelisting and Least Permissive
- Prioritization of issues depending on risk
- Automation of workflow monitoring, warning or blocking of infractions, auditing
Compliance
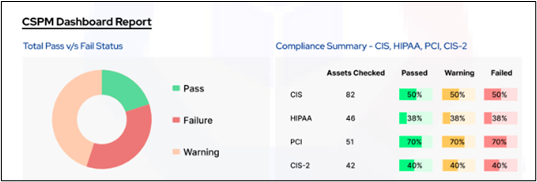
- Comply with CIS1, CIS2, HIPAA, PCI-DSS, MITRE, and NIST for your cloud infrastructure and apps.
- Compliance Report on Demand
- Scan types include continuous, periodic, and on-demand.
- Policy Controls Violations: Audit/Block Based Remediation
- RCA, Forensics, and Audit Trail
GOVERNANCE
Corporate governance allows businesses to manage their strategy, ethical behavior, and risk. Cloud governance is a set of policies and rules designed to ensure data security, system integration, and the deployment of cloud computing. 41% of companies develop multi-cloud operations only due to governance. A good framework:
- Improves resource management
- Hardens cloud security
- Curbs shadow IT
- Reduces administrative overhead and labor.
AccuKnox closely adheres to the Five Disciples of Cloud Governance and provides resource management and security issue detection. Setting up a cloud governance framework involves defining, implementing, and continuously monitoring controls. Let us see how.
Comprehensive Coverage
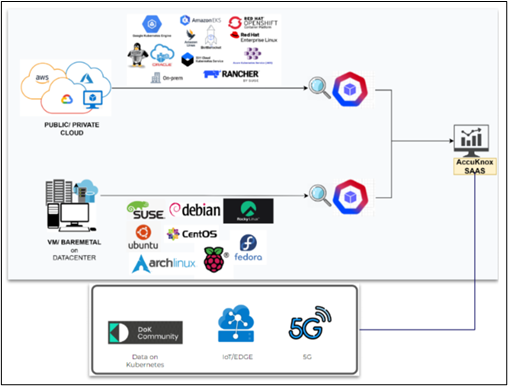
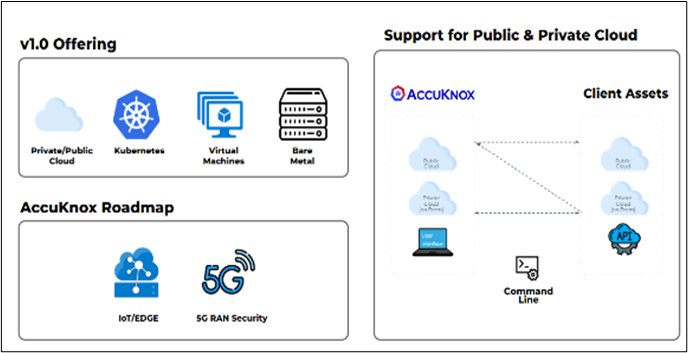
Our emphasis spans a broad range of issues. These include the protection of modern infrastructure across several sectors. We don’t just protect public clouds, but also private and hybrid cloud settings. We also extend to current workloads, to strengthen Kubernetes and containers. Based on the pulse of conventional workloads too and thus provide security for VMs and bare metal configurations in data centers or on-premises locations. Anticipating the future, our roadmap includes cutting-edge areas such as Edge/IoT and the approaching 5G era.
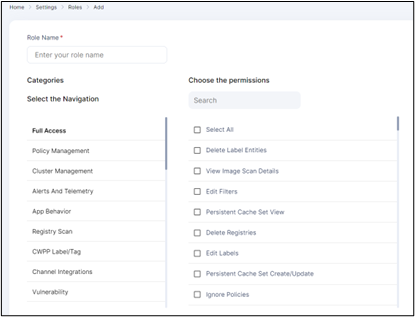
Multi-Tenancy, RBAC, Organizational Isolation
- Isolated and protected from others at the organizational level
- Segment various domains based on the organization’s tenants
- Temporal Invite people and withdraw access when no longer required
- Define RBAC in Tenants for multiple teams working on the same project, such as the Monitoring Team, Research and Development Team, Management Team, and so forth
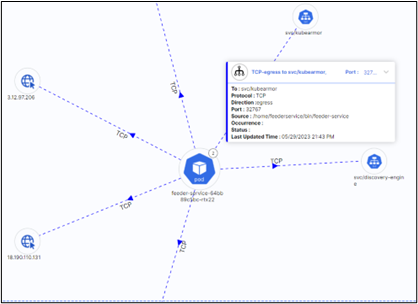
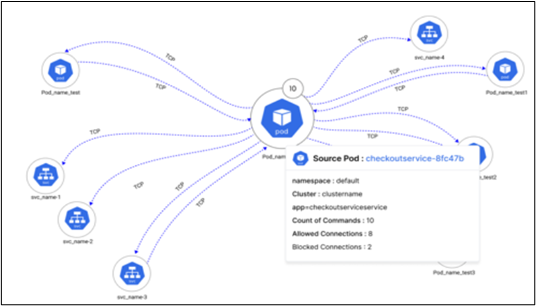
App & Infra Visibility
- Easily identify any vulnerabilities or misconfigurations that may exist within your infrastructure.
- The real-time monitoring feature enables tracking app behavior and detecting anomalies or performance issues.
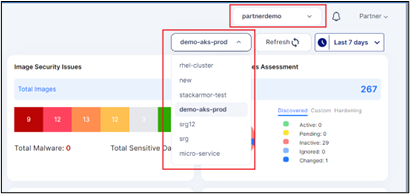
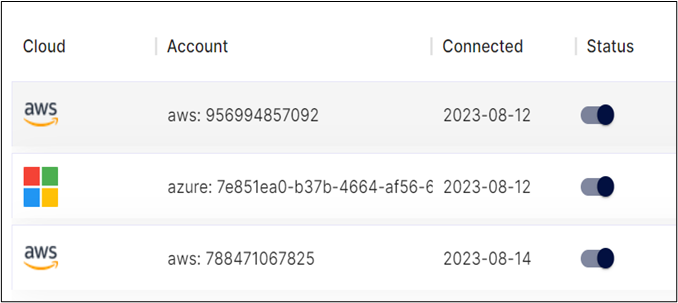
- A multi-cloud view simplifies the management and monitoring of assets across different providers.
- We provide you with a full view of your assets after every periodic scan. Get full visibility into your cloud workloads (pods, clusters, networks, etc.).
In the previous three years, a critical risk event occurred in 62% of the organizations
In cloud computing, risk management comprises discovering, analyzing, and prioritizing possible hazards. This procedure entails taking steps to reduce and prevent certain dangers.
- Create a security strategy.
- Keep an eye out for violations.
- Set up access controls.
- Review policies frequently.
- Create catastrophe recovery plans.
- Conform to industry standards.
Data loss, unwanted access, and breaches are all new risks with cloud computing. Risk management comprehends, analyzes, and mitigates these dangers.
As per the Deloitte report, Financial institutions prioritize:
- Collaboration (66%) between business units and the risk management function
- rising regulatory demands and expectations (61%)
- Creating and embedding a risk culture throughout the organization (55%)
Security risks span unauthorized access, breaches, and inadequate recovery systems. Compliance risks deal with adhering to standards, while data loss can result from insufficient backup.
Here are some examples of well-known risk types:
- Security
- Compliance
- Data erasure
- Service disruption
- Lock-in of vendors
- Privacy
- Risks associated with operations.
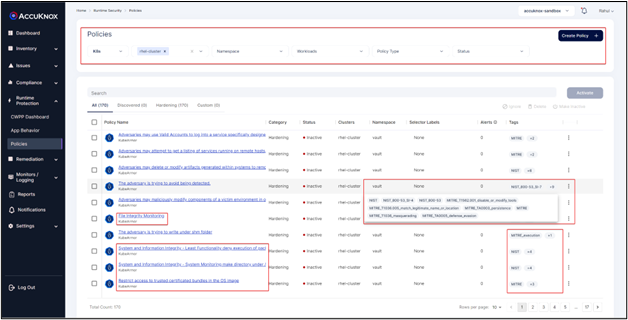
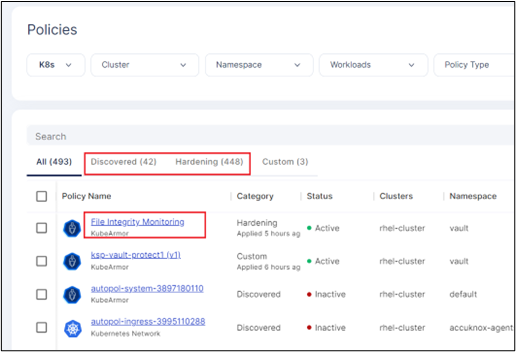
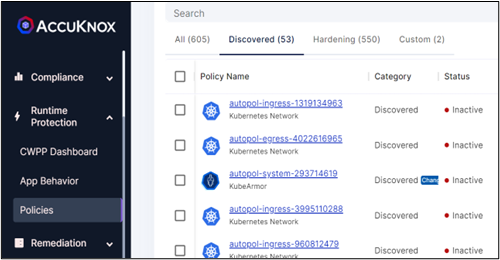
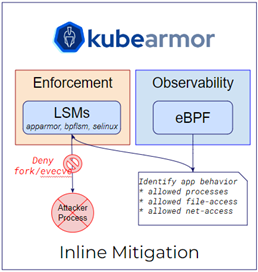
AccuKnox Policy Compliance
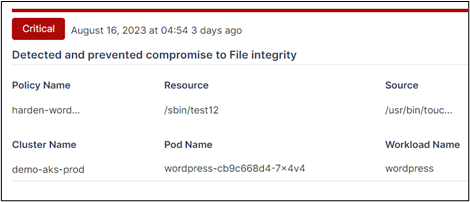
It is a robust solution tailored to enhance your security protocols. It features an auto-discovery function that evaluates compliance status, ensuring alignment with necessary standards. Through continuous security assessment, it detects and tackles vulnerabilities, bolstering your defenses in real time. Our solution also has options for audits and automated remediation. Addressing violations including file integrity monitoring and overall system integrity is easy. The toolkit has log analysis, events, and alerts, with deep telemetry and forensics.
Risk Based Prioritization
Prioritize Vulnerabilities Risk based on factors such as:
- Is the network exposed?
- Can it be exploited?
Is it used at Runtime?
Ingest vulnerabilities from multiple data sources and prioritize among them to handle critical vulnerabilities.
Whitelisting, Blocking Violations & Auditing
- Whitelist Specific Controls
- Block Violations from the Controls
- Get Alerted for the Block-based Controls
- Audit every event and generate Logs
COMPLIANCE
Compliance officers cite “continuing regulatory change” as their greatest obstacle.
Businesses must follow rules, regulations, and contracts to ensure their operations. ISO 27001 and NIST SP 800-53 standards are frequently used as the foundation for establishing security measures. If a firm decides to use ISO 27001, staff must be trained to ensure suitable controls are in place. Internal or external audits determine compliance levels. Internal audits provide self-evaluations, whereas third-party audits provide more objective conclusions. To follow EU GDPR standards, commercial enterprises are advised to follow certain security measures, which may be difficult given the cloud’s processing and storage capabilities. Noncompliance results in significant financial consequences, e.g., a company handling or storing credit card data might have a contract with a credit card company. This requires them to implement certain PCI-DSS components.
A functional enterprise-wide reporting system that integrates with compliance monitoring is only reported by 47% of chief compliance officers as existing in their organization.
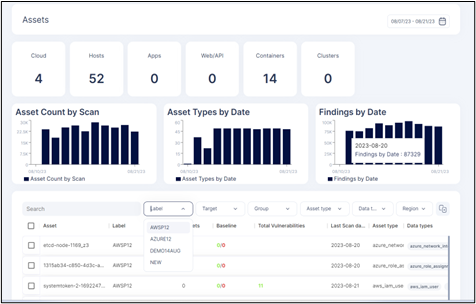
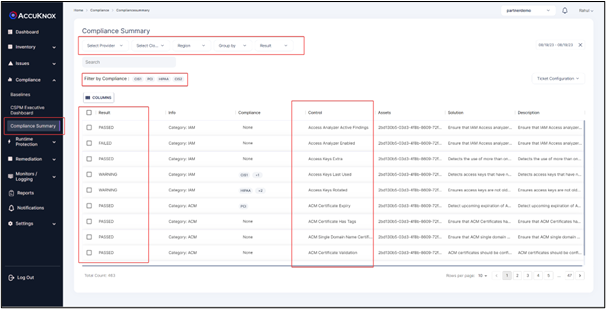
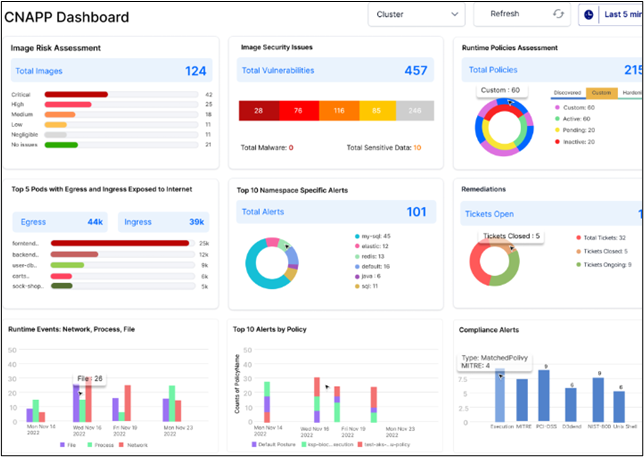
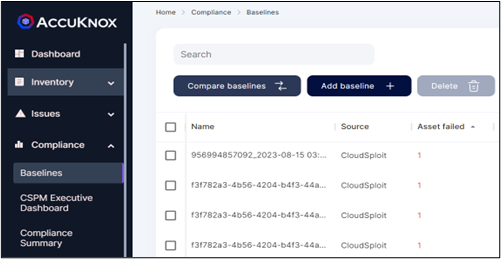
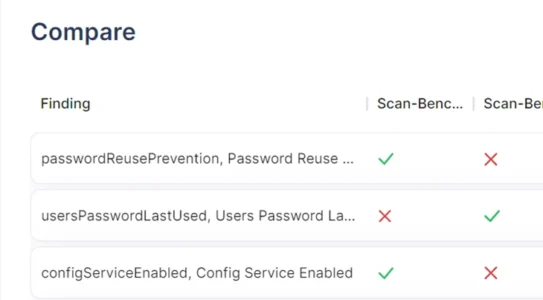
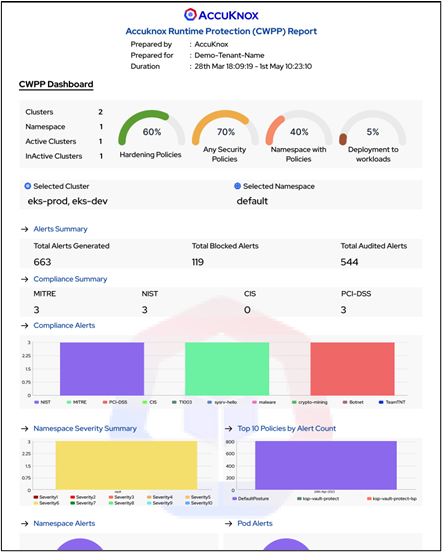
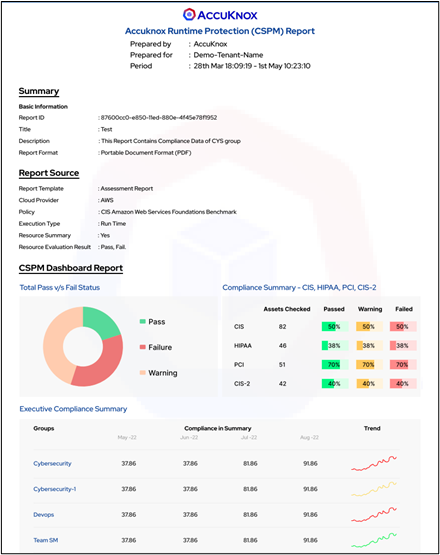
Compliance Summary – Cloud Resources and Workload
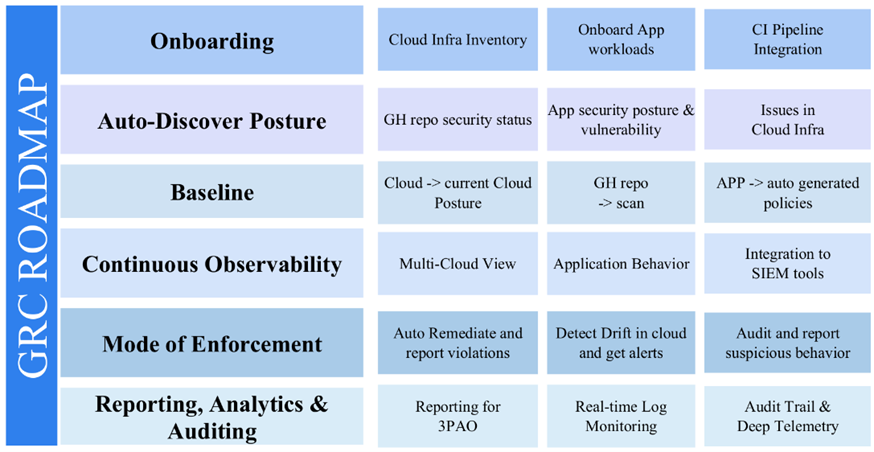
How to achieve GRC via AccuKnox
1. Onboarding
Integrate AccuKnox smoothly to further your GRC journey. Onboard your cloud infrastructure, workloads, and continuous integration pipeline seamlessly. Experience quick and effective workflows that seamlessly integrate GRC with your DevSecOps workflow.
2. Auto-Discover Posture
Our platform discovers and presents all the listed items and more in an intuitive dashboard for a better overview. AccuKnox’s automated discovery capabilities unveil comprehensive cloud security insights. Crucial components merge into an intuitive dashboard, offering a holistic view. Go deeper into cloud infrastructure, app security posture, and GitHub repository security status for an enhanced understanding. Our systems are designed with the Zero TrustArchitecture in mind.
3. Baseline
Lay a robust GRC foundation with AccuKnox’s advanced baselining. Align with existing cloud postures for consistent security. Auto-generated policies establish sturdy application baselines. GitHub repository scans complete the three-pronged security approach.
4. Continuous Observability
Oversee your entire cloud landscape with multi-cloud asset visibility. Get all the granular details about the app’s behavior through intuitive network graphs. Elevate GRC with real-time insights via SIEM tool integration for comprehensive threat analysis.
5. Mode of Enforcement
Safeguard cloud infrastructure through AccuKnox’s vigilant enforcement. Detect and rectify drifts in cloud configurations, maintaining security posture with timely alerts. Swift automatic remediation bolsters defenses. Audit functionality ensures prompt addressing of suspicious behavior.
6. Reporting, Analytics & Auditing
Strong reporting, analytics, and auditing will help you achieve and exceed security expectations. Demonstrate compliance activities to third-party assessment organizations (3PAO). With real-time log monitoring, stay informed. For thorough forensic investigation, our dashboards include audit trails and deep telemetry.
Compliance Reporting for 3PAO
Include AccuKnox in your DevSecOps toolkit to transform GRC. Streamlined onboarding, posture discovery, solid baselines, ongoing observability, proactive enforcement, and thorough reporting may all be used to improve cloud security posture.
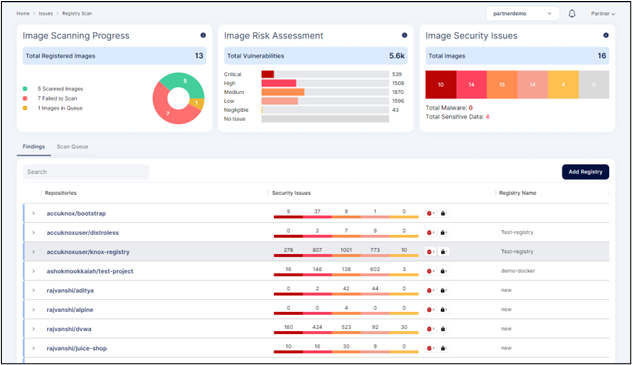
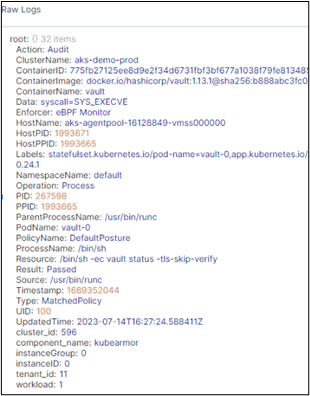
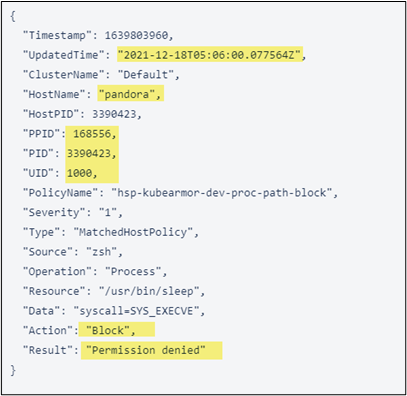
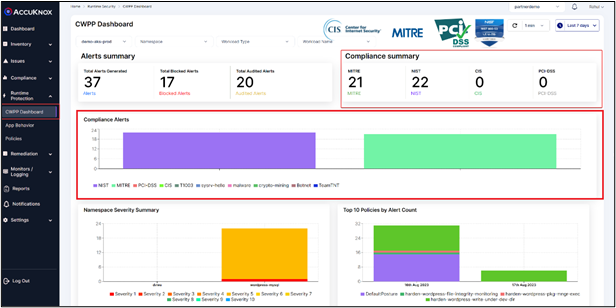
AccuKnox Forensics Solution
The systematic gathering, analysis, and preservation of digital evidence from cloud settings is the focus of cloud forensics. It assists companies in determining the origin, scale, and effect of security events, ensuring a thorough awareness of prospective risks. You get improved visibility and faster threat detection and incident response. This has 3 notable benefits:
- Delivering real-time notifications
- Speeding incident reaction times
- Narrowing the window of vulnerability to attacks.
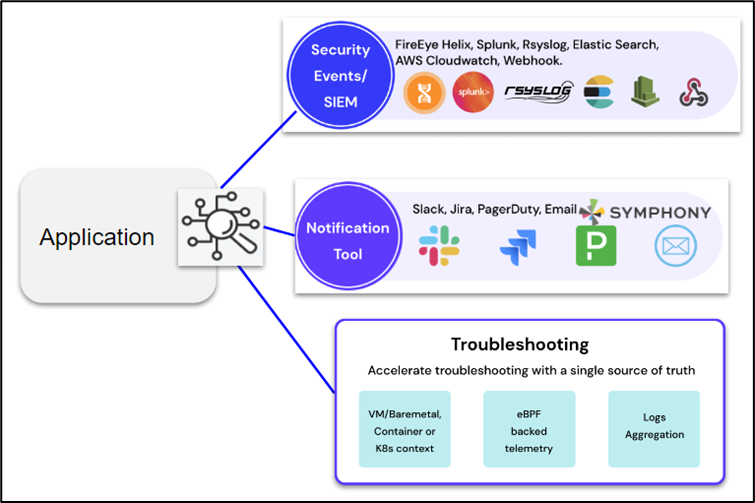
Check out our SPLUNK integration and RSYSLOG integration help docs for a better understanding.
Log Aggregation – Helix, Insights Integration with Splunk, Rsyslog, Elastisearch, AWS Cloudwatch, Sentinel
Notification Tools – Symphony, Slack, Jira, PageDuty, Email
Conclusion
GRC is a crucial component of contemporary digital operations, merging IT strategy with organizational objectives to control risk, comply with regulations, and assure moral behavior. However, it must contend with challenges, including regulatory requirements and cyber dangers. By offering real-time notifications, quick issue response times, and tool integration, AccuKnox provides a solution to these problems.
Recent statistics show that 70% of organizations cite compliance as their top cloud challenge, while 43% experience security breaches in the cloud. The average cost of a data breach exceeds $3.86 million, making GRC solutions indispensable. A global financial institution cut compliance violations by 93% with GRC implementation. This highlights the transformative potential of GRC. Our CNAPP solution accelerates threat mitigation strategies.
AccuKnox’s hybrid agent and agentless approach reinforces the best practices of both cloud governance and zero trust paradigm. Proactive automation is not an option but a necessity. AccuKnox’s support for GRC is a formidable defense against breaches. The promise of security, compliance, and ethical operations is fulfilled by GRC.
- Schedule 1:1 Demo
- Product Tour
On an average Zero Day Attacks cost $3.9M

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
Total Exposed Attacks in 2024 Costed