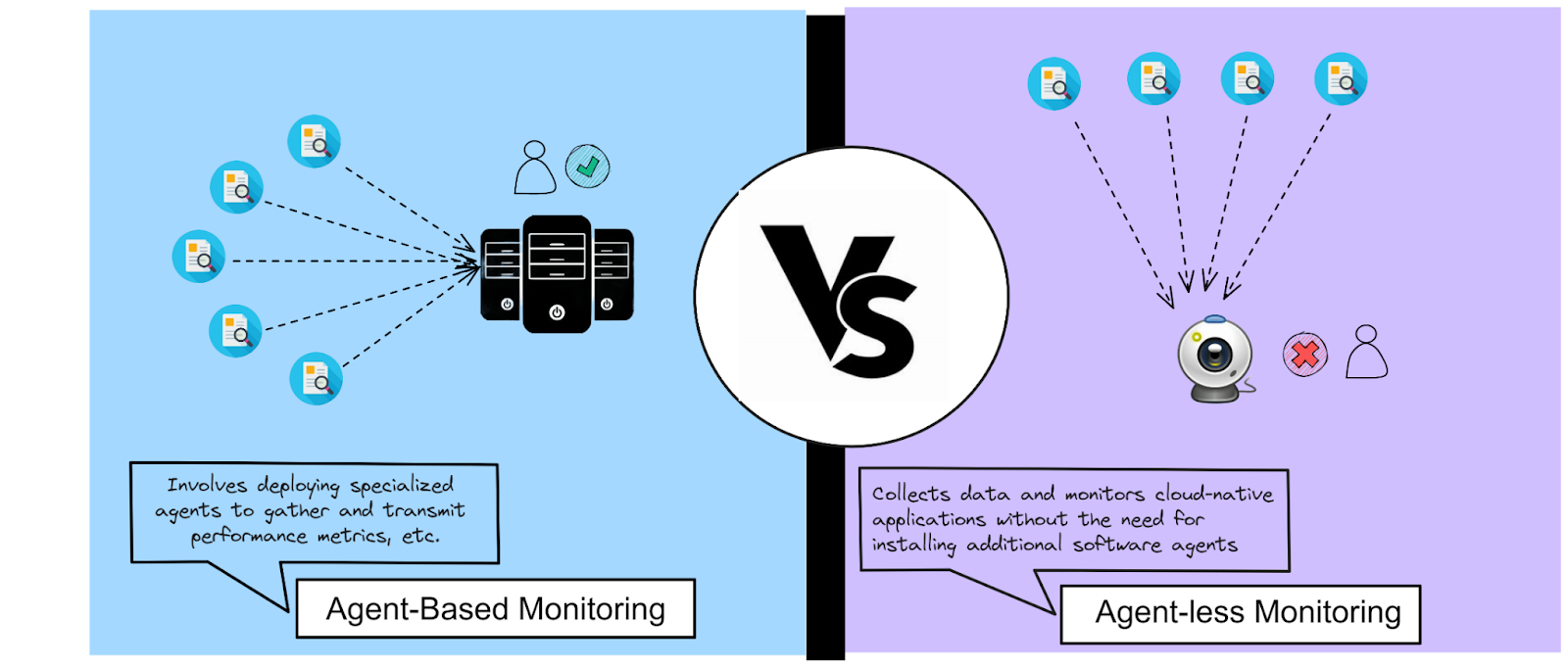
Agentless or Agent-Based Approach: Discover AccuKnox’s Adaptive Security Approach
AccuKnox Adaptive Security Approach addresses static and runtime vulnerabilities, focusing on agent vs. agentless debates for effective application protection. We go through the hybrid approach and the benefits of both methods and make informed decisions to fortify your cloud-native applications.
Reading Time: 5 minutes
Table of Contents
Cloud computing has revolutionized business operations by offering flexibility, scalability, and innovation. But ensuring strong security in cloud settings is a challenge. Choosing between agent-based and agentless security strategies requires much consideration. After all, it achieves the right balance and protects your data and applications.
💡TL;DR
- The CNAPP from AccuKnox is a strong security solution that integrates elements like ASPM, CSPM, and CWPP.
- Suppose you are at an airport. A rapid overview of the luggage is provided using an X-ray scanner (agentless). Yet a thorough body check provides a close look (agent-based).
- The agent-based approach used by AccuKnox examines system operations, network traffic, and runtime behavior. We can identify and counter sophisticated threats like zero-day assaults because of this. Advanced malware has no way to escape either.
- These models lead to improved security without sacrificing speed. You are free to operate various cloud environments without upkeep and as per your wishes.
Cloud computing has revolutionized business operations by offering flexibility, scalability, and innovation. But ensuring strong security in cloud settings is a challenge. Choosing between agent-based and agentless security strategies requires much consideration. After all, it achieves the right balance and protects your data and applications.
Static vulnerabilities
Occur during software development. They result from security awareness gaps, misconfigurations, or flawed access controls. To address them, perform strong security assessments and manage configurations. Dig out flaws in the codebase, root out environment variables, identify non-public keys, etc.
Runtime vulnerabilities
Arise from unpatched vulnerabilities during the development or execution of cloud applications. They stem from coding errors, insecure design patterns, or software vulnerabilities. They can compromise application and data security. Prevent them by using secure coding techniques and conducting regular vulnerability scans. Implementing effective runtime monitoring and protection systems is also a great security practice.
| Static Vulnerabilities | Runtime Vulnerabilities |
|---|---|
| Inadequate Access Controls | Injection Attacks |
| Misconfigured Security Groups | Cross-Site Scripting (XSS) |
| Weak Password Policies | Server-Side Request Forgery (SSRF) |
| Unpatched Software | Denial of Service (DoS) |
| Insufficient Data Encryption | Data Breaches |
| Insecure Default Settings | Malware Infections |
| Lack of Logging and Monitoring | Session Hijacking |
Exploring AccuKnox’s CNAPP Comprehensive Features and Functions
AccuKnox CNAPP (Cloud Native Application Protection Platform) is a powerful security solution. We designed it to safeguard cloud environments by addressing various security challenges.
This innovative solution provides comprehensive cloud security by incorporating the following components:
- ASPM (Application Security Posture Management)
- CSPM (Cloud Security Posture Management)
- CWPP (Cloud Workload Protection Platform)
By combining these components, our CNAPP solution empowers organizations. You maintain a robust security posture across cloud accounts and safeguard cloud workloads against both static and runtime vulnerabilities.
| CSPM (Agentless) | Scans cloud environment using exposed APIs. |
|---|---|
| Static Vulnerability Detection | Identifies misconfigurations, weak access controls, password policies, network exposure, compliance drift, etc. |
| Critical Asset Detection | Detects critical assets and provides detailed information, including issues, fixes for analysis. |
| Proactive Issue Identification | Tracks, alerts, and remediates known vulnerabilities, security malpractices, and compliance violations. |
| Enhanced Cloud Security | Addresses static vulnerabilities based on CVEs, compliance, and proactive monitoring of sensitive assets. |
| Flexible and Agentless Deployment | Offers flexibility and easy deployment without the need for agents. |
| CWPP (Requires Agent) | Protects cloud workloads against Zero-Day Attacks and safeguards against runtime exploits. |
|---|---|
| Runtime Anomaly Detection | Detects anomalies in application behavior, compliance drift, and attack analysis with detailed context. |
| Container Forensics Analysis | Helps analyze containers for deep packet-level inspection and understanding of security controls. |
| Mitigation of Runtime Vulnerabilities | Mitigates exploitable vulnerabilities by applying least permissive security posture. |
| Protection from Cloud Native Attacks | Essential for safeguarding against sophisticated cloud native attacks that can evade agentless detection. |
Choosing between agent-based and agentless security solutions in the cloud is important. Consider your specific needs, limitations, and long-term goals.
💡With AccuKnox’s agentless approach, you gain unmatched flexibility in addressing security issues. And what’s more? No need for third-party software installation. Our solution utilizes cloud APIs and scanning algorithms to cut threats. With us, you can ensure a seamless experience.
Schedule a demo today to take your cloud security to the next level.
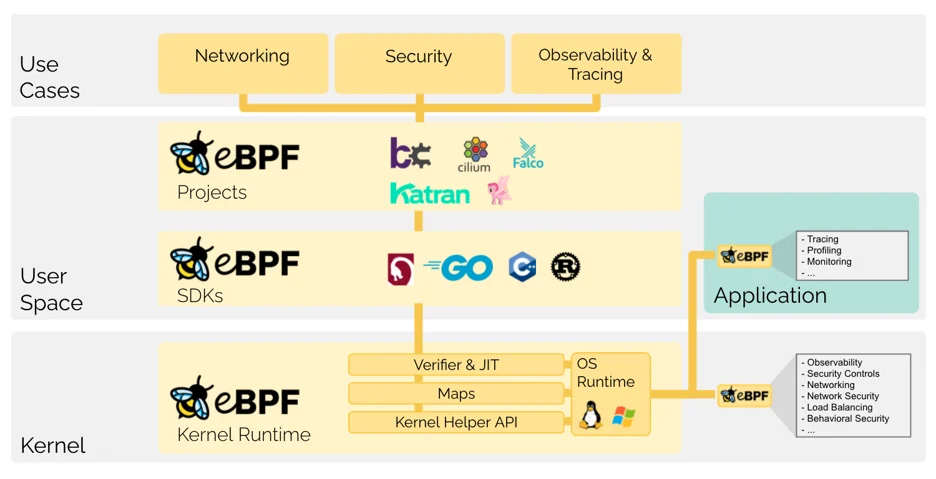
The Power of eBPF: A Tried, Tested, and Open Solution
eBPF (extended Berkeley Packet Filter) is effective and adopted for cloud security. Here’s why it’s the best choice:
Industry Standard and Openness
Facebook and Cloudflare use it, and it’s accessible to organizations of all sizes.
Industry Standard and Openness
Facebook and Cloudflare use it, and it’s accessible to organizations of all sizes.
Unparalleled Performance
eBPF delivers near-native speeds and exceptional performance, ensuring powerful security without sacrificing speed.
Enhanced Security Capabilities
Provides deep visibility into network traffic and runtime behaviors. Detects various security concerns like incursions, malware, and unauthorized access.
Integration with Cloud Native Technologies
Supports Kubernetes and other cloud-native technologies. Enables fine-grained network policies and prevents runtime attacks.
| Company | Use of eBPF | Problem(s) Addressed |
|---|---|---|
| Netflix | Network observability, security, and performance | Improved troubleshooting and optimization |
| Network traffic analysis and monitoring | Enhanced network visibility and analysis | |
| AWS | Container security and network filtering | Strengthened security and control |
| Kubernetes networking and observability | Enhanced Kubernetes ecosystem and monitoring | |
| Microsoft | Cloud-native networking and observability | Improved management and performance optimization |
Industry leaders like Netflix, Facebook, Amazon, Google, and Microsoft have benefited from eBPF. Meta’s Katran and Isovalent’s Cilium use eBPF for load balancing and cloud-native networking. It’s proven to be non-intrusive, secure, and reliable. eBPF is a cost-effective method for strengthening cloud security, making it the preferred choice for businesses.
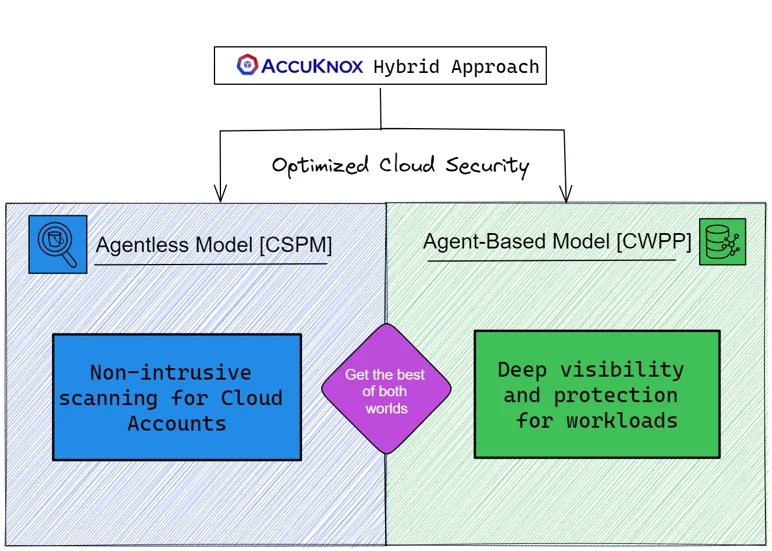
AccuKnox’s Hybrid Approach: Balancing Frictionless and Deep Visibility
Choosing between agent-based and agentless models for cloud security can be challenging. Customers hesitate to install vendor agents due to concerns about impacting performance and compatibility issues. AccuKnox understands these challenges and offers a unique hybrid approach. We combine the benefits of both models, providing enhanced security without compromising performance. You will not need to do any maintenance: it’s all taken care of.
Imagine airport security. An X-ray scanner provides a quick overview of baggage (agentless). But a full body inspection offers a detailed examination (agent-based). AccuKnox’s agent-based model analyzes runtime behaviors, network traffic, and system activities. Through this, we detect and mitigate advanced threats like zero-day attacks. Sophisticated malware has no room for escape as well.
AccuKnox is proud of its agentless model – especially for CSPM (Cloud Security Posture Management). Instead of traditional agents, we use cloud APIs through our SaaS platform. This allows us to scan cloud accounts and identify misconfigurations.
With cloud APIs, AccuKnox accesses the cloud infrastructure for full scans. No need for you to install agents on individual systems. This approach offers two key advantages:
Frictionless Deployment
Installing agents on each system is not required. This makes the deployment process simple and efficient. It also eliminates complexities and disruptions in managing and updating agents. Now you can manage diverse cloud environments without sweating.
Scalability and Flexibility
The agentless helps AccuKnox scale. Supporting a wide range of cloud accounts and configurations, it offers flexibility. It accommodates cloud service providers and environments without the limitations of agent compatibility.
A host-agent based approach is required for CWPP, whereas the agentless model is suitable for CSPM.
AccuKnox uses eBPF technology in CWPP. eBPF provides a framework for monitoring and securing workloads at the kernel level. AccuKnox deploys host agents with eBPF capabilities for granular visibility and threat detection.
⭐ We have the agentless model for CSPM and the agent-based model for CWPP. This offers a balanced approach providing non-intrusive scanning for cloud accounts – not to mention the deep visibility for workloads using eBPF-based agents. AccuKnox’s hybrid approach optimizes cloud security for diverse organizational needs.
Conclusion
To ensure complete security in the cloud, address static and runtime vulnerabilities. And of course, protect against advanced Zero-Day attacks. AccuKnox understands this need and provides a proven solution.
Our agentless approach handles 99% of security issues, like a no-touch X-ray scan at the airport. It identifies misconfigurations, weak access controls, and static vulnerabilities.
For the 1% of advanced threats, our agent-based model has deep visibility and analysis. This is comparable to the full-body scan example discussed earlier. Built on eBPF, our solution remains battle-tested. It is also open-source, ensuring high performance, robustness, and security.
Embrace AccuKnox’s hybrid approach for the best of both worlds. Safeguard your cloud infrastructure with our comprehensive and powerful cloud security solution. Book a Demo and put your mind at ease.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed