Highlights of CNCF Cloud Native Security TAG Survey
Introduction Here are the highlights of the CNCF Cloud Native Security Technical Advisory Group (TAG) Survey. The article directly quotes the whitepaper as a blockquote and adds commentary on how Accuknox can help address some of the challenges mentioned in the Microsurvey. #1: Modernizing Security is really important An overwhelming 85% of respondents indicated that […]
Reading Time: 4 minutes
Table of Contents
Introduction
Here are the highlights of the CNCF Cloud Native Security Technical Advisory Group (TAG) Survey. The article directly quotes the whitepaper as a blockquote and adds commentary on how Accuknox can help address some of the challenges mentioned in the Microsurvey.
#1: Modernizing Security is really important
An overwhelming 85% of respondents indicated that modernizing security is very important to their organization’s cloud native deployment. Another 12% believe it is somewhat important, and 3% feel neutral. No one indicated that it is not important.
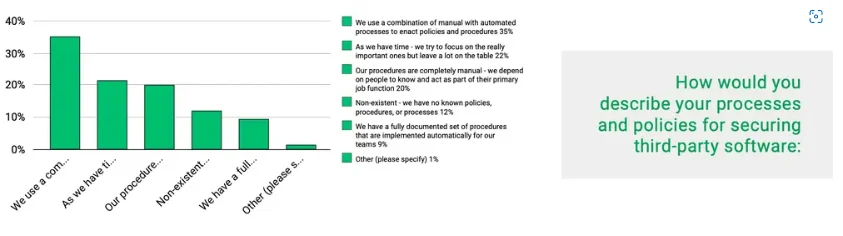
#2: Security policies are not fully automated and are driven by trial and error
Security Policy
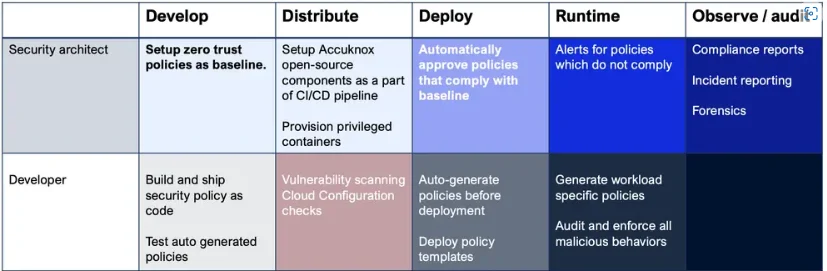
Accuknox automates the policy lifecycle:
Accuknox makes it easy for organizations to adopt fully open source-based security components and automate the entire – policy auto-generation, policy auto-approval cycle with the following user personas and user journeys:
Policy Lifecycle
82% of respondents said it’s important that the security systems they implement are built using open source software. No one indicated that they felt open source was too risky to trust, a sign that Linus’ Law is well understood
Accuknox’s open-source solutions
Accuknox is built on open-source first foundations and our contributions include:
- Cilium with SPIRE / SPIFFE integration – available on this fork but being upstreamed into Cilium https://github.com/kubearmor/cilium
- KubeArmor runtime cloud security https://github.com/kubearmor/KubeArmor
- Open-source Policy Templates for Cilium and KubeArmor: https://github.com/kubearmor/policy-templates
#4 Key Challenges include
- A lack of technical expertise (58%). This is not surprising as talent shortages have been reported in many other areas of software development. Also, cloud native security is a broad field, so the demand for security professional talent is high.
- Trouble matching new methods and processes like DevOps and CI/CD with existing requirements, tools, or processes (51%).weight: bold; padding-top: 20px;”>This is a well-known gap in the community – existing compliance frameworks have yet to catch up. While necessary, it is not particularly an exciting area, as we’ve seen with the general limits of automated compliance tooling (OSCAL being an exception).
- Data Security (49%). Seeing this high-up on the list is actually a good thing. Organizations are considering shifting to a data-centric security model and might be positioning them- selves to begin looking into Zero Trust. It may become a more prolific area of focus in the coming years, so be sure to keep an eye out.
- The complexity of building, deploying, and management (46%). This likely ties back to the lack of technical expertise. Like all technology revolutions, modern security requires a cultural shift, and many organizations are still figuring out how to do this. There is no “easy out” on cloud native journeys, and there certainly isn’t one for cloud native security. Each organization will need to learn and transform its approaches and processes while considering the existing documentation and papers available in this space, another where TAG Security contributes.
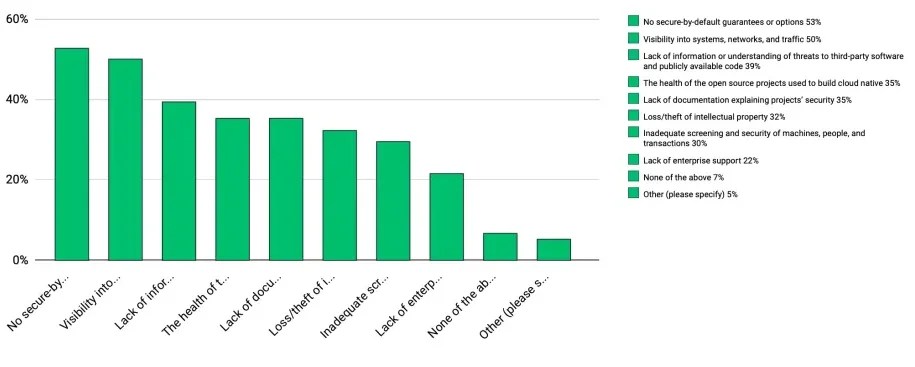
#5: The biggest concerns in Cloud-Native Security
Cloud-native chart
No secure-by-default guarantees or options (53%). This could be due to a lack of certifications or conformance with existing practices. Projects adhering to CII and adding a badge to their repositories could help to alleviate this concern around how projects were developed securely. However, it does not express a project as secure-by-default. There have been several nominations and ideas around the growing attestation of secure-defaults, but this is still nascent.
Visibility into systems, networks, and traffic (50%). While cloud native monitoring tools like Prometheus exist, they are primarily used for tracking performance. Tools like Falco will help, but it is still in the early stages of adoption.
Lack of information or understanding of threats to third-party software and publicly available code (39%). This is a problem with open source software in that no one is charged with providing this information. Foundations and groups need to work together to fill this need.
The health of the open source projects used to build cloud native (35%). This is another area where adding a CII badge or other security label could help to ensure conformance with secure development.
Lack of documentation explaining projects’ security (35%). This is often missed by projects that are not designed for security. The Security TAG encourages projects to complete a self-assessment and submit a pull request to their repo (for independent storage) to help identify gaps in documentation.
#6: Concerns about edge adoption include:
Misconfiguration (31%). This is due to a lack of documentation and testing for secure configurations.
Unpatched vulnerabilities (18%). Organizations should increase their release and update cadence to help address this.
Backdoors into the corporate network (15%). This underscored the importance of having identity and access management tools available and ensuring they are being utilized correctly.
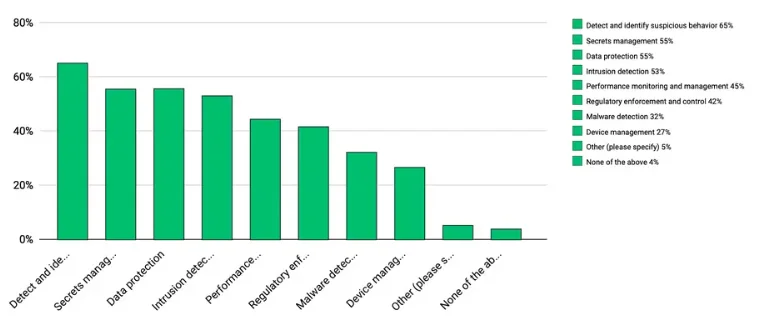
#7: Cloud-native projects addressing edge computing should have the following (security) capabilities
Detect and identify suspicious behavior (65%)
Secrets management (55%)
Data protection (55%)
Intrusion detection (53%)
Cloud computing Graph
#8: Vendor Lock-in Concerns
Organizations would like to have multiple open source alternatives for the following proprietary technologies
- Key Vault, Vault (59%)
- Splunk, ELK (53%)
- AWS Key Management Service (30%) 4. HSM replacement (23%)
Cloud Secuity Graph
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed