KubeArmor Host enforcement + Policy discovery
KubeArmor now adds support for host policies i.e policies that can directly run on Virtual Machines and Baremetal systems using AppArmor and SELinux. A host policy is a policy that is applicable to a given host (identified by a label) and can be enforced on the host by targeting an individual or a group of […]
Reading Time: 2 minutes
Table of Contents
KubeArmor now adds support for host policies i.e policies that can directly run on Virtual Machines and Baremetal systems using AppArmor and SELinux.
A host policy is a policy that is applicable to a given host (identified by a label) and can be enforced on the host by targeting an individual or a group of actions or processes.
A host policy can be enforced by either of the two Linux Security Modules (LSM):
- AppArmor – Many Linux distributions (e.g. Debian, Ubuntu, OpenSUSE) ship with AppArmor.
- SELinux – CentOS, RedHat Enterprise Linux and other RHEL flavors such as Rocky Linux support SELinux.
So how do host policies work?
Host policies require a virtual machine control plane called the KVMService (details here). The KVMService allows us to orchestrate and enforce Kubearmor (and Cilium policies) on non Kubernetes i.e. virtual machine and bare-metal workloads as well as hybrid workloads. Please read the help documentation regarding KVMService in our help section. Once the KVM service is installed and enabled a host policy can be defined to enforce on the host on a particular process or action on the host.
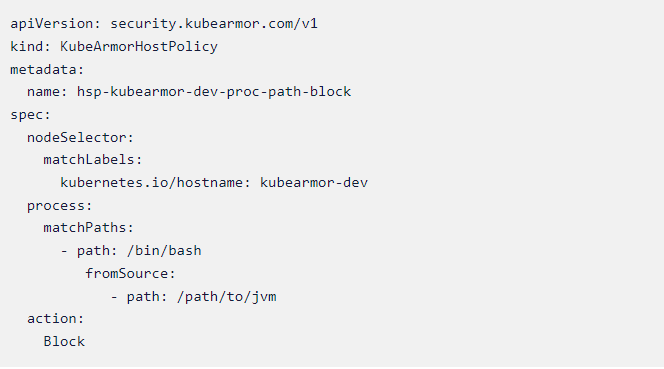
Sample host policy: Denies /bin/bash execution from any JVM /path/to/jvm
Host policy
Auto-discovery of host policies
Policy Discovery engine auto-discovers security policies for a VM or bare metal systems in addition to K8s clusters. The auto-discovery of policies on a host typically discovers policies by process (aka workload on the host). The user can choose to auto-discover policies as a single file for the host as well.
The auto-discovery of policies works for
- Host-based KubeArmor policy auto-discovery: KubeArmor will automatically discover the entire profile of the host operating system and its workloads including all processes, file accesses, and network connections. KubeArmor will then use these auto-discover policies to enforce it on the host (Ubuntu, Debian, CentOS, RHEL, Rocky Linux..) using AppArmor or SELinux depending upon the host operating system.
- Host-based Cilium policy auto-discovery: The Auto discovery also supports fully automated discovery of network policies (L3, L4, and L7 policies) for all workloads within a virtual machine or baremetal system attempting to access a network connection.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed