Is your system protected against Chaos Malware?
Introduction In this blog, we will see how to defend against Chaos malware using Accuknox’s Open-source tools. This blog is very specific to protecting against K8s workloads. Non K8s workload support is coming soon on Accuknox. Presented at Gosec 2017 in Montreal, Chaos malware origin could be traced to a rootkit called “sebd” active in […]
Reading Time: 3 minutes
Table of Contents
Introduction
In this blog, we will see how to defend against Chaos malware using Accuknox’s Open-source tools. This blog is very specific to protecting against K8s workloads. Non K8s workload support is coming soon on Accuknox. Presented at Gosec 2017 in Montreal, Chaos malware origin could be traced to a rootkit called “sebd” active in 2013. This malware can create a fully encrypted and integrated SSH reverse shell on the victim’s device.
Malware functionality
To stay hidden, the attacker first disables the logging history. Then the attacker checks the SSHD binary and the existence of certain files such as /usr/include/gpm2.h. This attacker can make sure it is not infected with any other malware. The files that the attacker checked are commonly known to be used by patched SSHDs to log stolen SSH credentials. That’s why this check has been performed in the first place.
This malware consists of:
- Chaos Server – ELF Binary
- Chaos Client – ELF Binary
- initrunlevels – Shell script
- Install – Shell script
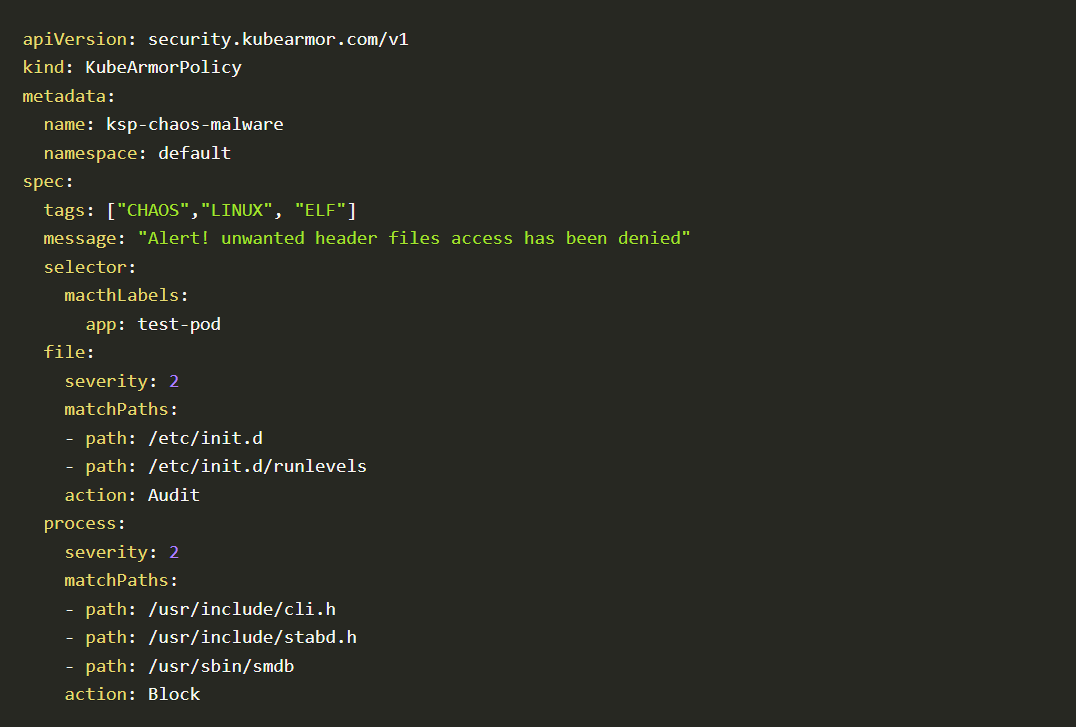
Let’s understand how this works. The install script is copying the initrunlevels script to /etc/init.d to ensure that the file is executed at each boot of the system. The initrunlevels script opens port 8338 and checks if certain files exist. If they do not exist, the script copies hidden files to the checked paths. Next, the script copies the Client into /usr/include/cli.h and Chaos into /usr/include/stabd.h and /usr/sbin/smdb.
This is done in order to create backups for both Client and Chaos on the system. The attacker also dropped and executed additional files to make the system part of an IRC botnet, but we investigated the backdoor only within the scope of this post.
Virustotal reference:
Chaos Server: Click here
Chaos Client: Click here
Accuknox Run-time security tools and how we can protect against threats like Chaos
Accuknox open-source tools protect against unknown and malicious behavior at run-time.
malware such as chaos at run-time. A run-time security tool provides active protection for your workloads while they’re running. The idea is to detect and prevent malicious activity from occurring after the workloads have been initialized and are running.
Accuknox open-source tools consist of a) auto policy discovery b) KubeArmor and c) Cilium.
There are many ways to block Chaos and other kinds of malware. One would be to auto-discover a safe profile of the workload and only allow that through auto-discovery.
Blocking Chaos specific actions
For the purpose of this blog, we will focus on understanding the Chaos malware signature and trying to block those specific actions. With the information we gathered about Chaos, we can create a KubeArmor policy as follows to block Chaos malware
Chaos malware
The given Kubearmor policy will defend against file-related actions in chaos malware. In this case, the policy is applied to the workload by using the kubectl command
kubectl -f apply <policyfile name.yaml> #to apply the policy
This malware also opens port 8338 to run initrunlevels script.
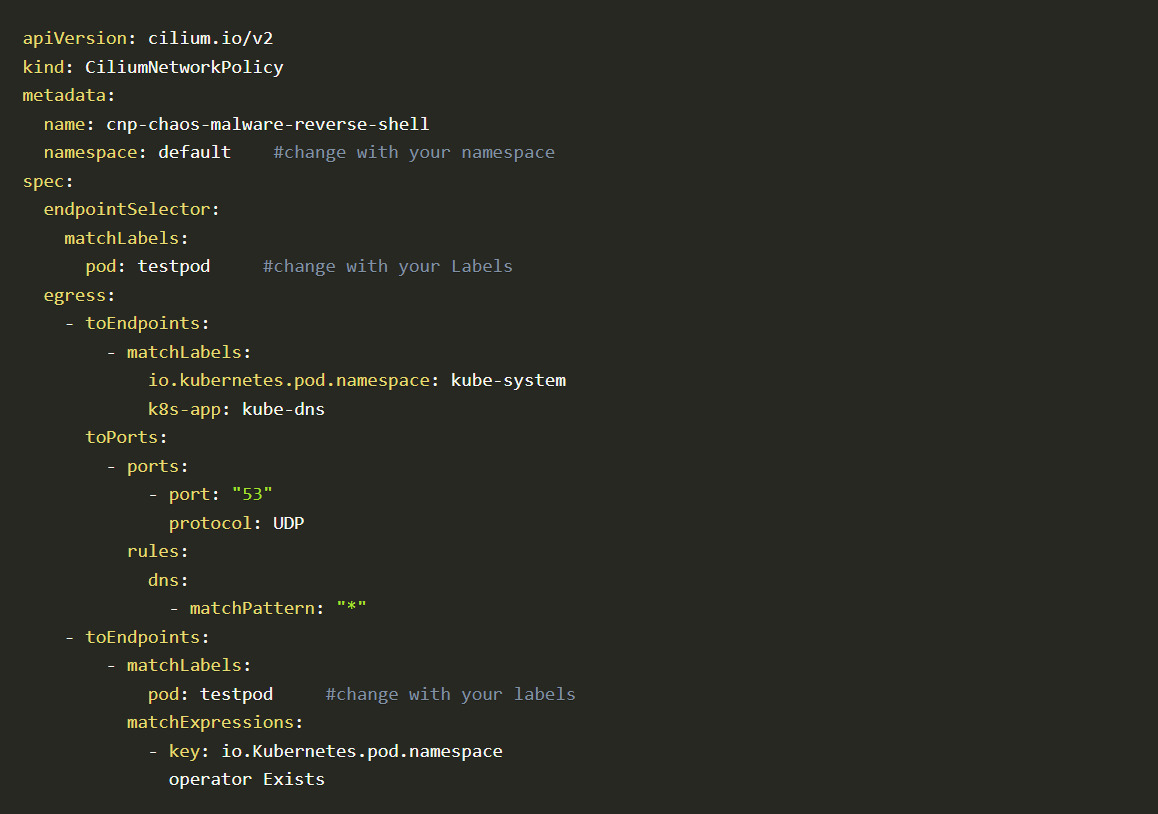
Let’s use a Cilium network policy to block that port from opening.
Cilium network policy
Here in this policy, we are only allowing “53” ports to open and all other ports are closed in the pod. So when initrunlevels runs, it will not be able to open any unwanted ports.
Conclusion
In this malware, we have seen how to defend against Chaos malware using KubeArmor & Cilium. This malware uses various techniques such as Reverse shells to attack infected machines. So KubeArmor can protect files, systems, networks, and Cilium is like a network firewall for containers. We used both programs to prevent this attack.
References:
https://www.gosecure.net/blog/2018/02/14/chaos-a-stolen-backdoor-rising/
https://securityaffairs.co/wordpress/69459/hacking/chaos-backdoor.html
Creating a persistent backdoor and bypassing anti-virus programs with the Chaos
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed