
KubeArmor v0.11 Release
Lift your cloud security shields up with Kubernetes security, simplified deployment, TLS assessment, EKS Addon, and more in KubeArmor v0.11
Reading Time: 6 minutes
Table of Contents
Elevating Container Security for Kubernetes Environments
We’re thrilled to introduce the latest release of KubeArmor, version v0.11! This significant update reinforces our commitment to providing top-tier container-level security for Kubernetes deployments. With an array of new features, integrations, and improvements, KubeArmor v0.11 empowers you to achieve even greater security and control over your containerized workloads. Let’s delve into the key highlights of this release:
💡TL;DR
- As a significant update to Kubernetes security, KubeArmor v0.11 makes deployment, TLS assessment, and the EKS addon easier.
- The OpenTelemetry KubeArmor adapter converts KubeArmor telemetry data to openTelemetry format, providing insights into container behavior and workload interactions. The KubeArmor Controller reconciles policies using k8s-native design.
- K8tls, a service endpoint scanning engine that checks whether Kubernetes service endpoints are utilizing secure communication and the proper security configuration, is introduced in this version.
- Additional Kind and Minikube compatibility make it simple to apply security policies to local testing and development environments.
- The updated Helm chart streamlines deployment and the KubeArmor Operator streamlines cluster component auto-detection.
Operator support: Simplifying Management and Deployment
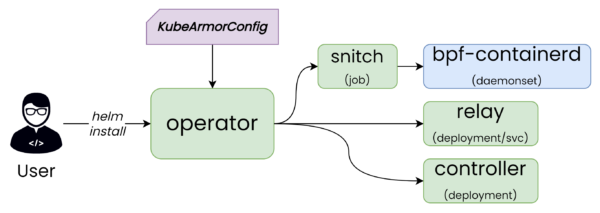
Elements of KubeArmor Operator design:
- Operator: The operator is the initial component that gets deployed as part of the helm-based installation. The job of the operator is to reconcile the current state of KubeArmor to its intended state.
- Snitch: Snitch is a job deployed by the operator to check what are the prevalent LSM (Linux Security Modules) and the container runtime on each of the nodes. Snitch then directs the KubeArmor daemonset to use these parameters to accordingly use the appropriate enforcer and container runtime primitives.
- bpf-containerd: This is essentially the KubeArmor daemonset that does most of the work from observability to policy enforcement. Note that the name of the daemonset is dependent on the underlying enforcer (bpf, apparmor) that is used and the container runtime that is detected.
- Relay: KubeArmor Relay connects to each of the daemonset and collects the alerts/telemetry/log and makes it available at a single GRPC endpoint. External services can connect to KubeArmor Relay to get the alerts/telemetry from a single point. Relay is available as a k8s deployment/service.
- Controller: KubeArmor controller reconciles the KubeArmor policies. One of the biggest advantages of KubeArmor is its use of k8s-native design for policy management. Users can enable disable policies at will by applying/deleting the policies at runtime. This enables a wide range of possibilities such as time-based policy activation.
OpenTelemetry
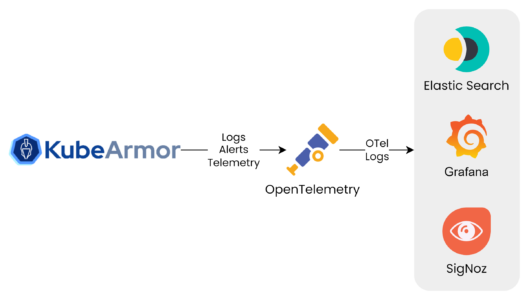
To enhance your observability capabilities, KubeArmor now seamlessly integrates with Open Telemetry. Gain unparalleled insights into container behavior and workload interactions through comprehensive telemetry data collection. With this integration, you’ll be equipped to make informed decisions, swiftly identify anomalies, and proactively address potential security threats.
Credits: Amazing work by Maureen Ononiwu for handling KubeArmor’s OpenTelemetry integration as part of LFX Mentorship. 🚀
Announcing k8tls (pronounced cattles): k8s service endpoints TLS best practices assessment
Security extends beyond containers. KubeArmor v0.11 introduces k8tls to bolster transport layer security within Kubernetes clusters. Safeguard your communications with enhanced encryption, safeguarding your data and ensuring the confidentiality of sensitive information.
K8tls is a k8s-native service endpoint scanning engine that verifies whether the endpoint is using secure communication and is using the right security configuration. K8tls deploys itself as a k8s job that scans/fingerprints k8s service endpoints to identify if TLS best practices are followed.
Primary features include:
- 🔒 Check if the server port is TLS enabled or not.
- 📃 Check the TLS version, Ciphersuite, Hash, and Signature for the connection. Are these TLS parameters per the TLS best practices guide?
- Certificate Verification
- 💥 Is the certificate expired or revoked?
- ✍️ Is it a self-signed certificate?
- ⛓️ Is there a self-signed certificate in the full certificate chain?
KubeArmor as Canonical Microk8s Addon
Kind and Minikube Compatibility
With this release, KubeArmor extends its compatibility to Kind and Minikube clusters, enabling you to effortlessly apply KubeArmor’s security policies to your local testing and development environments. Maintain consistency between testing and production while fortifying your workloads.
karmor profile
karmor logs tool provides raw telemetry out of the box. However, you may want to summarize the process, file, network, syscall events over a period of time. karmor profile introduces a way to handle the summarization. KubeArmor community followers might realize that the base profile feature was added in v0.8 release. v0.11 vastly improves the usability of the features, for e.g, by sorting the data based on process name, summarizing/aggregating well, adding syscall related event summarization etc.
EKS Addon published: Simplifing EKS deployment
Amazon EKS Anywhere allows installing and managing Kubernetes clusters on your own infrastructure, with optional support from AWS. EKS Anywhere supports full lifecycle management of multiple Kubernetes clusters that can operate completely independently of any AWS services. It provides open-source software that’s up to date and patched so you can have an on-premises Kubernetes environment that’s more reliable than a self-managed Kubernetes offering. EKS Anywhere is compatible with Bare Metal, CloudStack, and VMware vSphere as deployment targets.
Although EKS Anywhere can make cluster administration easier, the issue of protecting how Kubernetes namespaces, pods, workloads, and clusters interaction and access of shared resources remains an unsolved problem. It is imperative that workloads are protected at runtime since most of the attacks such as cryptomining, ransomware, data exfiltration, denial of service are manifest once the workloads are deployed in target k8s environment.
In line with the recommended safety guidelines for EKS, KubeArmor comprehensively fulfills these requirements. Getting up to speed on the Kubernetes threat environment proves to be difficult for security teams. New responsibilities for Kubernetes infrastructure and workloads lead to high overhead. Furthermore, ensuring that platform and application teams have consistency and complete visibility across environments for configurations and settings to fulfill AWS EKS security best practices can be difficult. KubeArmor helps you take care of most of these for you.
Streamlined Deployment: Updated Helm Chart
Deploying KubeArmor has never been smoother. The updated Helm chart simplifies the installation process, ensuring that you can effortlessly manage KubeArmor’s security policies across your Kubernetes clusters. Spend less time configuring and more time securing. Use of KubeArmor Operator greatly simplifies the auto detection of cluster components and deploying the kubearmor accordingly. For example, no more mounting of unwanted host mount points to just detect the container runtime in use.
Staying in Sync with Infrastructure: Terraform Updates
For those who embrace infrastructure-as-code, KubeArmor v0.11 offers updated Terraform integration. Seamlessly incorporate KubeArmor into your Terraform workflows, ensuring consistent security provisioning throughout your infrastructure.
Open source KubeArmor terraform provider from AccuKnox helps provision KubeArmor deployments, policies, and configuration at scale using Hashicorp Terraform.
Pushing Boundaries: Scale Testing with KubeArmor-Relay
Scalability is of paramount importance. One of primary hurdle to observability/monitoring solutions is its impact on runtime performance. With v0.11, we tested logging/telemetry components such as KubeArmor-Relay for scale of 100s of nodes. Through rigorous testing under varying workloads, KubeArmor v0.11 ensures unwavering performance even in the most dynamic Kubernetes environments.
Flourishing Ecosystem: Adopters Update
Our community of adopters continues to grow, and we’re immensely grateful for your support. Join a vibrant community of users and contributors who are shaping the future of container security. Together, we’re elevating Kubernetes security to new heights.
Thanks/Credits
We extend our gratitude to our dedicated community, whose feedback and contributions drive the evolution of KubeArmor. Dive into the cutting-edge security enhancements of KubeArmor v0.11 and fortify your Kubernetes environment with confidence.
To explore the latest features and embark on your journey with KubeArmor v0.11, visit our official GitHub repository and comprehensive documentation.
Secure your containers, fortify your Kubernetes clusters — experience KubeArmor v0.11 today.
Stay secure, The KubeArmor Team
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed





