Protecting Against Typical MITRE TTPs With KubeArmor
What is MITRE TTPs MITRE TTP is a well-known comprehensive knowledge base that analyzes all the Tactics, Techniques, and Procedures (TTPs) that advanced threat actors could possibly use in their attacks. Rather than a compliance standard, it is a framework that serves as a foundation for threat models and methodologies. In any case, by using the […]
Reading Time: 2 minutes
Table of Contents
What is MITRE TTPs
MITRE TTP is a well-known comprehensive knowledge base that analyzes all the Tactics, Techniques, and Procedures (TTPs) that advanced threat actors could possibly use in their attacks. Rather than a compliance standard, it is a framework that serves as a foundation for threat models and methodologies.
In any case, by using the MITRE ATT&CK framework model used to infiltrate and attack Kubernetes Clusters, An attacker
normally strategizes how to penetrate a cluster and perform damage by following the stages that require an attack lifecycle. The attacker must progress through each of these stages for the attack to be successful.
How to Use the MITRE ATT&CK matrix for Kubernetes?
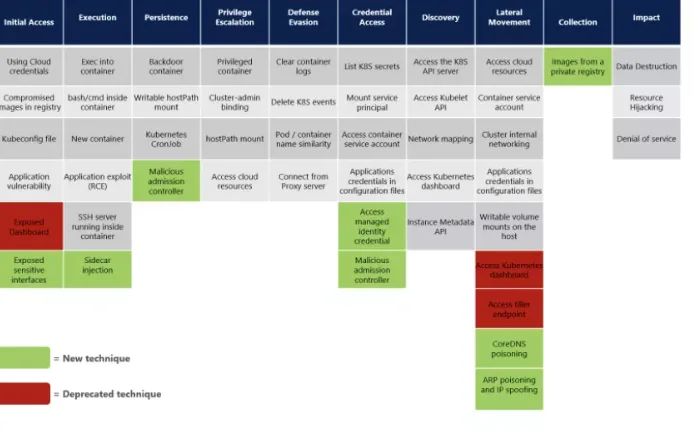
The MITRE Engenuity ATT&CK framework has 10 steps:
- Initial access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential access
- Discovery
- Lateral Movement
- Collection and Exfiltration
- Command and Control
From initial access to command and control, these are the 10 tactics, which individually consist of techniques and sub-techniques.
Protect and Detect Typical TTPs in the MITRE ATT&CK framework with KubeArmor
Organizations currently have a vast amount of unsecured workloads and no efficient or unified way to protect them. Often, they are managing multiple, single-purpose security solutions to secure these workload stacks, which can create operational burdens and security gaps,
” Today’s new capabilities further our commitment to deliver comprehensive
cloud workload protection across hybrid and multi-cloud environments. DevOps
teams can now efficiently build and deploy their workloads and applications
rapidly while helping security teams deliver protection.
KubeArmor, is open-source software that enables you to protect your cloud workload at run-time.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed