Maximizing Zero Trust Security: The 8 Pillars & AccuKnox Cutting-Edge Solutions
A deep-dive into the eight pillars of Zero Trust architecture and how AccuKnox leads the way in cloud security.
Reading Time: 12 minutes
Table of Contents
Securing the Cloud: 8 Pillars of Zero Trust and How AccuKnox Leads the Way
Zero Trust means “never trust, always verify.” It means not outrightly giving permissions to users, devices, and networks without cause. You need to confirm and authenticate entities before granting access to resources.
In the world of cloud architecture, it is a much-needed approach. Zero Trust (ZT) challenges the idea of trusting everything inside the network perimeter. Instead, it focuses on verifying and securing every user, device, and network connection. At AccuKnox, we follow the Zero Trust security principles laid out by NIST in their Zero Trust Architecture standard NIST.SP.800-207. Our solutions meet industry best practices for robust security. Now, let’s understand the motivations behind Zero Trust security.
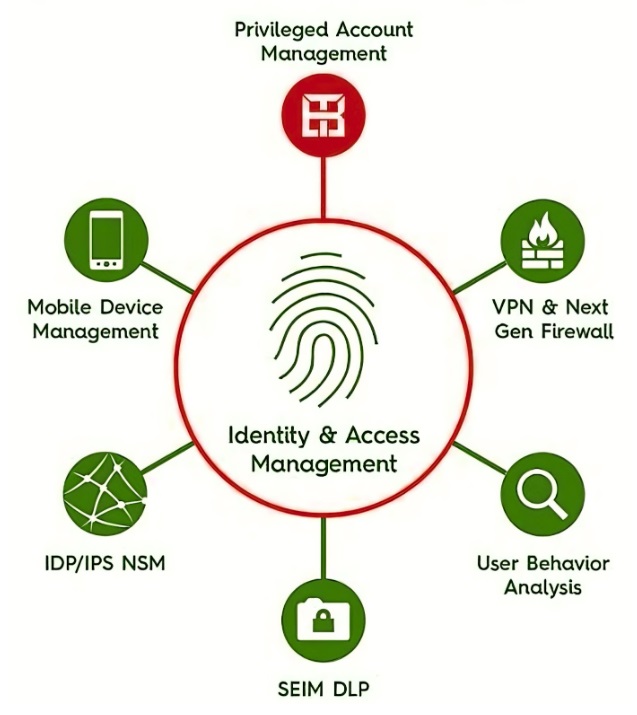
Tenets of Zero Trust Security
- Strict authentication and authorization. Must authenticate all resources. No implicit or irregular access without explicit whitelisting.
- Maintain data integrity. Put in place robust encryption and data protection measures. Enforce confidentiality, integrity, and availability of sensitive information.
- Gather data for improved security. Auto-Discover default posture and analyze data to enhance security standards.
- All data sources and computing devices are a resource. Treat all devices with access to the network as valuable resources.
- Keep all communication secured regardless of network location. Apply strict security requirements to all network connections.
- Grant resource access per session. Follow the principle of least privilege. Check each access request.
- Moderate access with a dynamic policy. Establish a transparent policy for access privileges.
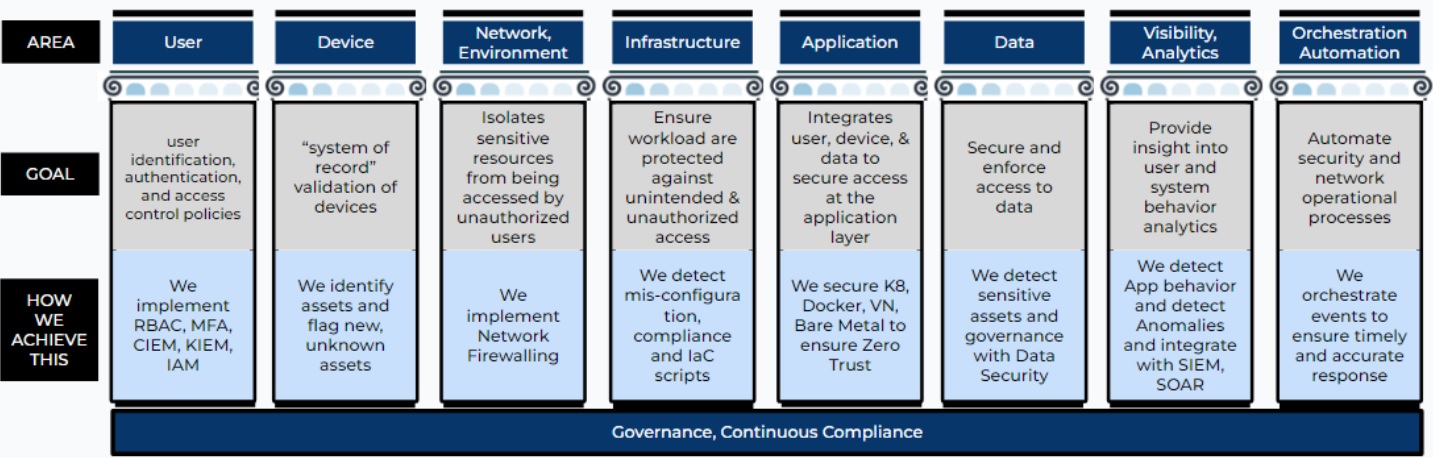
Following these tenets leads us toward the eight pillars of Zero Trust which in turn helps build a strong security framework. Its primary goal is to earn and maintain trust at all costs. As Bruce Schneier said, “Trust has to be both earned and maintained.” With Zero Trust security, you can protect your assets from evolving threats. Let’s explore each pillar to understand its significance in the ZT framework. Below we will see the contribution of each pillar to securing the cloud environment.
Discover why DevSecOp professionals are embracing Zero Trust architecture. Explore our Zero Trust CNAPP Buyer’s Guide today and gain invaluable insights.
Pillar 1: User Identification and Access Control
To ensure system security, user verification, authentication, and access control policies are crucial. Let’s explore each concept.
- User verification confirms your identity. Require a username and password. Also, using biometrics like fingerprints or facial recognition are more secure alternatives. MFA is a common trend involving a verification code via email or phone.
- Authentication proves you are who you claim to be. You present credentials like a password or cryptographic token. This proves your knowledge or possession of something unique to you.
- Access control policies define rules for user access. They determine what resources or actions you can access. It follows the principle of granting the least privilege necessary. This thwarts unauthorized access, breaches, or misuse.
Now, let’s discuss the role of dynamic data analysis in verifying attempts. This analysis examines factors surrounding your authentication attempt to determine its legitimacy. It considers
- Device and network information. Analyzing device location, IP address, and operating system helps identify suspicious activities.
- Behavior patterns. Monitoring your login times, preferred devices, and access patterns detect anomalies.
- Geolocation and IP reputation. Checking your login location against previous locations or IP reputation provides insights.
Real-world example:
Salesforce uses User Identification and ACL. Salesforce Identity allows fine-grained access controls and streamlined authentication. This has increased customer trust and revenue.
Remember, balance security and usability. Strict measures may frustrate users, while lax measures leave vulnerabilities. In summary, dynamic analysis verifies attempts by considering factors. Install robust mechanisms and effective policies to protect information and maintain system integrity.
Pillar 2: Device Validation and Trustworthiness
Device validation confirms the authenticity and integrity of user-controlled and autonomous devices. Only trusted and authorized devices can access the system. Why is this important? Well, it prevents unauthorized access, data breaches, and misuse of resources.
Pros of validating devices and networks:
- Mitigating security risks. By validating devices, you identify vulnerabilities or compromised devices. This reduces the chances of unauthorized access or attacks. Can you imagine the consequences of unauthorized access to your system?
- Protecting sensitive data. User-controlled and autonomous devices often handle sensitive data. Validating these devices safeguards confidentiality, integrity, and availability. This means only authorized and secure devices can access and process sensitive data. How important is the protection of your sensitive data?
- Maintaining acceptable cybersecurity posture. Device validation contributes to a secure and trusted environment. All connected devices must meet the necessary security requirements. How would you feel if your system had an unacceptable cybersecurity posture?
Consider these measures for device trustworthiness and to maintain a good cybersecurity posture:
- Put in place device authentication to verify device identity.
- Use secure communication protocols to protect data transmission.
- Update device firmware to address known vulnerabilities.
- Conduct periodic device assessments to identify risks or vulnerabilities.
Real-world example: Apple uses device validation to check if devices are genuine and secure. Only trusted devices can access Apple services and products. This keeps user data safe and builds customer trust in Apple’s security.
Device validation mitigates security risks and protects sensitive data. It is a proven way to maintain an acceptable cybersecurity posture. Can you afford to neglect it? Discover the future of IoT and 5G devices with the CNCF sandbox project – KubeArmor. Ensure device validation and trustworthiness for edge workloads. Learn more about it in our blog post.
Pillar 3: Network Segmentation and Access Control
It means dividing a larger network into smaller, more isolated groups or segments. Not only does that keep things organized but also protects against common cloud security issues. These include unauthorized access, lateral movement, data breaches, and malware propagation. Achieving compliance and regulatory requirements becomes manageable. It creates boundaries and stops different parts of the group from talking to each other. This border is important because it keeps your applications defended against surfacing attackers.
Access control is like having a special key to enter a secret room. It’s about controlling who can go where and do what. By doing this, only the right people or devices can enter certain parts of the group. This helps us keep our things safe and makes it harder for troublemakers to get in.
Popular network access and micro-segmentation techniques:
Different permissions to different people/devices. The basis of this is who they are, what they have, where they are, or when they want to enter. It’s like giving passes to different people depending on who they are and what they need. This helps us control access in a flexible and detailed way.
Micro-segmentation is dividing the group into even smaller groups. Each small group has its own rules and security measures. Imagine different rooms with different keys. Make nothing obvious! Abstract and protect.
Encrypting end-to-end traffic ciphers all messages going through the system. Only the people who know the code can understand the messages, which adds an extra layer of protection and makes it difficult for others to slip through.
If you want access control, encryption, keeping networks and data safe, and controlling who can go where network segmentation is the obvious choice. It makes it harder for bad people to do bad things. These are very important measures to keep your network infrastructure secure.
The best part is that AccuKnox offers Network Segmentation out of the box. We have automated analysis and least privilege network policies, leading to enhanced DevSecOps speed, control, and confidence.
Pillar 4: Infrastructure Protection
Infrastructure Protection, the fourth pillar of cloud security, is a powerful shield wall. It safeguards your systems, services, and workloads from unauthorized access and vulnerabilities. Think of it as building a fortress to protect your cloud-based operations.
Wondering how all this applies to your cloud-native application?
- Safeguarding systems and services. Picture your cloud infrastructure as a fortress. Infrastructure protection allows only authorized individuals to access organizational systems and services. It’s like having sturdy gates and checkpoints to keep intruders out. Who wants uninvited guests in their digital domain, right?
- Protecting against vulnerabilities. Vulnerabilities are like weak spots in your fortress walls that attackers can exploit. This identifies and fixes these weaknesses in place, making your cloud environment more resilient and secure.
- Securing workloads. Workloads are the applications, data, and processes running within your infrastructure. Infrastructure protection shields workloads from potential threats. Imagine a diligent security team that watches over and defends your valuable assets. Who doesn’t want a trusty guardian for their digital treasures?
In cybersecurity, a well-known saying is “Security is not a product, but a process.” Implementing robust infrastructure protection measures is a need. Part of that process is the safety and integrity of your cloud-based operations.
Amazon, Netflix, and Uber adopt cloud infrastructure protection for secure operations. Backed by robust security practices, they ensure integrity, confidentiality, and availability. These companies maintain compliance with industry standards as well.
Wish to fortify your cloud infrastructure and unleash the power of secure computing? It’s time to build a strong defense to keep your digital kingdom safe and sound. Let’s protect what’s yours!
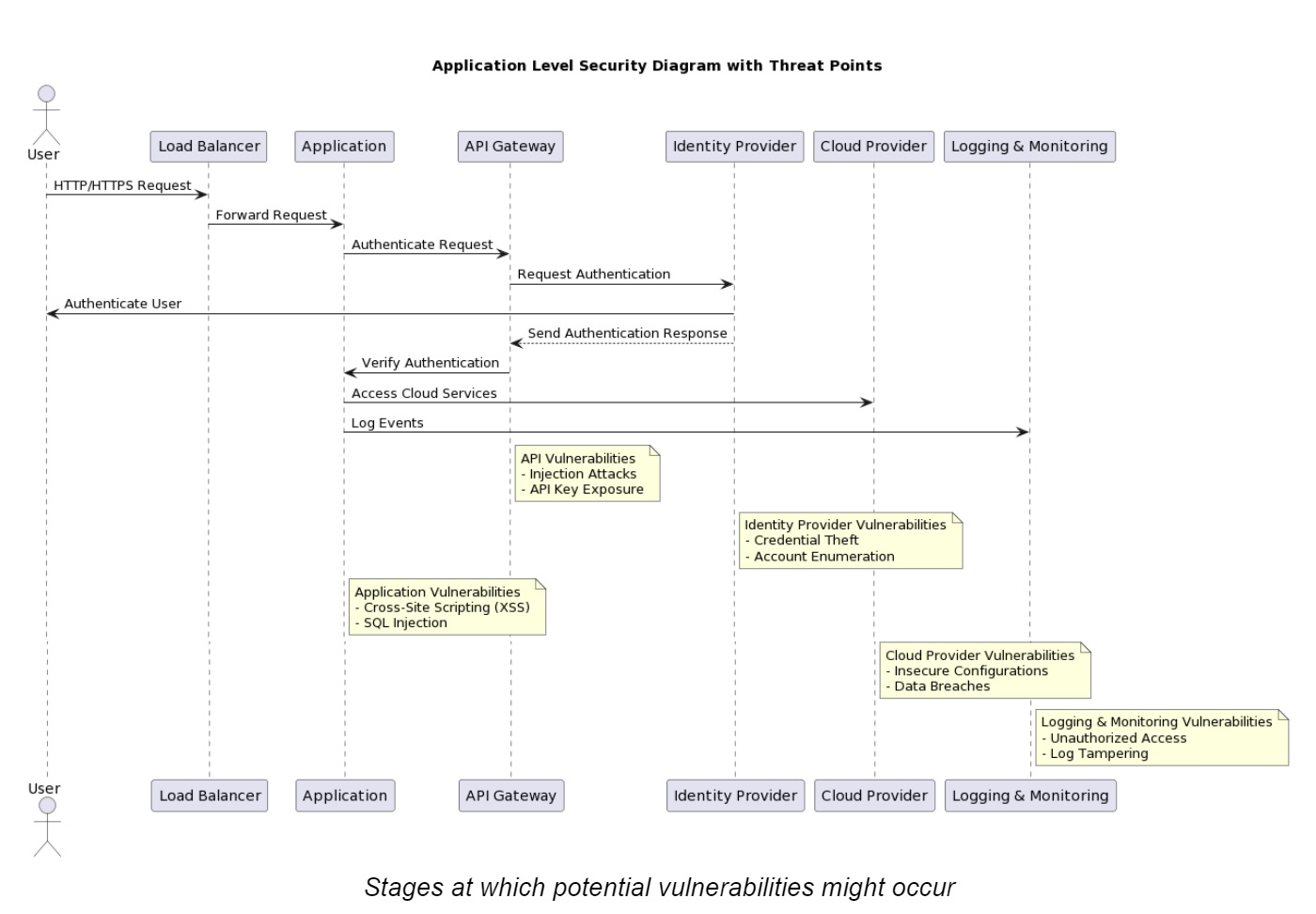
Pillar 5: Application Layer Security
Application layer security is all about protecting access and data within an application. Compare it to putting a strong lock on the front door of your house to keep out unwanted guests. Deploying cloud-native applications is getting easier day by day. This makes protecting against unauthorized access and tampering the need of the hour.
Tons of cloud applications run on platforms like Kubernetes. Cybercriminals have limitless opportunities to exploit vulnerabilities. That’s where application layer security comes in. It’s the extra layer of protection. With it, only the right people can access your applications, database, and tools.
Stages at which potential vulnerabilities might occur
Some strategies and tools that organizations use for application layer security:
- Authentication and Authorization. Cloud service providers offer services to control access to applications and their data. AWS/GCP has multi-factor authentication and role-based access control. Only authorized users can get in and only with 2x verification.
- Encryption. Encrypt data in transit and at rest to thwart unauthorized access. Nobody on the server can even peek at client-side information and messages. This raises client confidence. Nowadays, people only favor encrypted communication channels.
Application security is vital for cloud-native applications, 5G, and IoT. Professionals consider robust measures such as authentication, encryption, and continuous monitoring. Securing sensitive data builds trust, mitigates risks, and ensures integrity.
Doing this with AccuKnox is dead simple. Dealing with security measures will feel trivial with our dashboard, giving an organized bird’s-eye view of all the lurking threats.
Pillar 6: Data Access and Protection
Real-world example: Salesforce, a cloud-based CRM platform, enforces customer data security through robust access control. They also have encryption and cloud-native security practices in place. Salesforce protects customer information from unauthorized access or breaches.
| Strategy | Description |
| Categorize and Classify Data | Do it based on sensitivity and assign appropriate access controls. |
| Role-Based Access Control | Have strong access controls through user roles to restrict data access. |
| Data Encryption | Encrypt messages and data to ensure they are unreadable to unauthorized individuals. |
| Cloud-Native Security | Install security measures designed for cloud-based environments. |
| Zero-Trust Approach | Verify access requests before granting them, following a zero-trust security model. |
| Multi-Factor Authentication | Requires additional authentication factors, such as verification codes, for user access. |
| Data Integrity | Install measures to ensure the integrity of customer data, preventing unauthorized modifications. |
| Monitoring and Anomaly Detection | Detecting unusual or anomalous activities. Related to user, traffic, surge in downloads, etc. |
| Regular System Updates and Patching | Address known vulnerabilities and reduce occurrences of security risks. |
| Employee Education and Training | Educate and train employees on data security practices to promote a security-conscious culture. |
Pillar 7: Visibility and Analytics
Visibility and Analytics help you gain valuable insights by analyzing real-time communication data. You need to observe and analyze data across all Zero Trust components.
Due to modern trends and ease of use, most of us rely on cloud infrastructure and Kubernetes. Cloud-native apps offer flexibility, scalability, and agility. But the traditional security approach is no longer enough to protect your data.
A glimpse of the AccuKnox dashboard. Bird’s-eye view of analytics and reports.
The user and system behavior intertwine. Analyzing network traffic detects anomalies. Gain insights about usage and potential threats related to infrastructure and apps.
- Real-time communication analysis lets your security team examine user behavior. They can check authentication patterns, access requests, and data transfers. This ensures that only authorized users access the right resources. It helps spot compromised accounts and respond.
- Analyzing system behavior helps identify vulnerabilities and misconfigurations. It simplifies the detection of suspicious activities as it monitors interactions between containers and microservices.
- To detect and mitigate threats, analyze data from all Zero Trust components. This includes identity and access management systems, network security controls, and application logs. By aggregating and correlating this data, you get a complete security picture.
Real-world example: Google leverages Visibility and Analytics to enhance operations and security. This is across hundreds of services. They analyze network traffic to detect anomalies and ensure appropriate access controls. Google’s system behavior analysis helps identify vulnerabilities and address suspicious activities, thus strengthening their defenses.
So, Visibility and Analytics in Zero Trust handle monitoring and responding to threats. Analyzing real-time communication and observing data across components enhances your security. You protect your cloud-native apps and data from evolving cyber threats.
Pillar 8: Orchestration and Automation
Orchestration and automation are essential in Zero Trust. Why? Because they automate security and network processes. Both of these are interdependent.
Modern infrastructures deem that Kubernetes helps power operations and scale applications. But managing and securing these complex environments can be challenging. That’s where Orchestration comes in.
- Coordinates different security systems.
- Aligns functions and operations. Creates a unified approach to security across the organization.
- Reduces manual effort and speeds up security tasks. Automate routine processes and free up resources. Focus more on critical security activities.
Consistent enforcement of security policies is also recommended. Enforce compliance and security policies with automation! This leads to:
- Minimized human error and oversight.
- Efficient incident response and threat mitigation.
- Automated analysis of security alerts allows for rapid responses.
- Targeted actions to address potential security incidents.
- Consistent and up-to-date protection with automated security patches and software updates.
For cloud-native applications, integration is key. Automation enables the integration of security controls in development pipelines. Install security measures without slowing down development. In a nutshell, Orchestration and Automation streamline and automate security and network processes.
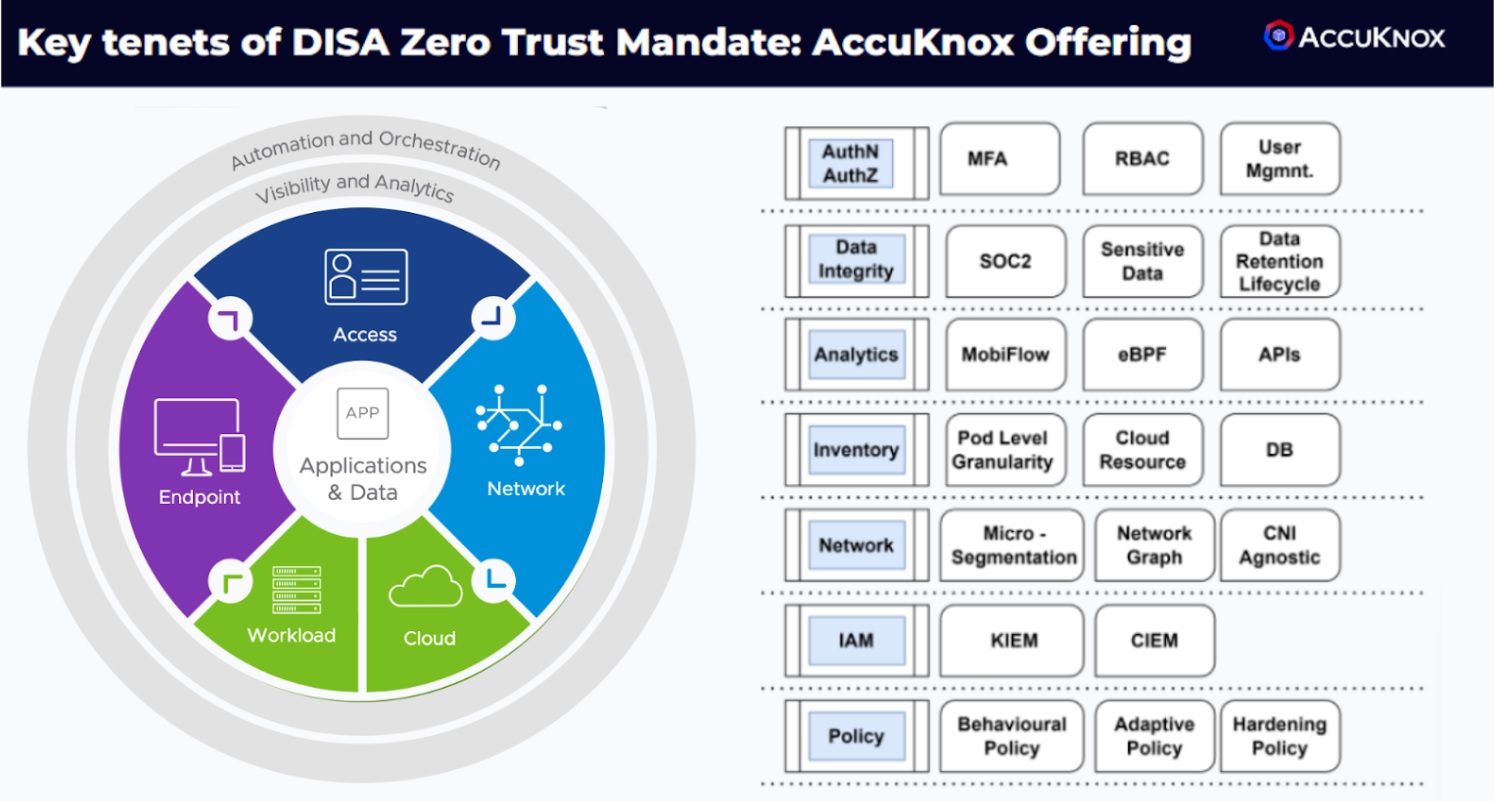
AccuKnox’s Approach
At AccuKnox, we provide targeted solutions and services. These align with the core principles of the Zero Trust Framework’s Eight Pillars. Our specific and targeted solutions aid enterprises to build a robust and secure cloud-native architecture. Here’s how AccuKnox contributes to each pillar:
We specialize in VMs, Bare Metals, Kubernetes, and so on. Our knowledge base has plenty of resources. They will help you strengthen your security posture, safeguard sensitive data, and respond to emerging threats. Trust AccuKnox to provide the security solutions you need in today’s cloud-centric environments.
Stay tuned as we continue to make advancements in IoT/Edge and 5G technologies! This infographic highlights our actionable recommendations and solutions for the same.
Read our article about ZT cloud security future to prepare for and embrace cloud-native security. Gain a comprehensive understanding of the benefits that outweigh the costs and challenges.
Conclusion
As a security professional, you have the power to strengthen your IT security. Safeguard digital assets with the eight pillars of the ZT model. Let us recap the points discussed above to help you achieve organizational security goals:
- Identify and Organize. The ZT playbook helps you identify and organize the necessary security tools. A structured approach helps security measures align with the zero-trust strategy.
- Add Appropriate Tools. Select a tool that performs well in each of the pillars above. Or better, choose AccuKnox since we take care of all this for you! Install the right security tools that meet your organization’s unique needs.
- Zero-trust framework gains popularity! The zero-trust model is becoming favored by enterprises due to its enhanced security advantages.
- Shift from perimeter-based model. Organizations are adopting the zero-trust model to address challenges posed by insider threats. The proliferation of IoT and edge devices is accelerating this. The perimeter-based model no longer suffices.
- Choose to untrust. The eight pillars treat everything as untrusted. This paranoid mindset leads to a comprehensive approach to security.
As a trusted partner in comprehensive security solutions, AccuKnox understands your security needs. Our team of experts can guide you in leveraging this model and ensure 100% compliance. Contact us today for a personalized consultation and let us help you achieve your security goals. We also recommend our presentation that covers all these facts in small bites and morsels.
Remember, security is an ongoing journey. Trust AccuKnox to be your ally in securing your digital assets.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed