Securing Java microservice workloads with AccuKnox Open-Source
Introduction Microservices are small, self-contained, ready to run applications. Each will have a specific well-defined task. All of them are grouped together to deliver all the functionalities of the big application. Java microservice is a software application written in the Java programming language and typically makes use of Java tools and frameworks. With Accuknox you […]
Reading Time: 3 minutes
Table of Contents
Introduction
Microservices are small, self-contained, ready to run applications. Each will have a specific well-defined task. All of them are grouped together to deliver all the functionalities of the big application.
Java microservice is a software application written in the Java programming language and typically makes use of Java tools and frameworks.
With Accuknox you can protect your Java microservices running on the cloud environment within a few clicks. You can also make use of open-source AccuKnox tools.
Prerequisites
Install open-source AccuKnox tools to your cloud environment.
Run the following script to install Daemonsets and Services
curl -s https://raw.githubusercontent.com/accuknox/tools/main/install.sh | bash
script to install Daemonsets and Services
For more details, see Quick Start – AccuKnox
or
Use Enterprise tier of the Accuknox product. For more details, see Agent Installation – AccuKnox
Deploy Sample Java/MySQL Web application in Kubernetes
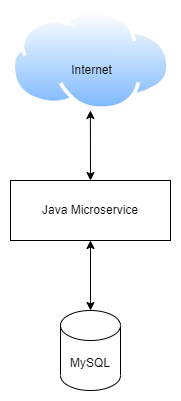
Here we are using a Java-MySQL demo application; Online Book Store as a workload. Online Book store consists of 2-tier microservices. The application is for selling books online, maintaining books selling history, adding and managing books, etc.
This application uses Java for Back-End and the database used is MySQL.
For more information see, the Deployment of the Sample OnlineBookStore application in GKE
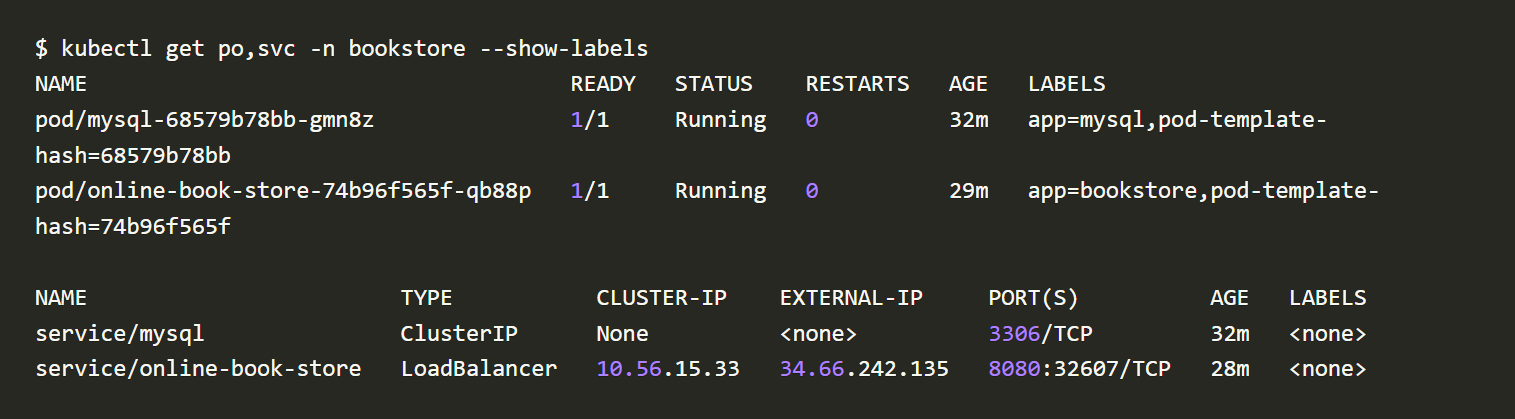
Check the status of the pod and service.
Pod and service template
Working with open-source AccuKnox tools
Auto-Discovered Policies
Auto-discovered policies are only available for K8s environments right now. For VM workloads it will be available soon. Accuknox policy auto-discovery engine leverages the pod visibility provided by KubeArmor and Cilium to auto-generate network and system policies.
Run the below script in the Kubernetes cluster to get Auto-Discovered Policies
curl -s https://raw.githubusercontent.com/accuknox/tools/main/get_discovered_yamls.sh | bash
Script-1
Script -2
cilium_policies.yaml contains all the auto-discovered cilium policies. cilium_policies.yaml
kubearmor_policies.yaml and kubearmor_policies_ext.yaml contains all the auto-discovered kubearmor policies. kubearmor_policies_ext.yaml kubearmor_policies.yaml
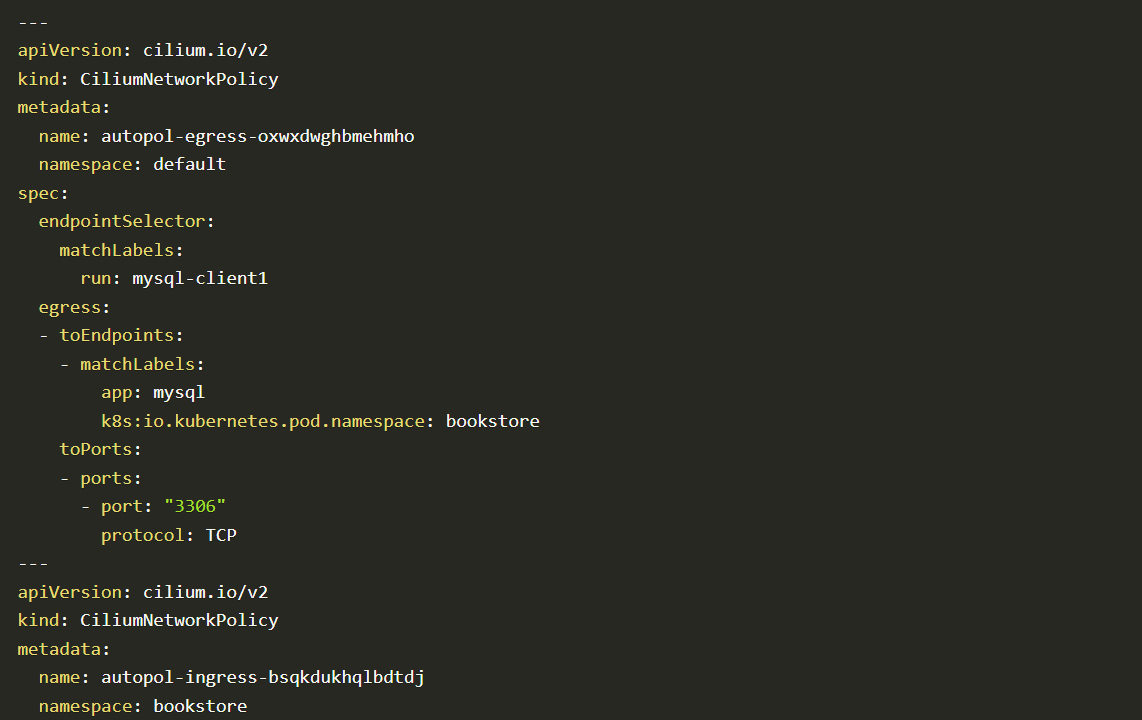
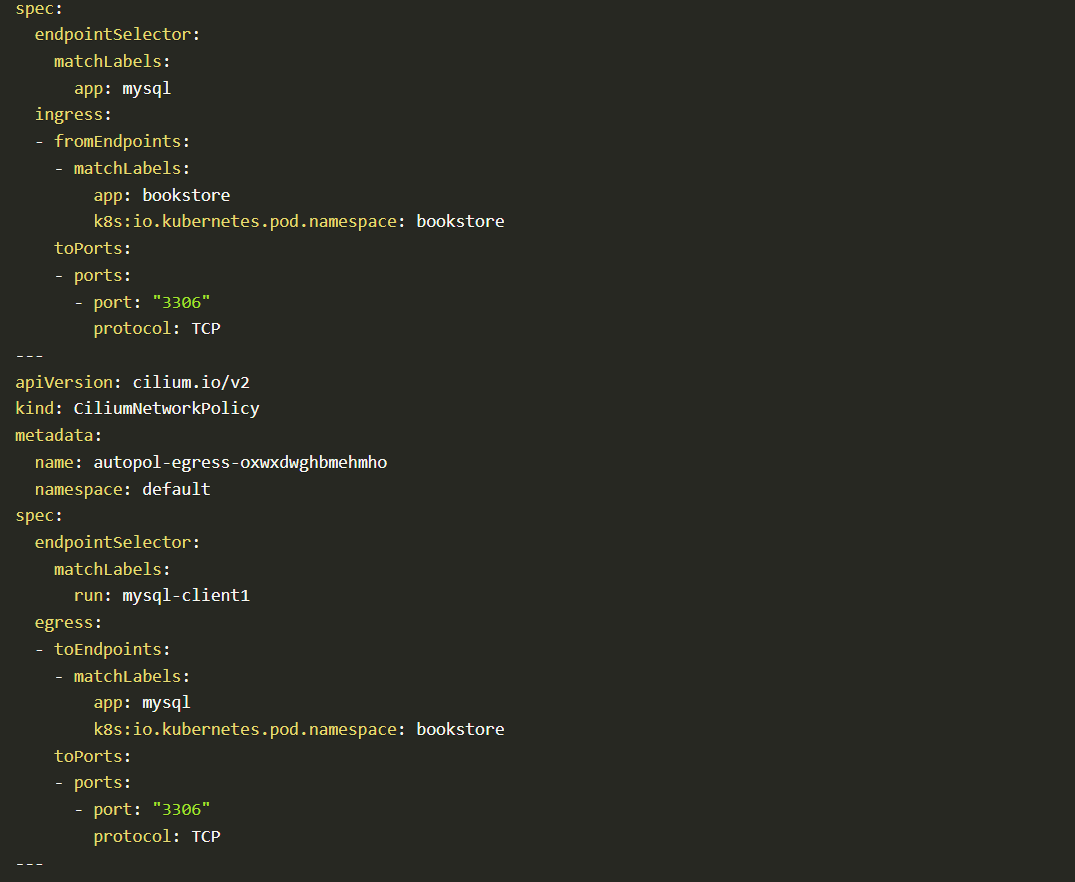
Let’s see all of the auto-discovered cilium policies we got related to the namespace: bookstore
Code block
Auto-discovered policies are generated based on the network flow of the application. By applying auto-discovered policies you can allow only minimum traffic that is necessary for its legitimate purpose. In that way, applications work with minimum attack surface.
Apply Auto-discovered Cilium Policies in Kubernetes:
kubectl apply -f cilium_policies.yaml
Apply Policies from Policy-templates Repo
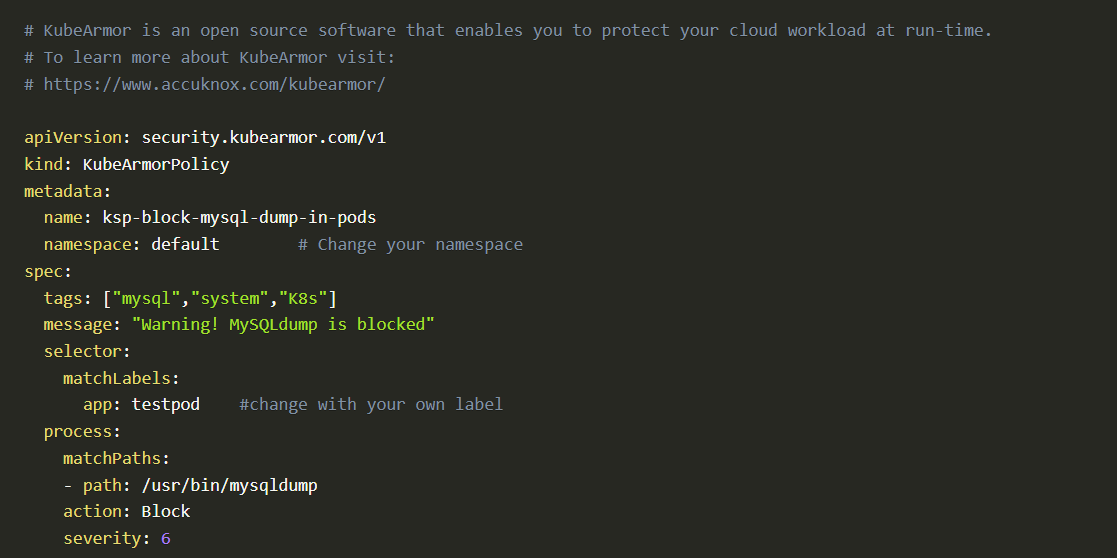
Accuknox’s policy templates is an open-source repo that also contains a wide range of attack prevention techniques as well as hardening techniques for your workloads.
The Policy-templates provides policies based on KubeArmor and Cilium policies for known CVEs and attack vectors, compliance frameworks such as PCI-DSS, MITRE, STIG, etc,
Repository link:
Within a few clicks, you can secure cloud workloads with policies.
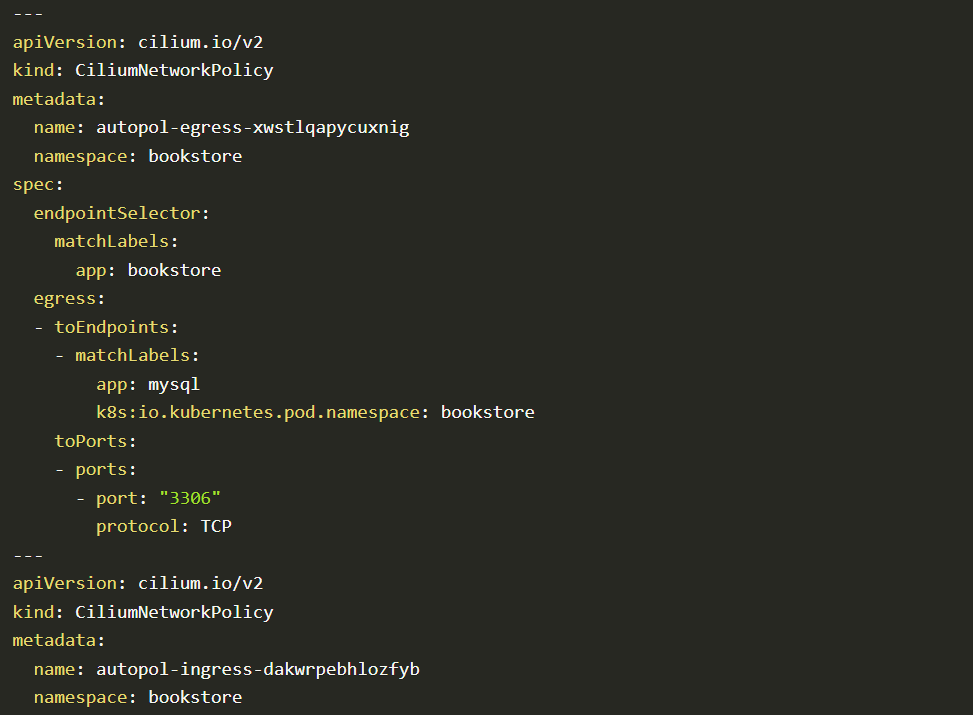
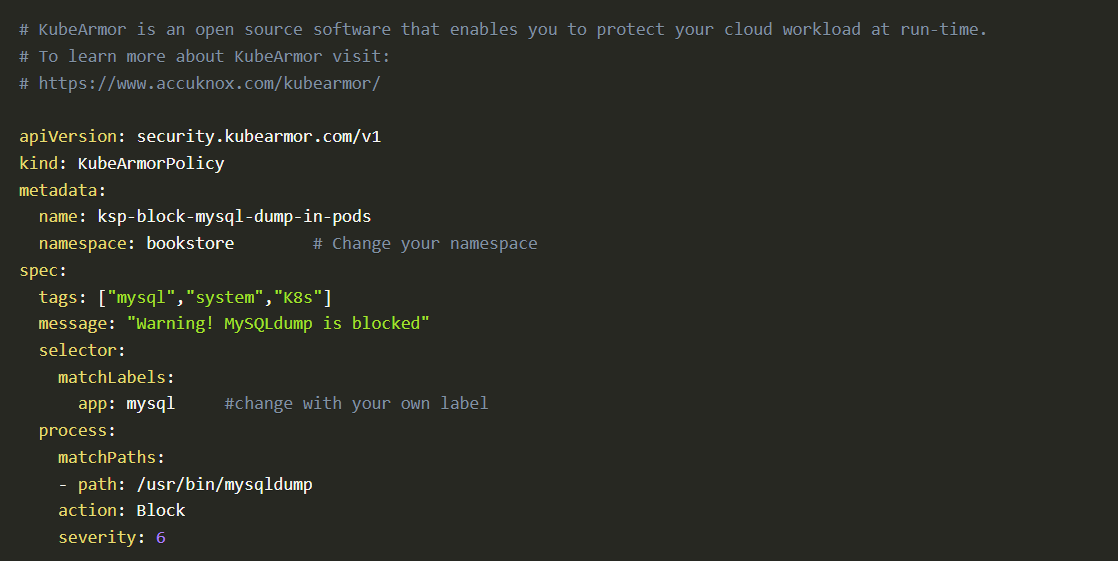
Go to Policy templates Github repository and selects any policy. Then copy policy raw contents and change namespace and matchLabels to the application pods namespace and labels
Policy templates Github
After changing namespace and matchLabels.
Code block 2
Note: Run kubectl get po -n bookstore --show-labels in the terminal to get the labels of the pods.
Conclusion
Using AccuKnox open-source tools, an organization can achieve cloud run-time security. With Accuknox policy enforcement engines, you can enforce policies to your cloud workloads while they are running.
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed