Identity is the New Perimeter
The perimeter is porous.. identity is the new perimeter. The last few years has seen a tectonic shift in the velocity and sophistication of software development and deployment models. The following depicts this shift. In this move to multi-cloud architectures, it has been established that we live in a “perimeter-less” world and the notion of […]
Reading Time: 3 minutes
Table of Contents
The perimeter is porous.. identity is the new perimeter.
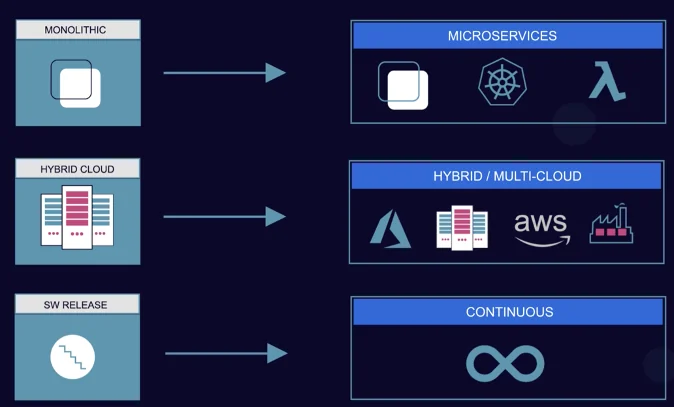
The last few years has seen a tectonic shift in the velocity and sophistication of software development and deployment models. The following
depicts this shift.
In this move to multi-cloud architectures, it has been established that we live in a “perimeter-less” world and the notion of “inside .. vs outside” is mostly irrelevant.
Furthermore, in the transition to containers, the assets are high dynamic, transient, elastic and ephemeral. Consequently, traditional IP-centric security mechanisms are not effective in securing container workloads. In this scenario, the only thing that is distinct, dynamic and secure is the identity, a unique cryptographic value assigned to a user or a service which serves as the unique key that is used for authentication and authorization. Hence the expression “Identity is the New Perimeter” Cloud Native leaders like Google, Netflix, Scytale (HPE) have pioneered SPIFFE (Secure Production Identity Framework For Everyone [1, 2]) which serves as a foundational mechanism for implementing this security paradigm.
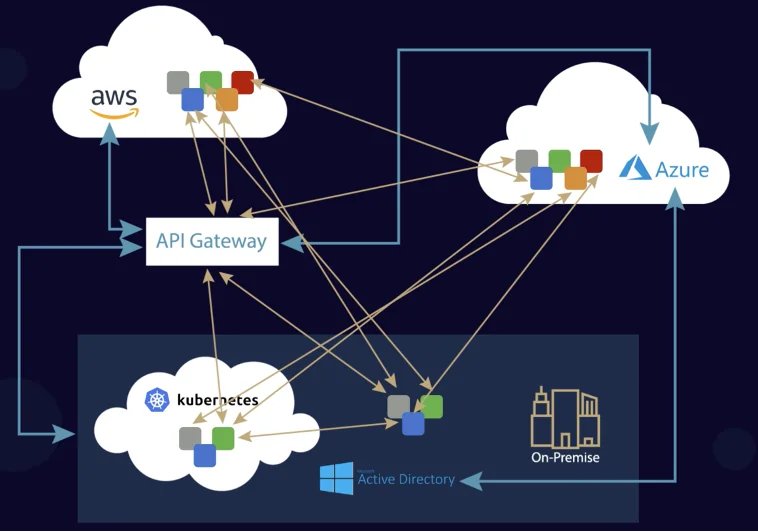
Establishing trust between entities (clients, servers) over untrusted channels (like internet) was made possible due to Passwords, Shared Secrets, PKI, HTTPS, TLS, etc. While these might seem extremely obvious in hindsight, these are incredibly revolutionary and path breaking by any standards. However, establishing trust in the world of micro-services due to the sheer size, scale and diversity and heterogeneity (across on-prem, private cloud, multiple public clouds, legacy platforms like VMs, modern platforms like micro-services, serverless, functions) makes this an extremely daunting task.
SPIFFE [3] is a standard spec defining a workload identifier
(SPIFFE ID) that can be encoded into a SPIFFE Verifiable Identity Document (SVID), either in the form of x509 or JWT. The spec also defines a few APIs that must be satisfied in order to register nodes and workloads, etc. SPIRE (SPIFFE Runtime Environment) is the reference implementation of the SPIRE spec.
SPIFFE and SPIRE helps you avoid the onerous process of setting up your own PKI infrastructure. The easiest way to think about SPIRE is fully automated high velocity PKI with dynamic credential rotation; and SPIFEE ID allows you to do cross authentication across heterogenous environments. Another common every day to conceptualize this [5] is to view SPIFFE and a unique identifier (say passport) and SPIRE verifies the passport.
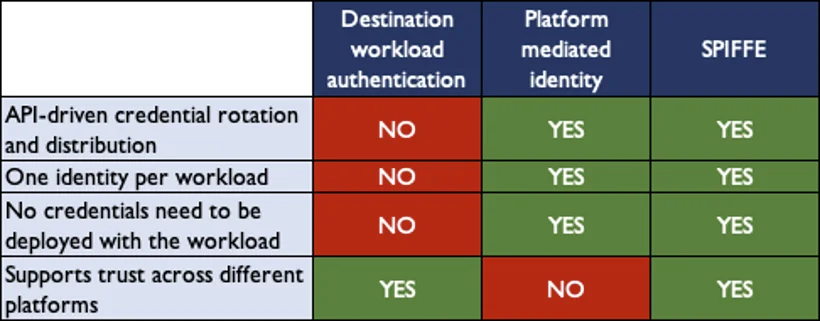
SPIFFE and SPIRE represent a quantum leap in Identity frameworks compared to anything in the past. The following table depicts its unique
advantages:
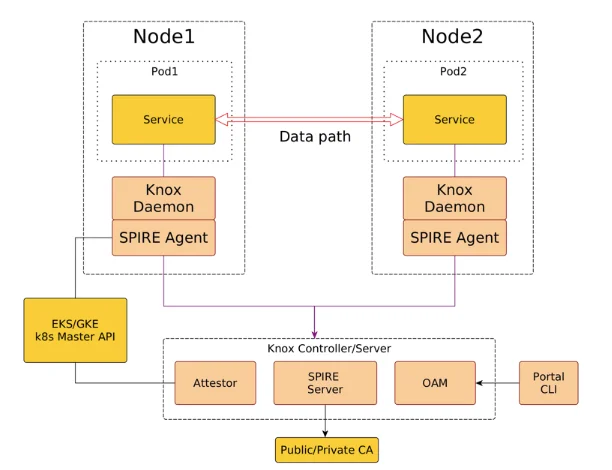
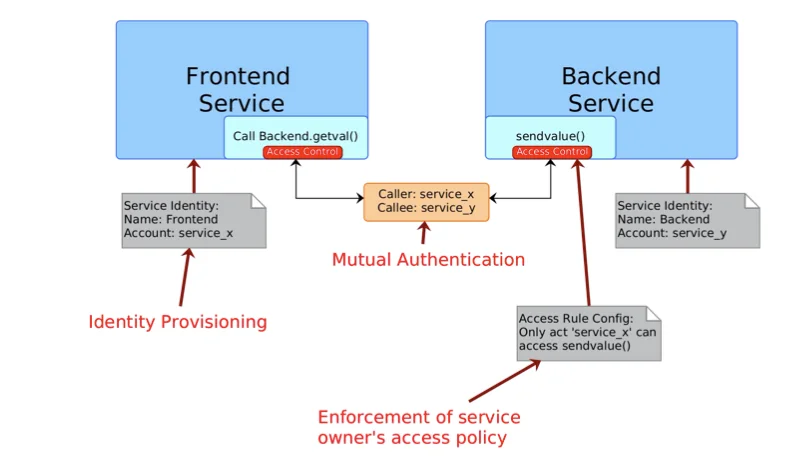
AccuKnox leverages the SPIFFE/SPIRE framework to implement a ZeroTrust Kubernetes Run-time Security Environment. The following depicts the high-level architecture.
In a Zero Trust world, there is a compelling belief [5] that Identity is a foundational element to establish trust across multiple foundational security platforms.
In summary, a strong Opensource based Identity Framework like SPIFFE/SPIRE is a critical foundational element to establish trust domains, attest workloads, establish policies, establish trust between organizations; all critical functions to establish a Zero Trust platform.
I am immensely thankful for my colleague, Rahul Jadhav’s input and contributions to this article.
Reference
1. Workload Identity – A SPIFFE Primer, Sunil Jacob
2. AWS IAM with SPIFFE & SPIRE
3. SPIFFE Project Introduction — Andrew Jessup and Emiliano Berenbaum
4. Five things you did not know you could do with SPIFFE and SPIRE — Andrew Jessup and Andres Vega
5. Building Zero Trust based Authentication in Healthcare with SPIRE
Now you can protect your workloads in minutes using AccuKnox</a >, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed