Implementing Runtime Security using KubeArmor
Accuknox is the only Cloud Workload Protection Platform (CWPP) that provides extensive protection to the application vector at runtime using KubeArmor Open source technology. Kubearmor is an open source project that was founded at Accuknox and it continues to be the core maintainer of the project. What is Kubearmor? KubeArmor is an open source application […]
Reading Time: 3 minutes
Table of Contents
Accuknox is the only Cloud Workload Protection Platform (CWPP) that provides extensive protection to the application vector at runtime using KubeArmor Open source technology. Kubearmor is an open source project that was founded at Accuknox and it continues to be the core maintainer of the project.
What is Kubearmor?
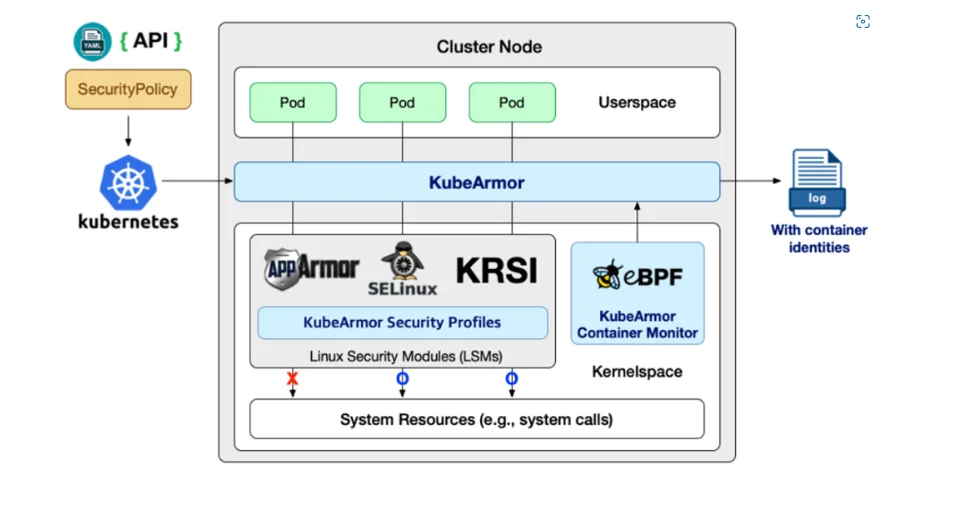
- KubeArmor is an open source application firewalling solution built for Cloud Native workloads.https://github.com/accuknox/KubeArmor
- KubeArmor uses Linux Security Modules (LSMs – AppArmor or SELinux to enforce application security), Syscall Filtering and soon eBPF LSMs to support hardening of a given process or container while interacting with the host, resources or other processes locally or across the network.
- Additionally, KubeArmor produces alert logs for policy violations that happen in containers by monitoring the operations of containers’ processes using its eBPF-based system monitor.
- KubeArmor allows operators to define security policies based on Kubernetes metadata and simply apply them into Kubernetes.
- Additionally KubeArmor supports virtual machine and baremetal workloads at this moment of time.
What can you do with KubeArmor and what is Runtime Application Security?
With KubeArmor, users can create an application firewall restrictions that allow us to restrict
- What kind of processes can be spawned from a given process
- What kind of network access is allowed
- What kind of file access is allowed
- What kinds of general system capabilities are permitted to the app.
Process Graph
Accuknox also automatically builds a full profile of the application at runtime a feature we call as the process graph. The process graph is a
runtime profile of the application segmented as application and network specific behaviors and is grouped by specific accesses over time.
The process graph provides full transparency into the application’s runtime behavior and easily allows users to select / create create policies to block specific unknown behaviors without quarantining the entire application.
Setting up KubeArmor
Setting up Kubearmor using Accuknox cloud platform typically requires installation of an agent in a Kubernetes environment and can be done using the installation guide given below (for GKE):
Deploy KubeArmor for GKE
https://raw.githubusercontent.com/kubearmor/KubeArmor/master/deployments/GKE/kubearmor.yaml
Deploy KubeArmor Host Policy
kubectl apply -f
LINK
Deploy KubeArmor Policy
kubectl apply -f
LINK
KubeArmor policy specification is provided on this link
Creating Runtime Application Security Policies on Accuknox
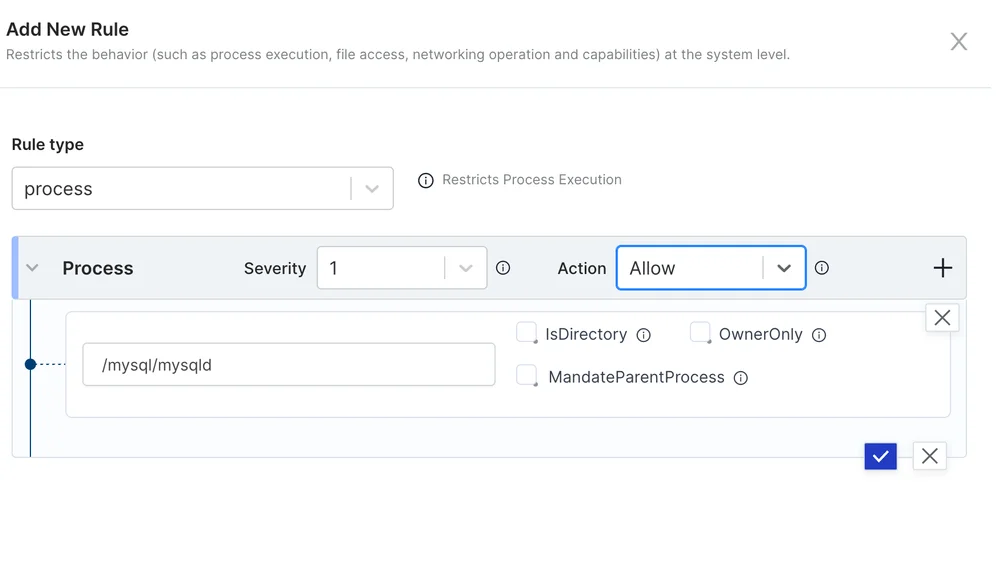
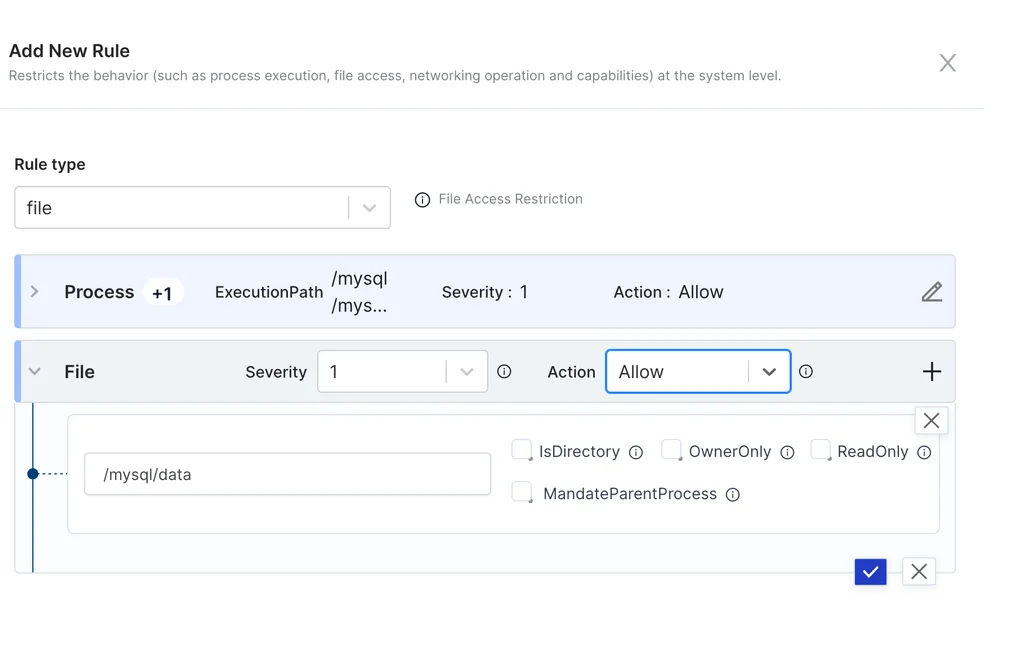
Creating application security policies can be done as Yaml or using the UI that the accuknox control plane provides. Users have several options for application security policies including the ability to restrict specific behaviors.
In the above examples, we have created a simple firewall that allows a specific container to be able to allow a certain path / process to run as well as provide access to a certain directory.
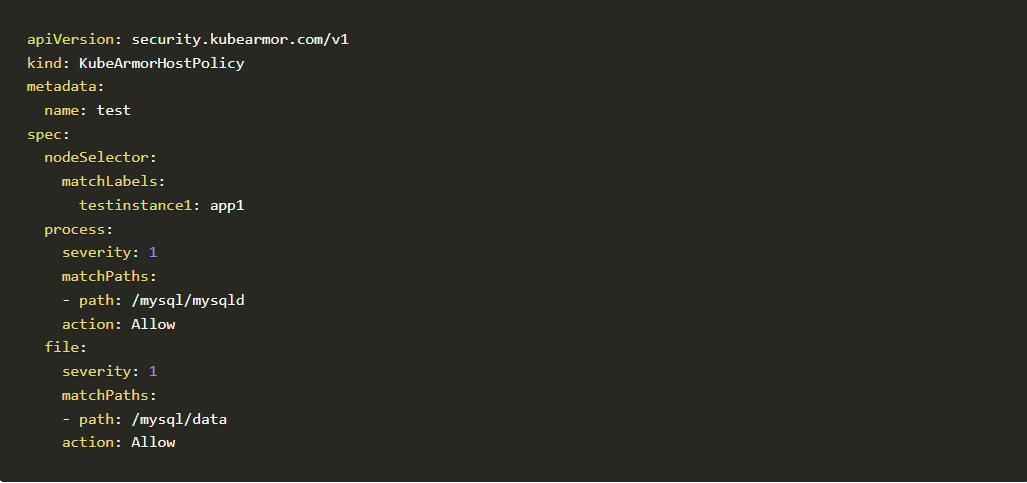
The policy as code generated for the the given policies as show below.
Application developers can shift this security policy to the left and make it as a part of the deployment artifacts.
Auto Discovery of KubeArmor Policies
Accuknox’s enterprise offering provides full support of auto-discovery of policies on cloud workloads. Click here to learn about the auto discovery of policies for KubeArmor.
Questions / Suggestions?
Please join:
Kubearmor Slack channel or the community on github to provide feedback on Kubearmor.
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed