McKinsey the Maven has spoken and…
“Security as code: The best (and maybe only) path to securing cloud applications” Welcome to Zero Trust Data Security!
Reading Time: 6 minutes
Table of Contents
“Security as code: The best (and maybe only) path to securing cloud applications”
Welcome to Zero Trust Data Security![
We have come to respect McKinsey’s pundit-like viewpoints in “board room” business settings. Insightful “boiler room” tech advice is the last thing I would have expected from this venerated consulting company. Consequently, I was very pleasantly surprised when I read this article from McKinsey. A number of core tenets outlined in this article concur with the architectural principles of AccuKnox Zero Trust Cloud Security Platform. The following is my attempt to provide a crisp and concise summary of the McKinsey article for folks who might not have access to the article and/or who might be looking for a “Cliff Notes” summary. Here it is…
1. Almost all breaches in the cloud stem from misconfiguration, rather than from attacks that compromise the underlying cloud infrastructure.
2. Traditional cybersecurity mechanisms were not designed to deliver security at the speed and agility that business leaders expect. Hence current business models require new security architectures and processes to protect their cloud workloads.
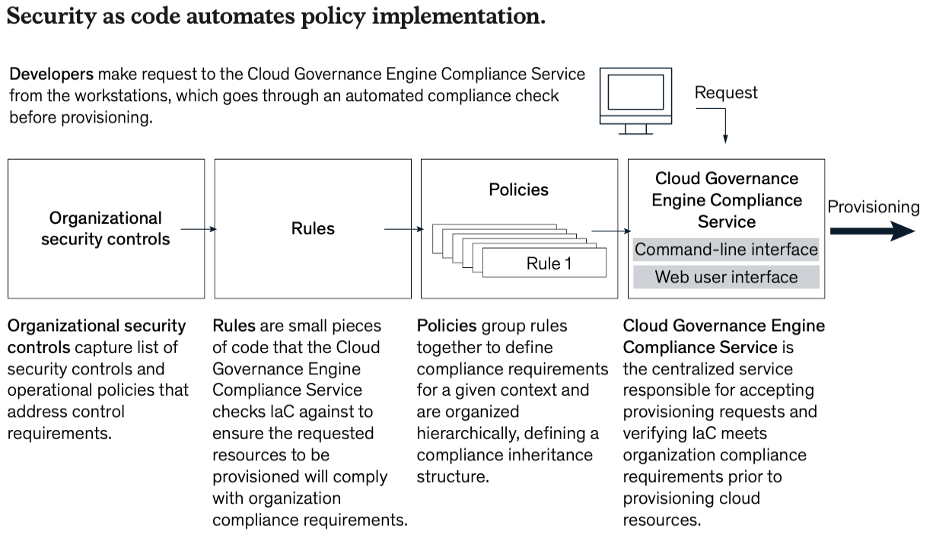
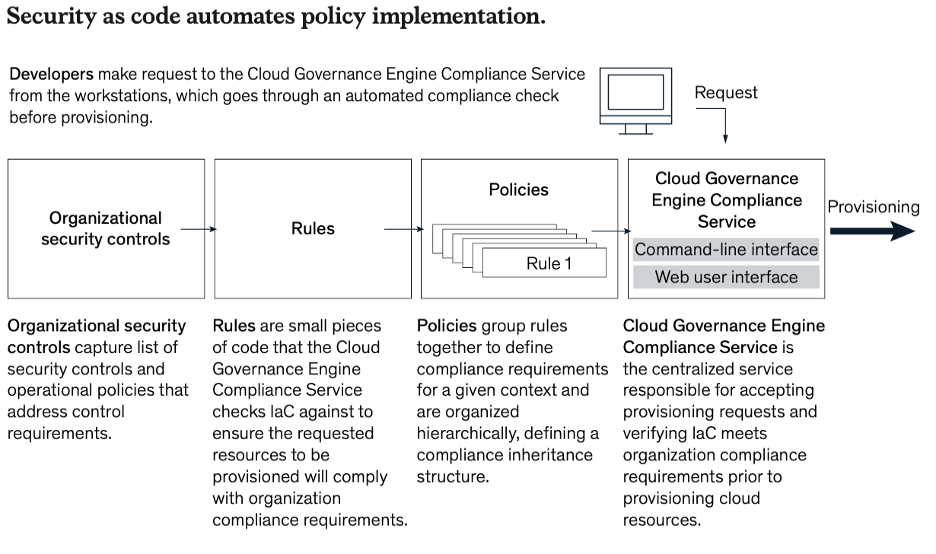
3. Infrastructure as code (IaC) has been highly effective at automating Cloud Systems deployment and streamline error-prone manual configurations. “Security as code” (SaC) is a natural progression of this concept and should be used for securing cloud workloads with speed and agility.
Security as Code
Following are the benefits of SaC:
1. Speed, Agility — Security moving at the speed of business
2. Risk Reduction — Cloud requires security controls to move with a workload throughout its entire life cycle. The only way to achieve this level of embedded security is through SaC.
3. SaC as a business enabler — Owing to these 2 reasons, SaC allows organizations to deliver fast time to market without compromising security.
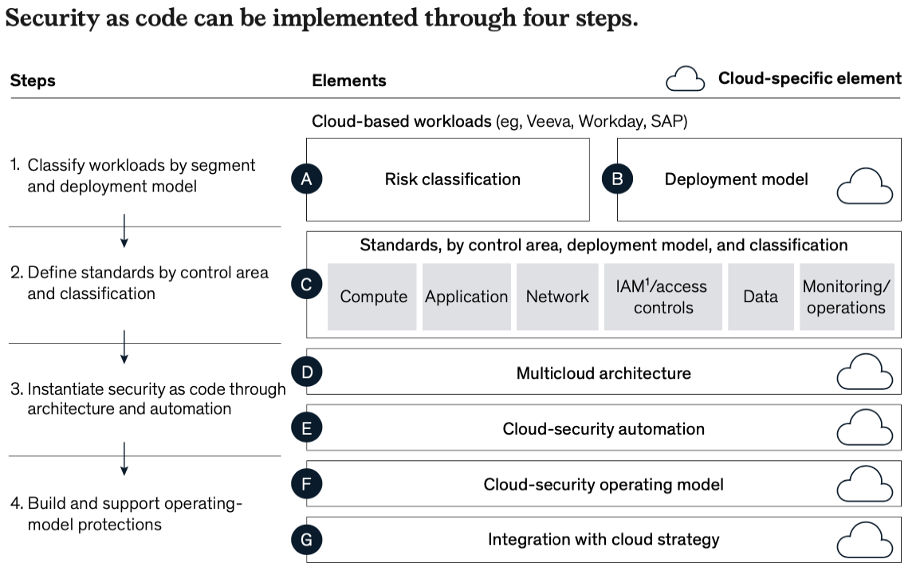
Organizations can implement SaC using the following structured approach:
1. Classify workloads according to sensitivity and criticality and then apply specific controls, based on workload risk and deployment type.
2. Define standards by control area and classification. Next step is to identify and write new policies to account for technologies that are not present on-premises. As an example: standards for container security, Kubernetes Security, API security, etc.
3. Finally, all polices — existing and new — must be written to a level of detail sufficient to enable them to be translated into code. This would be the place to invest in policy discovery, policy management tools.
4. Once policies have been defined, one would be able to make key architectural-design decisions and execute the right automation capabilities. As with policies, we recommend mapping these decisions to the organization’s priority control areas. Key questions about Private vs Public; Multi-cloud strategies need to be considered at this time.
4 Steps to SaC Implementation
Policy enforcement
Organizations need to invest in appropriate level of tooling their DevOps (Continuous Integration, Continuous Deployment) and “shift left” so that security is not an afterthought. This transformation leading to DevSecOps requires a close cooperation between Developers, DevOps, SRE and CloudOps teams. The security organization must move from a reactive, request-based model to one in which they engineer highly automated security products — for example, in identity and access management
or vulnerability management. This would require upgrading tools, processes, and core skills. This is outlined below:
Introducing Control Automation in the CI/CD Pipeline
Industry expert practitioners see immense value in implementing PaC (Policy As Code).
Mitigating human error:
“Security through code is all about repeatability. We implement automation and use of code for security purposes because it applies universal rigor throughout the organization. It solves the issue of human error that is the common denominator across cloud breaches.”
Stephen Schmidt, AWS CISO
“Over time, economies of scale will drive higher-level controls by default. The more we can raise the baseline of controls (for example, encrypted virtual machines, high-assurance container workloads, identity and access management, customer-managed encryption keys), the more customers can unlock all classes of workloads. Shortly, we’ll reach a tipping point when such enhanced security controls will be deployed across all services for all customers.”
Phil Venables, Google Cloud CISO
Balancing speed and risk:
“Security as code is all about giving our folks the freedom to do work while ensuring we have visibility into what they’re doing so there aren’t hidden behaviors or shadow IT. The security team must play an auditor role in accounts to see with specificity what is going on and get notified when changes are made.”
Stephen Schmidt, AWS CISO
“The automation capabilities and insights you gain across your inventory, services, configurations, and the ability to patch at scale are just not possible on-premises. We were also able to reduce our supplier footprint by 48 percent over two and a half years by leveraging integrated, holistic cloud solutions.”
Bret Arsenault, Microsoft CISO
“The pace of security enhancement and extent of security-feature additions to our products (our theme of secure products, not just security products) are accelerating. Many other cloud providers have made similar progress. This massive, global-scale competition to keep increasing security in tandem with agility and productivity is a benefit to all.
Phil Venables, Google Cloud CISO
Lifting and shifting security:
“The biggest problem we see is organizations trying to forklift security from on-premises to the cloud. Doing so misses so many opportunities that exist in cloud but not the data center.”
Stephen Schmidt, AWS CISO
“For some customers without sophisticated security teams, all they have to do is take every new security feature the cloud offers and keep them enabled. The most advanced customers requesting new features can drive benefit for all, and this — along with the visibility into and responsiveness to threats that we have as a hyperscale cloud provider — creates, in effect, a digital immune system for the whole customer base.” Phil Venables, Google Cloud CISO
“We can relate to enterprise customers; our security infrastructure and tools were not born in the cloud either. However, organizations cannot just take traditional, on-premises security processes and tools and apply them in a cloud environment. They simply won’t function at the necessary scale or speed. They must be transitioned for the environment they are operating in. It’s an investment, but the benefits, including cost savings overall, are significant.”
Bret Arsenault, Microsoft CISO
Automating containment:
“Some organizations can automatically remediate down to known good state, but most of the world is not there [and] should focus on automated containment instead. All components of an application need to have specific, up-to-date, and tested runbooks for containment in event of unexpected behavior. Bring in the business and application owners early. You don’t want to debate about when to pull the cord that isolates everything in the heat of battle.”
Stephen Schmidt, AWS CISO
In summary, PaC is the only viable solution for organizations to take advantage of the benefits of Cloud Computing, Kubernetes, and CI/CD to deliver business agility while ensuring prudent security controls. A structured approach along these lines will help organizations implement Security PaC discipline.
Author
Nat Natraj is the co-founder/CEO of AccuKnox. AccuKnox provides a Zero Trust Run-time Kubernetes Security platform. AccuKnox is built in partnership with SRI and is anchored on seminal inventions in the areas of: Container Security, Anomaly Detection and Data Provenance. AccuKnox can be deployed in Public and Private Cloud environments.
Natraj can be reached at [email protected] (@N_SiliconValley)
Visit www.accuknox.com or follow us on Twitter (@accuknox)
Now you can protect your workloads in minutes using AccuKnox, it is available to protect your Kubernetes and other cloud workloads using Kernel Native Primitives such as AppArmor, SELinux, and eBPF.
Let us know if you are seeking additional guidance in planning your cloud security program.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed