Achieving Zero Trust Cloud Security with Micro-Segmentation
This article explores the importance of network segmentation in achieving zero trust cloud environments. It also discusses how micro-segmentation can be used in AccuKnox CNAPP to create more granular control over network traffic.
Reading Time: 8 minutes
Table of Contents
Micro-Segmentation 101
Micro-segmentation is a network security strategy. It separates various workloads inside a data center from one another. In recent times, it has gained traction.
Why? Because it helps businesses to create more detailed zero trust security rules.
How? By limiting data flows across various workloads. Also, it enables the application of access control policies at the workload level.
💡TL;DR
- The complexity of multi-cloud architectures and the need to safeguard against online threats have put the spotlight on cloud security.
- CSPM tooling features include discovery, visibility, misconfiguration management, continuous threat detection, asset inventory, and testing cloud settings against best practices and compliance requirements.
- These solutions are suitable to deal with security issues in cloud infrastructures. Enterprises looking to enhance their cloud security procedures will benefit from adopting the CSPM toolset since it provides ready-made security solutions.
- 4 Steps to Improve Cloud Security Posture: Gain central access to all cloud assets, Locate information in context, understand the total cost of ownership (TCO), and focus only on cloud-native tools.
The purpose of micro-segmentation, like all network segmentation approaches, is to divide networks into isolated parts. This is done by establishing internal network boundaries. You get more insight into internal network traffic by monitoring traffic that crosses these borders. It also allows the application of direct access control and security policies to traffic that attempts to pass between segments.
✅ You are in the driver’s seat of your network security. Say yes to granular control!
Identity-aware policy discovery and micro-segmentation allow security SOCs and DevSecOps teams to logically divide workloads into discrete security segments and have more granular control over those segments. For instance, application tier segmentation, compliance, and so on.
How do Microservices Function?
Micro-segmentation is possible through software-defined networking (SDN). SDN implements network routing functionality in software. This separates the network data and control planes. Think of it as a digital bouncer, ensuring only authorized traffic can pass through.
SDN is useful for easy integration of access control lists and boundary definitions. Due to its lightweight and adaptable implementation strategies, it proves to be a top pick. Gone are the days of complex physical routing configurations. SDN eliminates the need for cumbersome network routes. Instead, switch over to a simplified implementation of micro-segmentation.
Network segmentation is a method of preventing lateral movement inside a cluster because Kubernetes is an open system by default.
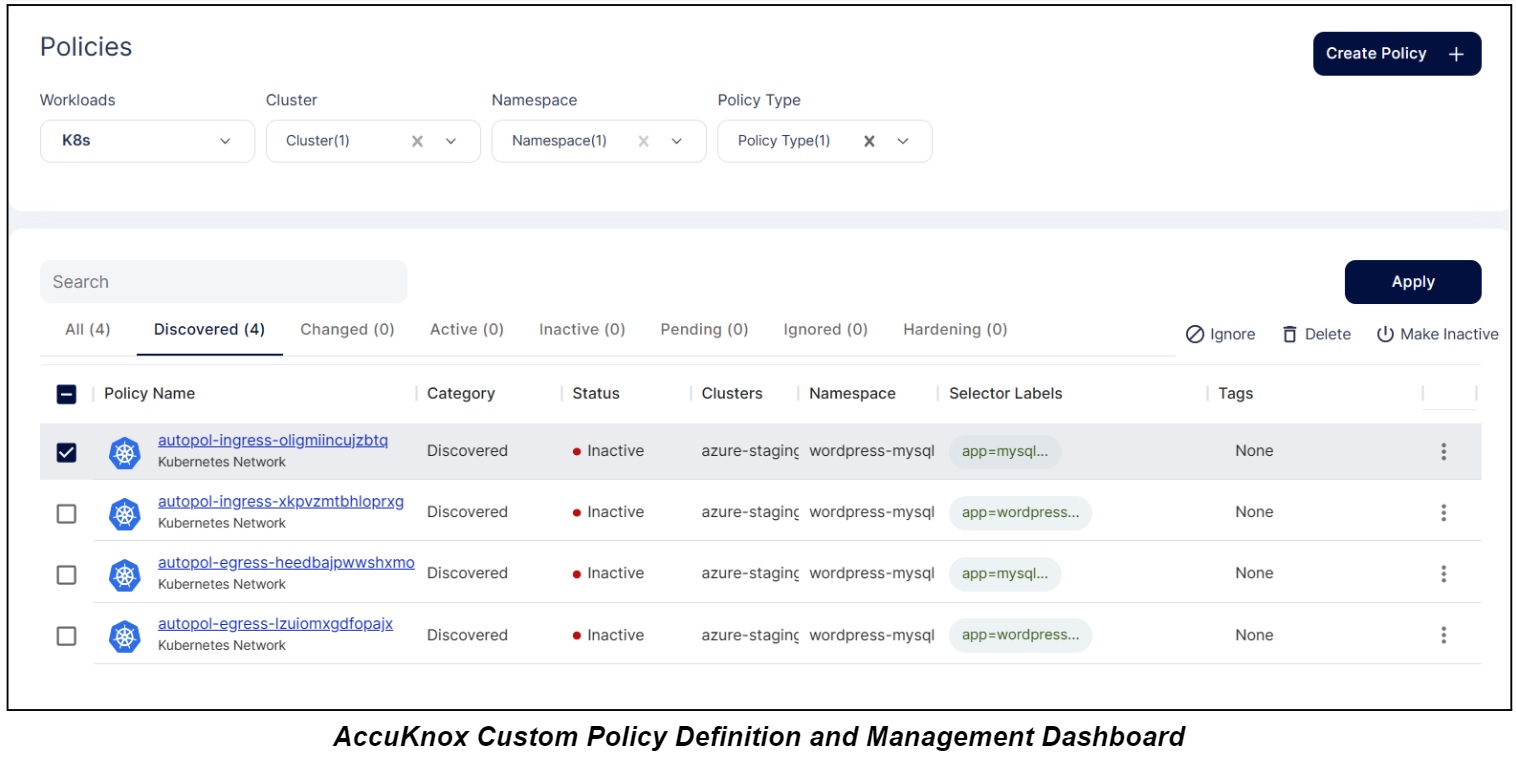
AccuKnox’s CWPP allows micro-segmentation at the most granularity level conceivable, which is also the smallest execution unit in Kubernetes, i.e. Pods. We will assist you in identifying process execution requests coming from a Pod, network connections it is attempting to establish internally and externally, and file systems it is accessing.
Based on the behavior of a specific pod and limiting the behavior to the expected flow of process/events/traffic, a least permissive security posture may be developed by defining whitelisting policies and auditing/denying everything else. Unless extra isolation is imposed, Kubernetes pods and services in various namespaces can still communicate with one another. It takes a lot of effort and is prone to errors to manually configure firewall and network policies.
⚡AccuKnox automatically examines the behavior of apps and develops least privilege network restrictions that are then applied by already-existing, high-performance Linux security modules. The network regulations are moved along with the application as code, dramatically enhancing DevSecOps speed, control, and confidence.
Cloud Security Issues: How Micro-segmentation Can Assist
Visibility and control are critical in cloud security. You must have spotted cases where entire databases, microservices, and APIs suffer outages without total data visibility, causing heaving losses. Let’s look at some common cloud security challenges where microservices might help:
- Cyberattacks and data loss. Protect your sensitive information from threats that could result in expensive losses.
- Misconfiguration of Security Measures. A minor error in establishing security measures might expose vulnerabilities. Keep an eye on things and double-check your settings.
- Illegal Access. Keep unwelcome visitors at bay! Protect unauthorized individuals from accessing your cloud resources and sensitive data.
- Denial of Service Attacks. Prepare for a flood of traffic that might impair your cloud services. Develop strong defenses to repel this onslaught.
- Malicious Insider Threat. The Enemy Within! Safeguard your organization against possible dangers posed by dangerous insiders. Put in place stringent access controls and monitoring mechanisms.
- Account Hijack. Beware of cyber criminals trying to take over your cloud accounts. Strengthen your authentication processes to thwart unauthorized access attempts.
- Insecure Interfaces and APIs. Micro-segmentation ensures interfaces and APIs are secure. Decoupling is a great way to go about this. Weak vulnerabilities in these entry points can allow attackers to exploit them.
Micro-segmentation is pivotal for achieving Zero Trust network security, according to 88% of cybersecurity leaders, and it is more practical and effective than alternatives, according to 92% of them. But 35% of cybersecurity experts still encounter difficulties like staffing shortages, financial limitations, and scheduling conflicts. The increase in cyberattacks, expanding attack surfaces, concern over vulnerability, and vulnerabilities in legacy devices are the primary drivers behind the implementation of microsegmentation. Real-time threat management, secure remote access, and a ransomware kill switch are key factors to look for in a micro-segmentation solution.
Get to Know the Difference: Micro-Segmentation vs. Macro-Segmentation
Macro-segmentation
Just another word for classical network segmentation. Useful to analyze and safeguard traffic entering and departing the data center. This traffic channeling is in a north-south manner. Comparable to constructing walls inside your network to divide groups of systems. A macro-segmentation strategy divides a network into groups of systems using virtual local area networks (VLANs) and firewalls. This allows visibility into and installs access control policies amongst segregated network parts. Imagine having different security personnel for each room in your home to ensure that nothing goes undetected.
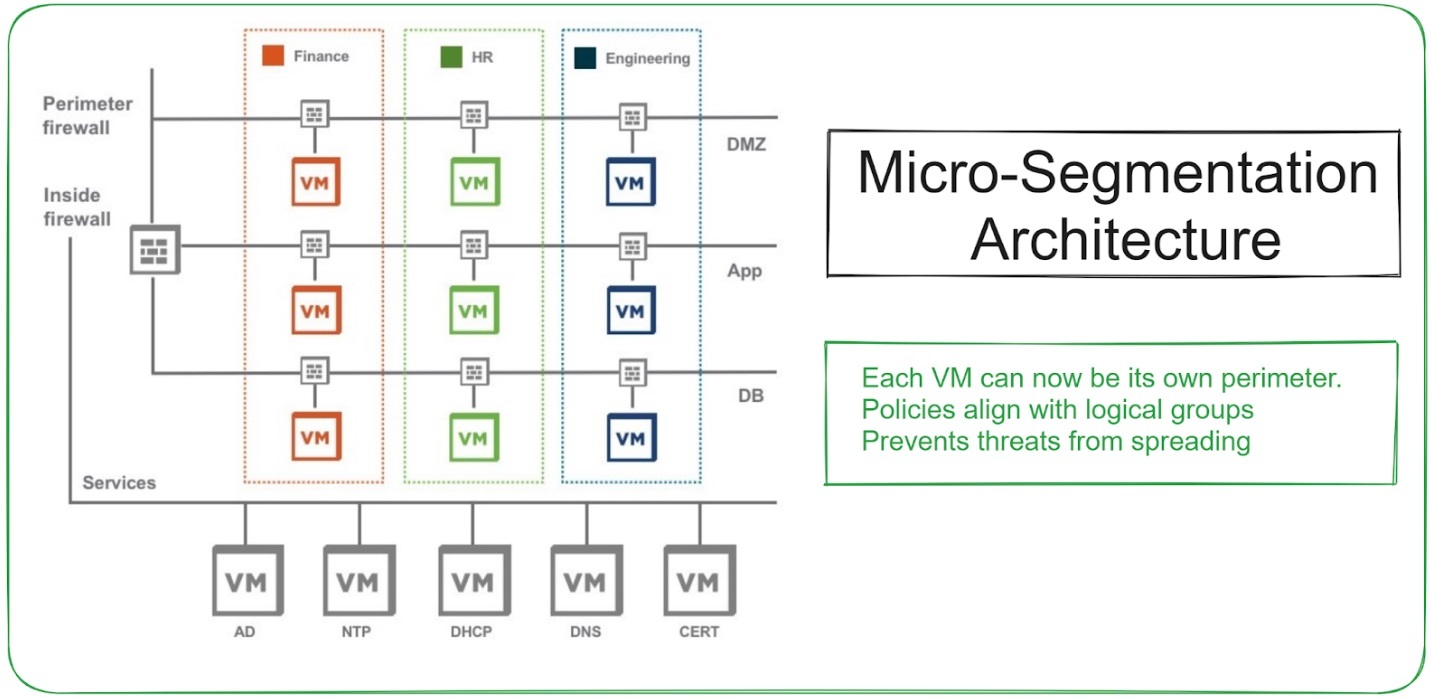
Micro-segmentation
Achieve network segmentation at a much finer level. You create a distinct bubble around each job to increase visibility and control. Micro-segmentation separates individual tasks rather than segmenting groups of systems. This gives the company far greater visibility and granular control over network traffic that travels laterally across workloads within the data center. Consider working with X-ray vision for your network. Detects any suspicious activity with pinpoint accuracy. Micro-segmentation is based on the “least privilege” principle across workloads and environments. This means you get a much more effective defense posture than traditional network-layer controls would allow.
So, which method is best for you? Depends on your security requirements and desired level of control. Macro-segmentation offers a larger perspective, whilst micro-segmentation enables granular control. To make an educated decision, consider the complexity and security needs of your network.
🔦You are in control of your network security whether you pick micro-segmentation or macro-segmentation. So go ahead and harden your network, and rest easy knowing that your data is secure thanks to the power of segmentation.
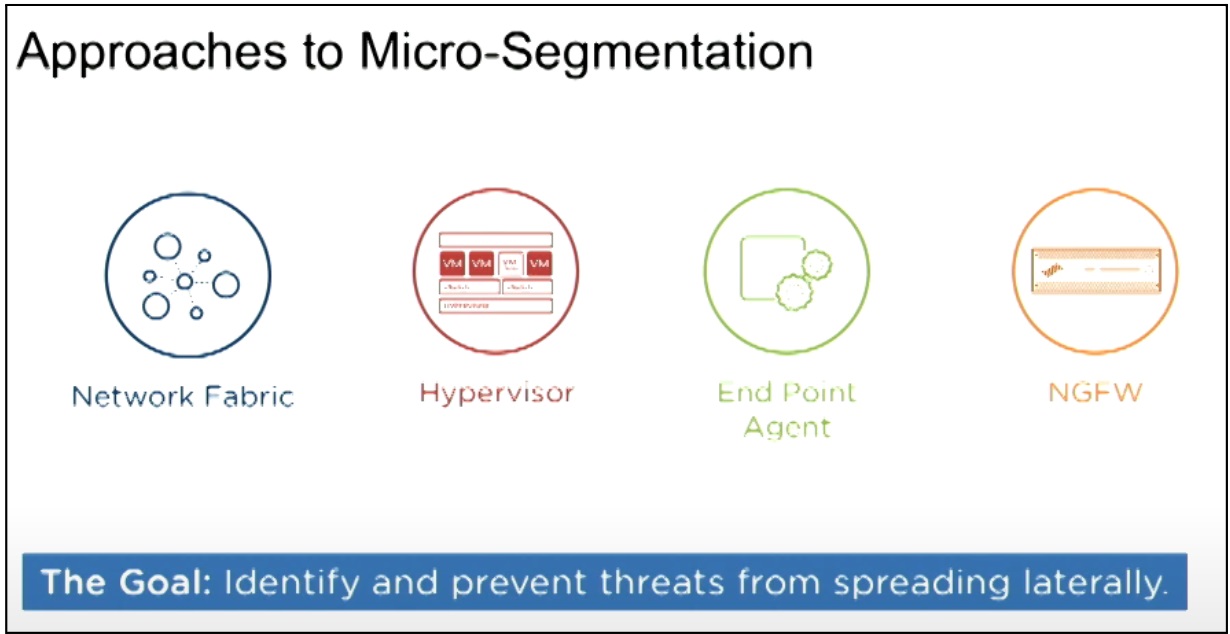
Types of Micro-segmentation – Review Approaches and Options
When it comes to micro-segmentation security, there are three options. Let us break things out in simple terms.
- Network-based: Regulate who and what may access various areas of your network. It is simple to administer and takes little administrative work. Note that managing security restrictions becomes difficult and costly if your segments get too vast.
- Hypervisor-based: A software or hardware used to run virtual computers. Allows for complete tracking and management of the network traffic. This is a huge win. Because now you can use existing firewalls and transfer security settings between hypervisors. Not suitable for cloud installations or certain types of applications.
- Host-based: With this technique, agents are placed on each endpoint to provide visibility and control over data, processes, software, and communications. A central manager controls everything, keeping an eye out for any flaws. This agent-based installation does not guarantee Zero Trust. It is also time-consuming for both administrators and end users to get it installed on every node on the network/host.
All the discussed strategies depend on organizational needs and circumstances. Whether you choose network-based micro-segmentation, hypervisor-based micro-segmentation, or host-based micro-segmentation, you’re taking a significant step toward improving network security.On a quick side note, you might also be interested in how to achieve Identity-based micro-segmentation using JWT-tokens.
Ways in which Micro-segmentation Improves Cloud Security
To lower cyber risks, every cloud instance or service needs to be isolated. Regardless of whether a business uses a hybrid/private/public cloud infrastructure. Micro-segmentation cloud security has a proven track record of reducing cloud asset damages and compromised systems. Stick to the below-listed industry best practices.
Pinpoint Assets
Recognize the assets that are present in your cloud environment, to begin with. Use data synchronization micro-segmentation techniques with your cloud management platform. This aids in grouping assets according to their features or functions.
Applications and Services as Models
Examine your assets and how they interact in more detail. You choose where to apply segmentation thanks to the detailed visibility provided by micro-segmentation. This guarantees that you comprehend exactly how various elements relate to one another.
Apply for fine-grained protection
Fine-tuning your control over cloud traffic using micro-segmentation is dead simple. Intrusion prevention/detection systems (IPS/IDS), application control, and URL filtering measures are a few of the security policies that need tailoring as per organizational requirements.
Improve Policies
For the most security, review and optimize policies. Micro-segmentation gives you information about how your assets are currently performing, assisting you in locating areas that need tuning. Maintain your security edge by fine-tuning your policies.
Observe and Adjust
There is no “set it and forget it” approach to micro-segmentation. It needs constant observation and improvement. Micro-segmentation monitors changes and modifies traffic flow as your cloud environment changes. By doing this, you remain certain that acquired assets are protected. Moreover, the architecture matches your organization’s requirements.
☁️ Avail AccuKnox’s cutting-edge micro-segmentation packaged with our Cloud Workload Protection Platform (CWPP). Rid yourself of security debt through robust network segmentation capabilities. AccuKnox offers micro-segmentation for granular network traffic control, ensuring individual workloads are protected and preventing unauthorized lateral movement within the network. Convinced? Quick start by referring to our docs.
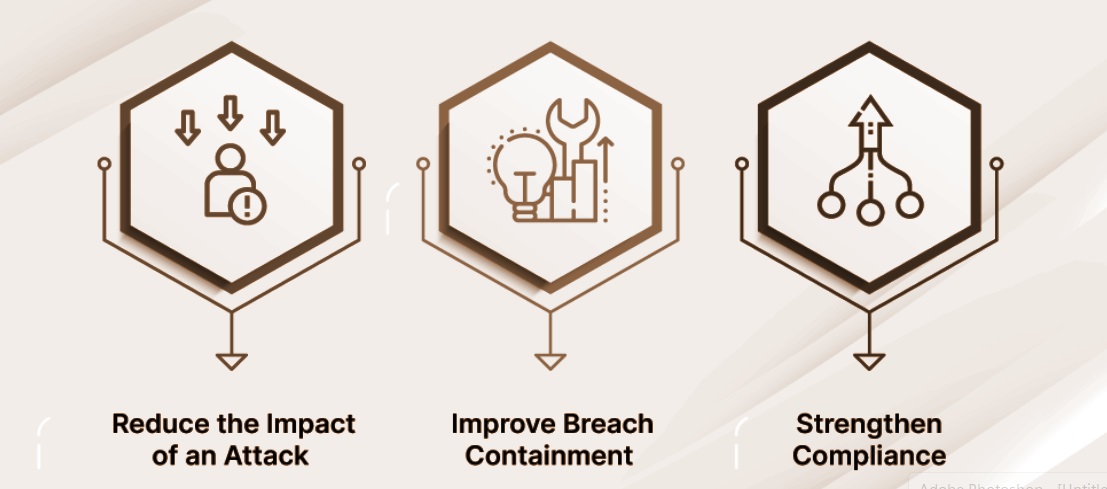
The takeaway is that micro-segmentation proves useful in cloud security strategy, precision asset protection, swift threat response, and continuous refinement.
Advantages of micro-segmentation
- Greater visibility. Monitor and manage data transfers between workloads to find and handle cybersecurity incidents.
- Limiting attacker lateral movement. Makes it tough for attackers to switch between compromised workloads. Cushion the impact of attacks and data breaches.
- Improved application comprehension. Discover how data moves between workloads, spot anomalies, and spot potential threats.
- Increased effectiveness. Network micro-segmentation renders irrelevant the need for distinct firewall devices and access control lists.
- Centralized policy management. Simplify overhead involved in monitoring and updating rules. Also, easy adjusting to network changes and online threats.
According to the Statista Survey regarding micro-segmentation adoption, 66% of respondents said micro-segmentation advanced their company’s threat detection and response.On the same note, 60% of security and IT professionals think security is the biggest obstacle to cloud migration. Microsegmentation is currently being used by 83% of cybersecurity leaders, while legacy technology protection was the last topic mentioned. Time, network complexity, and a lack of personnel are additional obstacles. Internal attacks account for over 43% of breaches and are undetectable by conventional firewalls. Data breaches are thought to cause an annual loss of about $24 billion Comment end .
Implementing Zero Trust with Micro-segmentation
In today’s shifting cybersecurity world, we encourage you to implement a zero trust security strategy to reduce your organization’s cyber risk and exposure to attacks. Zero trust is restricting access to systems and resources to only what is required. Following network authentication, each request is checked against established access control policies and either granted or denied. Access to apps is allowed based on business logic and is limited to minimal essential permissions.
Enforcing zero trust security necessitates the use of micro-segmentation. Micro-segmentation creates boundaries between workloads, allowing for stringent access control enforcement. This decreases network system susceptibility. Also, it limits an attacker’s access during a successful attack.
A cloud-based micro-segmentation solution is becoming important as enterprises transfer their computer infrastructure to private clouds.
Conclusion
Finally, micro-segmentation is an integral ingredient of the shared responsibility security paradigm. It improves the efficacy of network-wide security measures. Understanding this approach is critical for initiatives involving secure cloud and digital transformation.
The client, not the cloud provider, handles safeguarding virtual machines, containers, and code in serverless PaaS. The best area for security visibility and management is within the workload itself.
Integrating micro-segmentation alongside suitable procedures and policies. Assure your stakeholders and customers with the highest levels of security. Profit off a secure environment beyond the typical and deprecated perimeter.
Must read articles
- Zero Trust (ZT) – The Future of Cloud Security
- Zero Trust (ZT) Architecture, Framework and Model
- Cloud Security Governance, Risk and Compliance (GRC)
- How to Pick the Right CNAPP (Cloud Native Application Protection Platform) Vendor
- What is Driving the Need for CSPM (Cloud Security Posture Management)
- Agent vs Agentless Multi Cloud Security
Zero Day Attacks cost $3.9M on average

4+
Marketplace Listings
7+
Regions
33+
Compliance Coverage
37+
Integrations Support

Stop attacks before they happen!
According to the latest IBM cloud attack report - Each cloud attack on an average costs $3.92M
Total Exposed Attacks in 2024 Costed